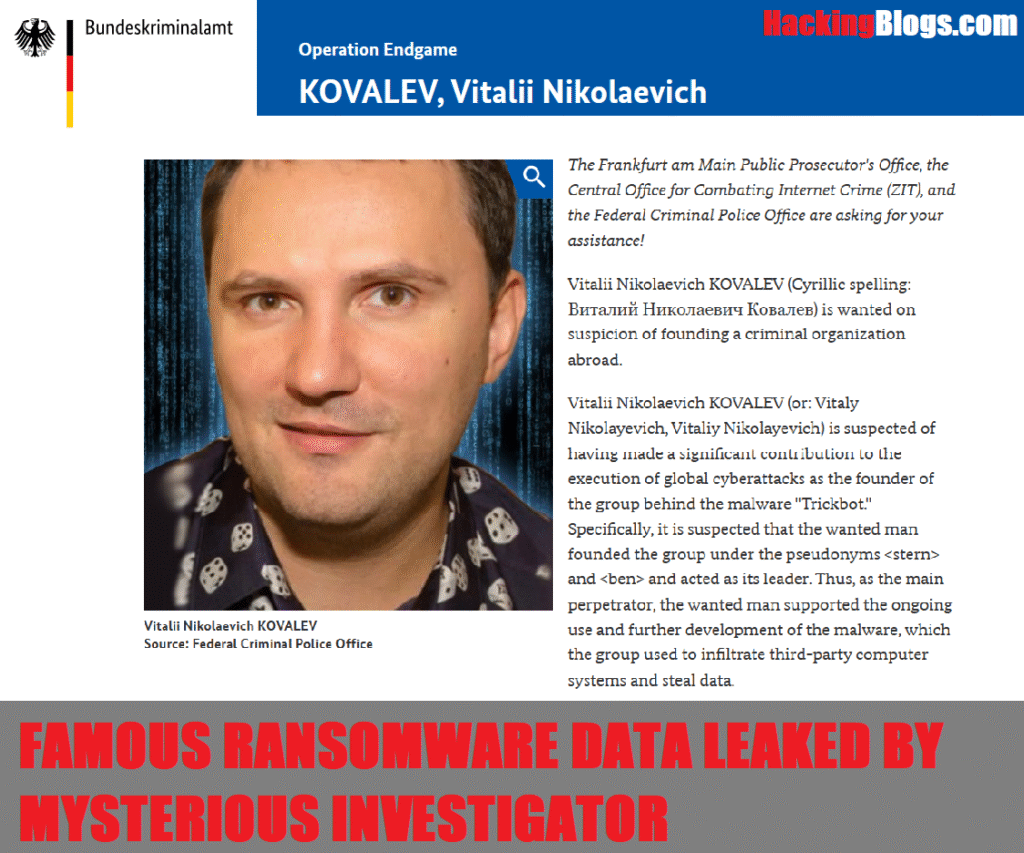
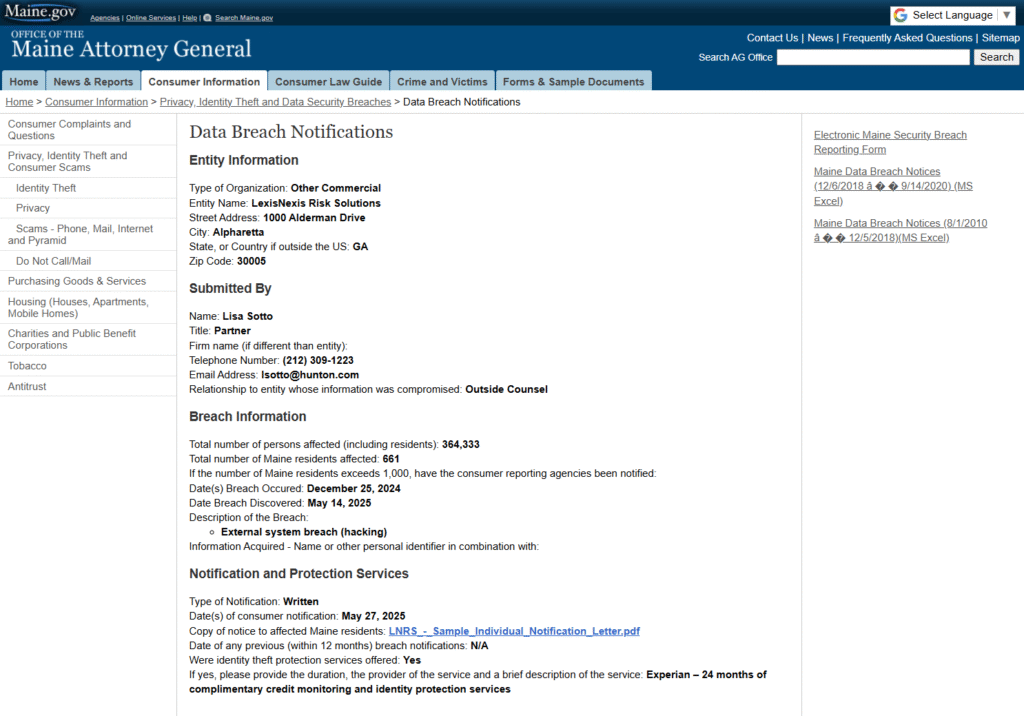
Think adult videos are safe? RatOn malware is using them to hack phones, steal banking info, and wipe out crypto
Hi there, this is Dipanshu. Today, I’m discussing a new malware known as RatOn malware, which is a major cybersecurity issue that has been making headlines. Fundamentally, RatOn malwares a Remote Access Trojan (RAT), which is a type of weapon that hackers frequently employ since it allows them to fully manage a victim’s device remotely. […]