The “0.0.0.0 Day” vulnerability affects all popular online browsers, including Apple Safari, Mozilla Firefox, and Google Chrome. The browser developers’ responses differ:
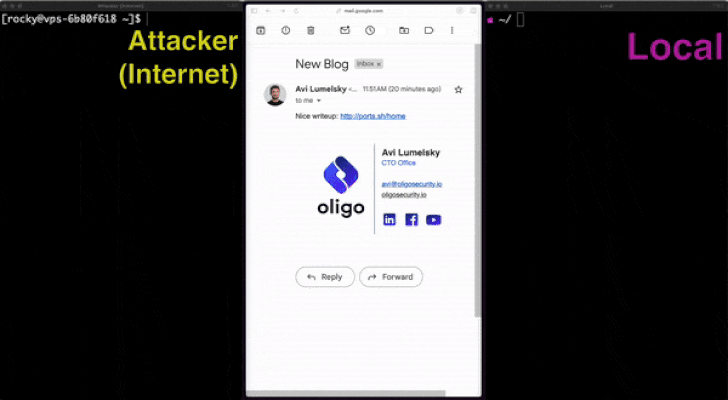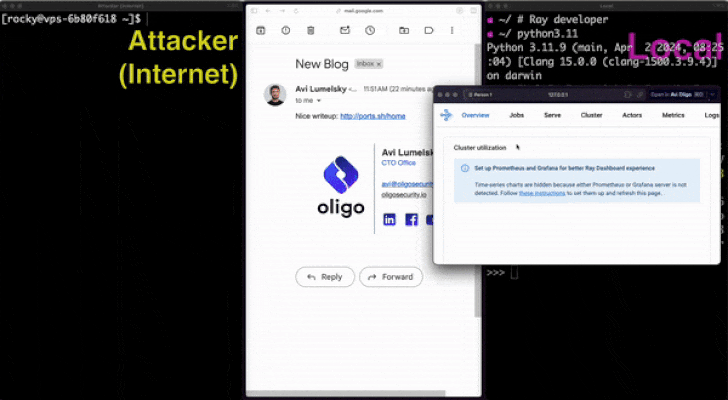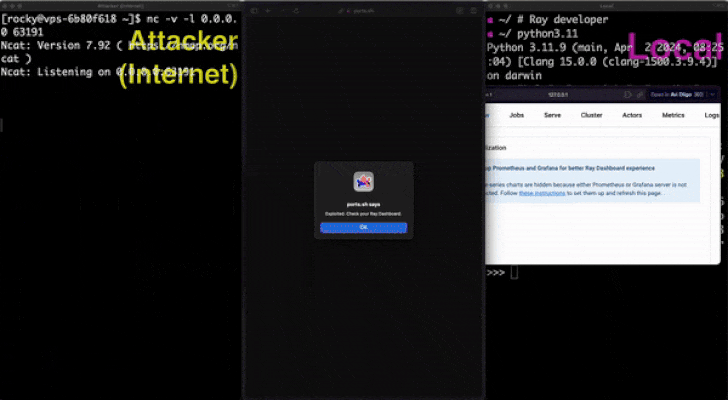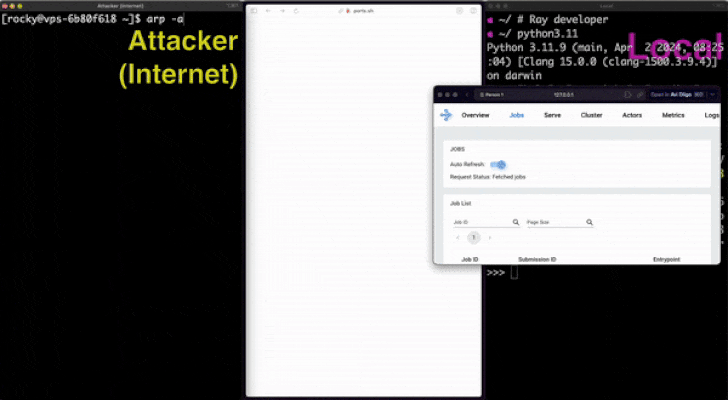
In a NutShell: The research team at Oligo security has discovered a serious flaw known as “0.0.0.0 Day,” which enables malicious websites to communicate with local network services and get beyond browser protection. Unauthorised access and remote code execution may result from this vulnerability.
What is “0.0.0.0 Day”
The research team at Oligo Security discovered the “0.0.0.0 Day” vulnerability earlier today. It is based on differences in how security features are set up in various web browsers, which gives attackers the opportunity to connect with local network services using the IP address 0.0.0.0. While Windows systems are unaffected, this may result in remote code execution and unauthorised access to MacOS and Linux services.

The problem comes from the browser industry’s lack of standards when it comes to how network requests are handled. In the past, the IP address 0.0.0.0 was used for a variety of purposes, such as representing all IP addresses on a host and serving as a stand-in for localhost. Oligo Security discovered that this address can be used by outside websites to communicate with local services, eluding the security protocols meant to prevent such exchanges.
Additionally, it bypasses Private Network Access (PNA), a feature that prevents direct access from public websites to endpoints housed within private networks.
By sending a POST request to 0.0.0[.]0:4444 with a specially constructed payload, any application that runs on localhost and is accessible via 0.0.0.0 might be vulnerable to remote code execution, including local Selenium Grid instances.
According to Lumelsky, “services that use localhost assume a limited environment.” “Insecure server implementations result from this assumption, which can be wrong, as in the case of this vulnerability.”
“With just one HTTP request, attackers may use public domains to target localhost services and even obtain arbitrary code execution (RCE) through pairing 0.0.0.0 with mode ‘no-cors.'”

Google’s Private Network Access (PNA) program seeks to prevent websites from accessing local network services. It is compatible with Google Chrome and Chromium-based browsers such as Edge. But PNA was bypassed by the 0.0.0.0 vulnerability. Google is releasing fixes to prevent access to 0.0.0.0; Chrome 133 is expected to fully incorporate this change.
Apple Safari: By adding a check to the destination host IP address, Apple has modified WebKit to prevent access to 0.0.0.0.
Mozilla Firefox: The Fetch specification has been changed to ban 0.0.0.0, even though Firefox has never previously blocked access to private networks. The whole PNA implementation has been given priority, however it is not yet accessible.

While they wait for browser updates, developers can safeguard their local applications in a few ways:
- Use PNA headers to limit access to the network.
- Check requests’ HOST headers to stop DNS rebinding attempts.
- Add authorisation layers instead of trusting that localhost is secure.
- Whenever possible, use HTTPS.
- In local applications, use CSRF tokens to stop cross-site request forgery.
The discovery of “0.0.0.0 Day” highlights the necessity of strong security protocols that are consistent across all browsers. Without these guidelines, vulnerabilities may continue to be exploitable, giving attackers the ability to carry out harmful activities with little difficulty.


