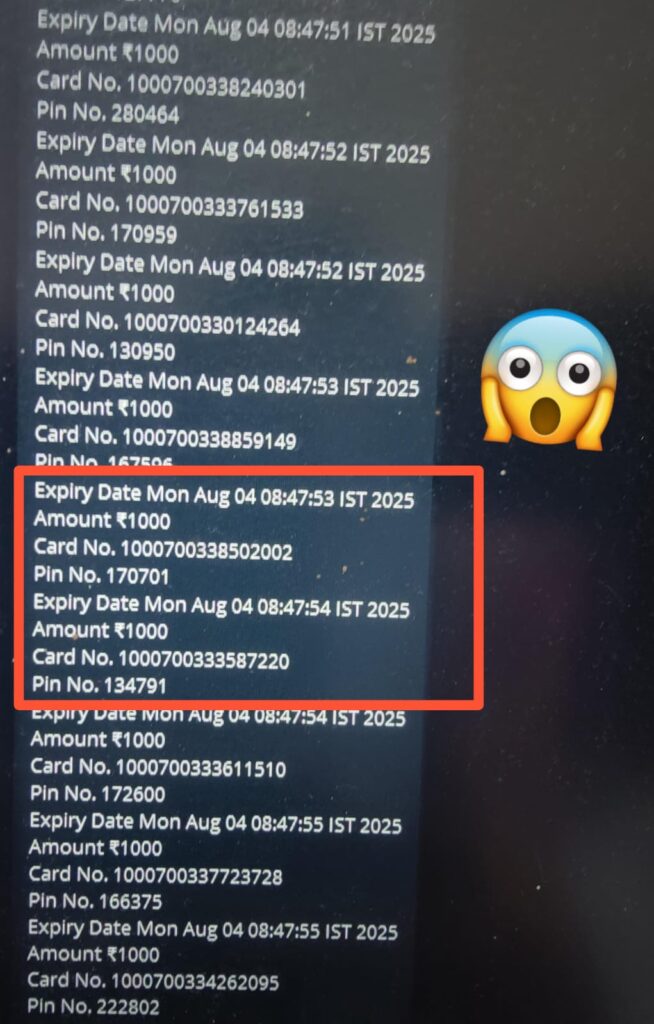
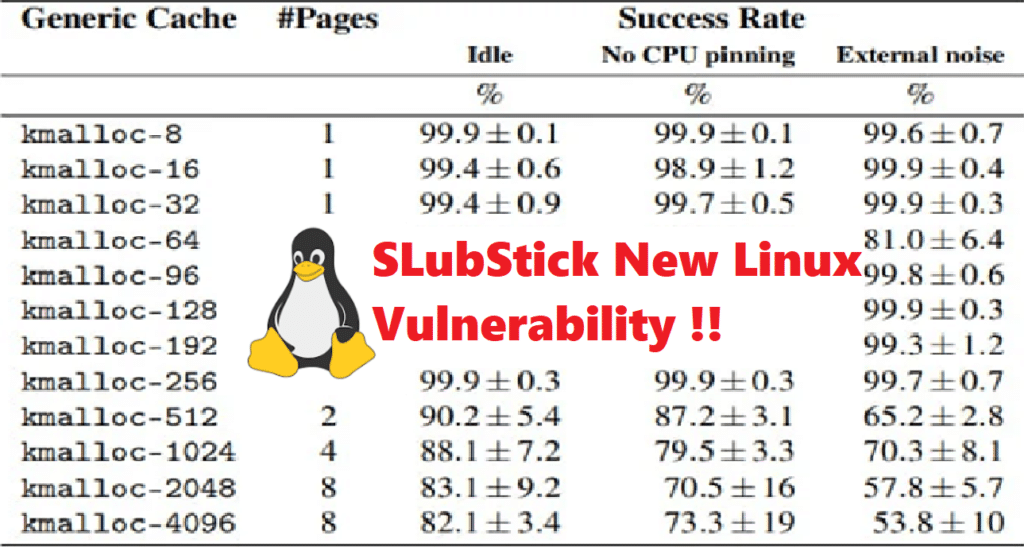
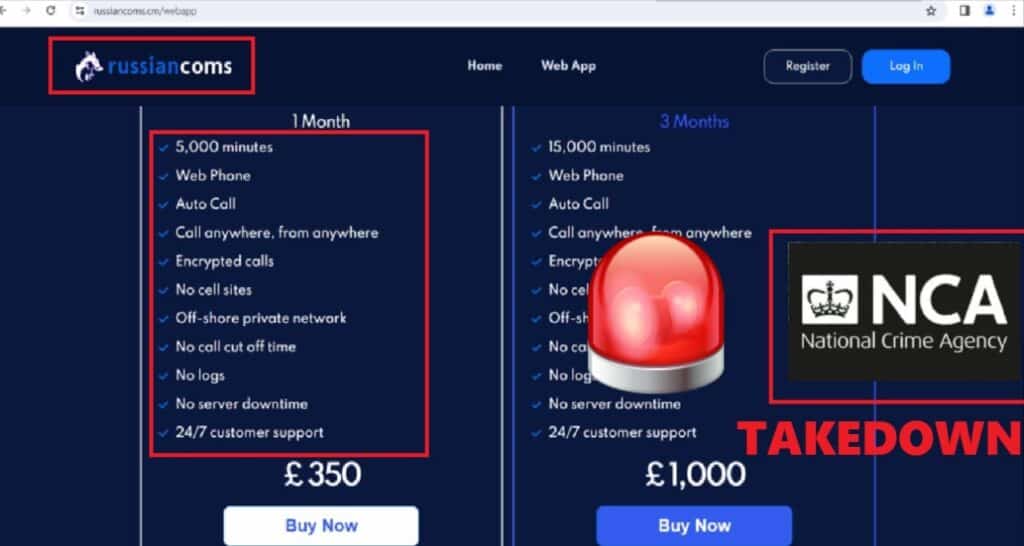
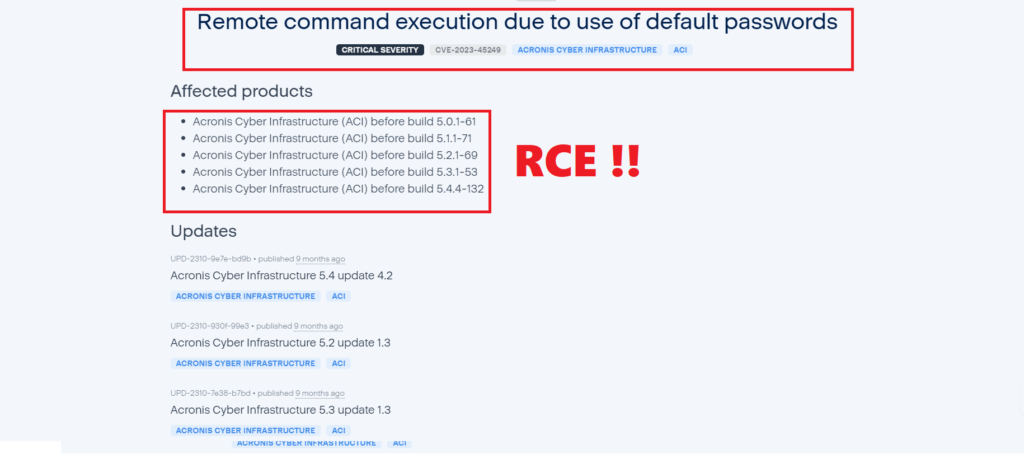
Microsoft Discovers multiple vulnerabilities on OpenVPN
Microsoft has found many vulnerabilities in OpenVPN, a popular VPN software that is incorporated into millions of PCs, routers, mobile devices, firmware, and other smart devices. They could be used in privilege escalation and remote code execution (RCE) attacks when chained together. Microsoft Says “Attack-chained: OpenVPN flaws that could cause RCE and LPE found” Certain […]
Microsoft Discovers multiple vulnerabilities on OpenVPN Read More »