The Famous Yet Uncovered Chinese Spying Tool EagleMsgSpy Has Been Discovered
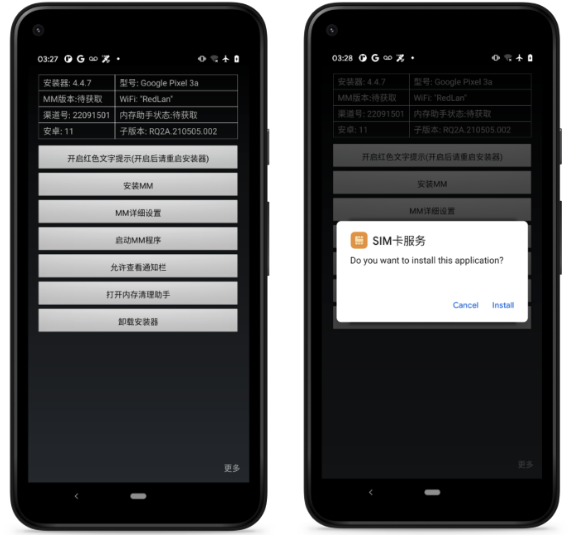
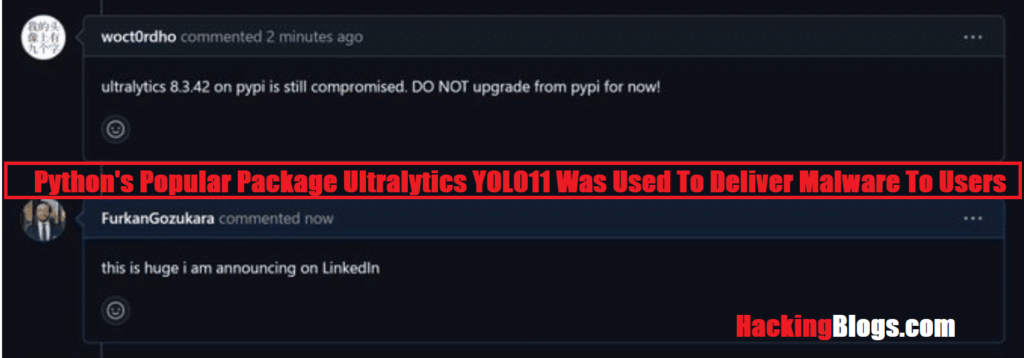
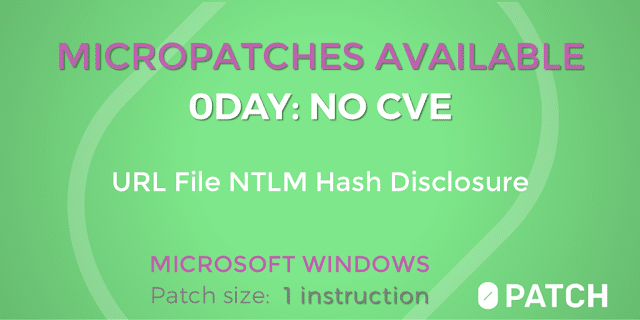
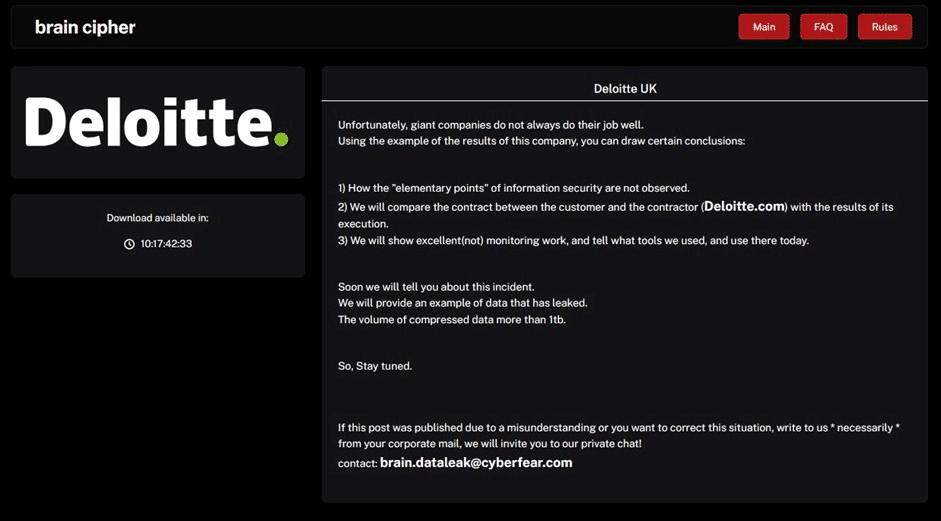
Hackingblogs Users need to be alert The discovery of EagleMsgSpy, a well-known Chinese spying program used by the Chinese intelligence agency and law enforcement to gather huge quantities of data from mobile devices, is the subject of this article, which is both vital and crucial. Several versions of the Android-focused tool have been received by […]
The Famous Yet Uncovered Chinese Spying Tool EagleMsgSpy Has Been Discovered Read More »