Over 15,000 plaintext VPN passwords and Fortinet firewall configurations were made public on the darknet due to a significant data breach. The dataset, which was leaked by a new hacking group known as the “Belsen Group,” covers 145 nations and has major effects in Germany, the United States, and Mexico.

The Fortinet breach, which was most likely caused by taking advantage of the major CVE-2022-40684 vulnerability, includes private data including SSH keys, encrypted Wi-Fi passwords, and administrator credentials. Since the data was stolen in 2022, there is a serious possibility of more cyberattacks, hence it is urgently advised to upgrade the firmware and disable remote access.
Who are the Belsen Group ?
The “Belsen Group,” a mysterious hacking criminal organisation, made a surprising appearance on the darknet by exposing more than 15,000 Fortinet firewall configurations, including plaintext VPN passwords. This group’s free release of a huge quantity of data has raised issues in the cybersecurity industry.
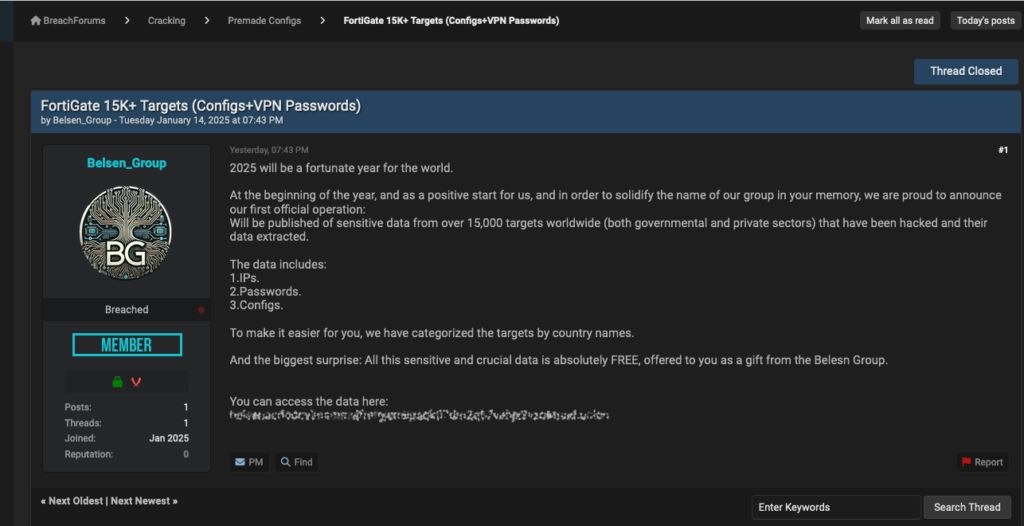
Specific devices and firmware versions were also disclosed in the leak; the majority were running out-of-date FortiOS versions 7.0.0 to 7.2.2. This means that the breach most likely happened in late 2022, when attackers were able to download configuration data due to the vulnerability CVE-2022-40684.Since there have been no reports of ransom demands or money motivations, the group’s intentions are still unknown.
According to security experts, the action might be an attempt to damage targeted organisations or an attempt to gain popularity in the cybercrime community.
Analyzing the Exposed Data And Verifying Leak Authenticity
The “Belsen Group” posted the compromised dataset on the darknet, which included comprehensive configuration files from thousands of Fortinet devices, the majority of which were firewalls and VPN appliances.
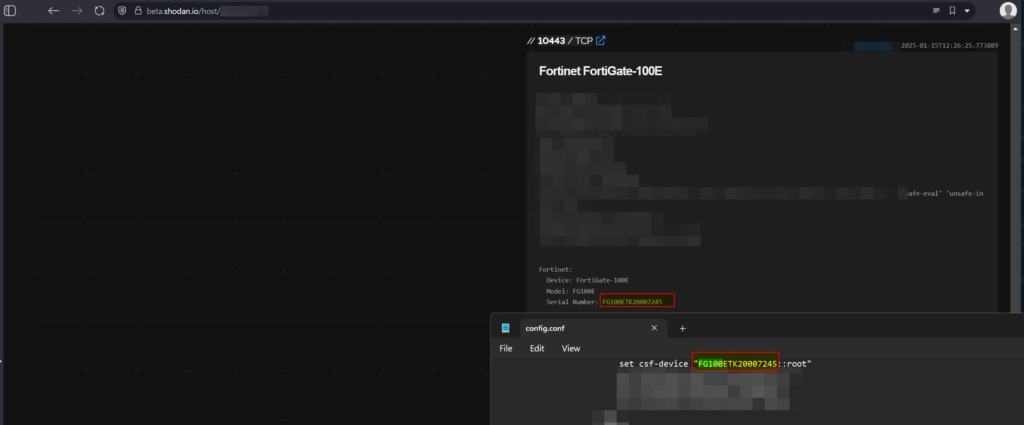
Since the gadgets in this dump are listed on Shodan and have identical serial numbers, Kevin Beaumont confirms that it is authentic:
Types of Exposed Data:
- VPN Passwords (Plain Text)
- Complete Configuration Files
- Encrypted Admin Passwords
- SSH Private Keys
- Encrypted WLAN Passwords
- Firmware and Device Information
- Geographic Distribution and Targeted Networks
Geographic Impact:
Mexico: 1,603 devices compromised.
USA: 679 devices compromised.
Germany: 208 devices compromised.
The researcher came to the conclusion that the majority of Businesses employing telecommunication or business leased line services provided the data that was made public. Some are governments, and some are also big businesses.
Every country which has in scope Fortinet products are visible in the data, except for one — Iran.
Exploitation of CVE-2022-40684: The Root Cause of the Breach
The CVE-2022-40684 vulnerability in Fortinet’s FortiOS was exploited, resulting in the compromise. Due to this vulnerability, attackers were able to steal private configuration files and get around authentication on vulnerable devices. These files included important information like SSH keys, admin credentials, and VPN passwords.
An authentication bypass using an alternate path or channel vulnerability [CWE-288] in FortiOS, FortiProxy and FortiSwitchManager may allow an unauthenticated attacker to perform operations on the administrative interface via specially crafted HTTP or HTTPS requests.
By using this flaw, the attackers were able to collect data from devices that were running out-of-date firmware versions—many of which had not received the required security patches—leaving them vulnerable.
The scope of the data leak highlights the risk that many organisations throughout the world are. In particular vulnerable were devices with out-of-date software that had not been updated following the disclosure of the CVE-2022-40684 issue.


