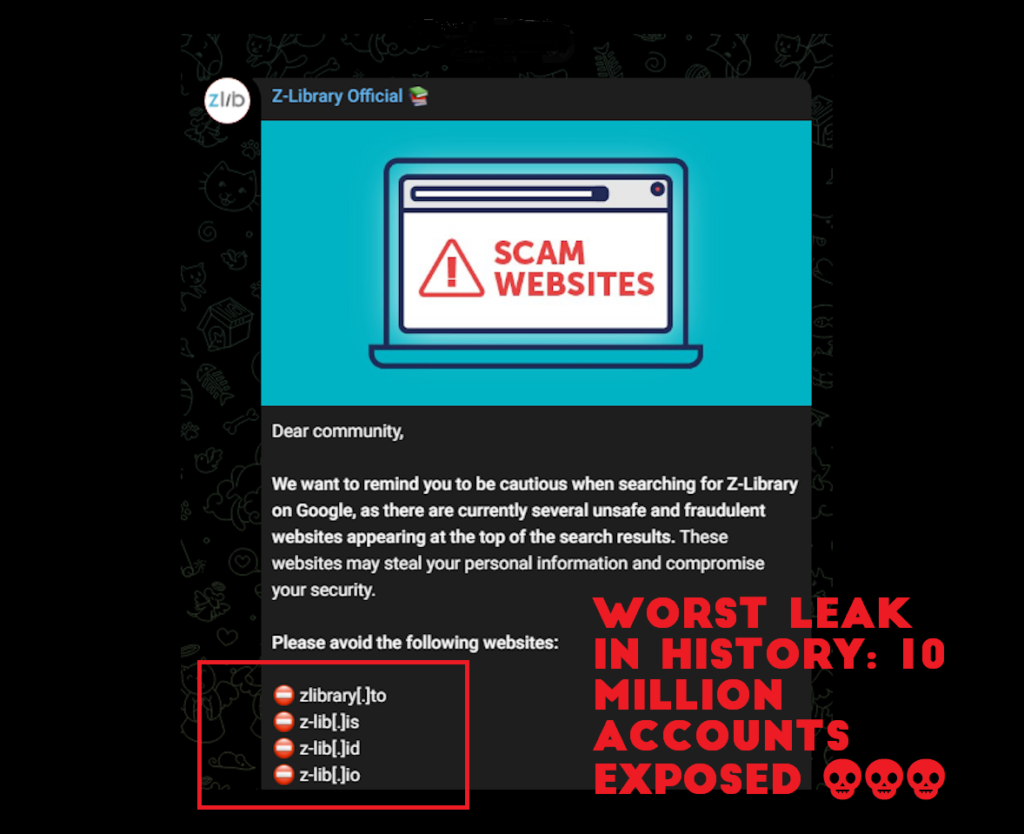
Worst Leak in History: 10 Million Accounts Exposed by Fake Z-Library Scam
Cyberalert: The biggest data leak in history happened. The Z-Library website was illegaly copied by hackers, and as a result, the data of around 10 million users was exposed, as the Cybernews investigation team recently found out. Ten million users mistakenly believed they were on Z-Library, a well-known website for academic papers and books that are pirated online. They were unaware, …
Worst Leak in History: 10 Million Accounts Exposed by Fake Z-Library Scam Read More »