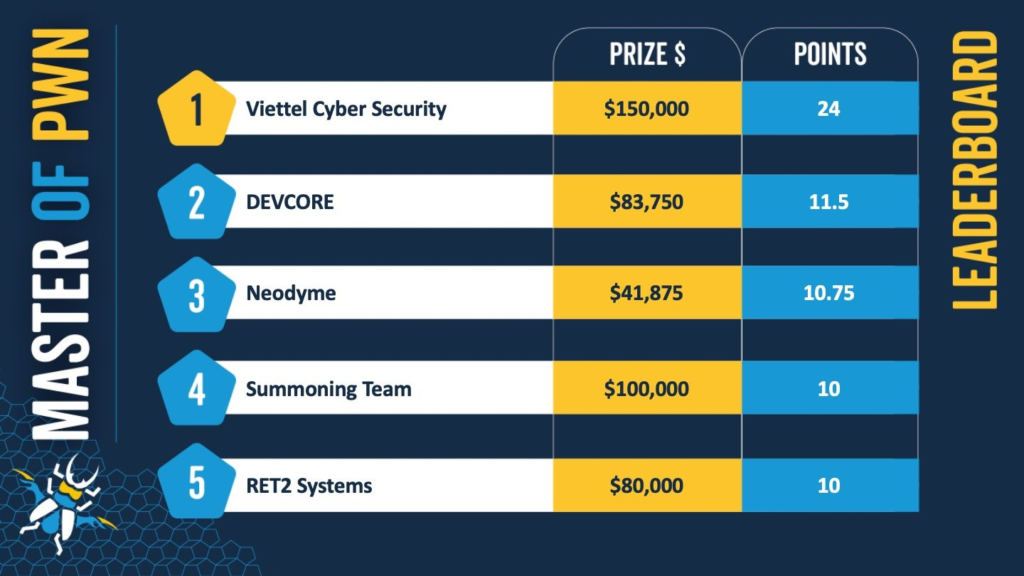
Summary
With impressive performances in a number of categories, the Viettel Cyber Security team had a commanding lead in the competition for the “Master of Pwn” title on day two of Pwn2Own.
- NCC Group’s Ken Gannon exploited the Samsung Galaxy S24 by chaining five flaws, including a path traversal, earning him five points and a $50,000 payment. Installing an app and gaining shell access to the well-known Android device were made possible by his hack.
- Using a Use-After-Free (UAF) vulnerability, Dungdm from Viettel Cyber Security took over a Sonos Era 300 smart speaker. His successful exploit earned his team six Master of Pwn points and an additional $30,000.
- The QNAP TS-464 NAS was compromised by Chris Anastasio and Fabius Watson of Team Cluck, who earned $20,000 and four points for chaining two vulnerabilities, including a CRLF injection.
- ANHTUD’s Pham Tuan Son and ExLuck began the day by taking use of a Canon imageCLASS MF656Cdw printer by employing a stack-based buffer overflow to hack a Canon imageCLASS MF656Cdw printer, earning two Master of Pwn points and $10,000.

Who Are ZDI ?

The Zero Day Initiative (ZDI) was established to incentivise researchers to confidentially report 0-day vulnerabilities to the impacted businesses in exchange for financial rewards. Some in the information security sector at the time believed that people who discovered flaws were malevolent hackers out to cause trouble. The ZDI is currently the biggest vendor-neutral bug bounty programme in the world. Unlike other programmes, they use a distinct method to gathering information on vulnerabilities.
Security researchers compete to exploit mobile hardware and software in the Pwn2Own hacking competition in order to win the coveted title of “Master of Pwn” and $1,000,000 in cash and prizes.
The Team said
Welcome back to Pwn2Own Ireland 2024! Yesterday, we awarded $516,250 for over 50 unique 0-day bugs. Today looks to be just as exciting with attempts on phones, cameras, printers, and smart speakers.
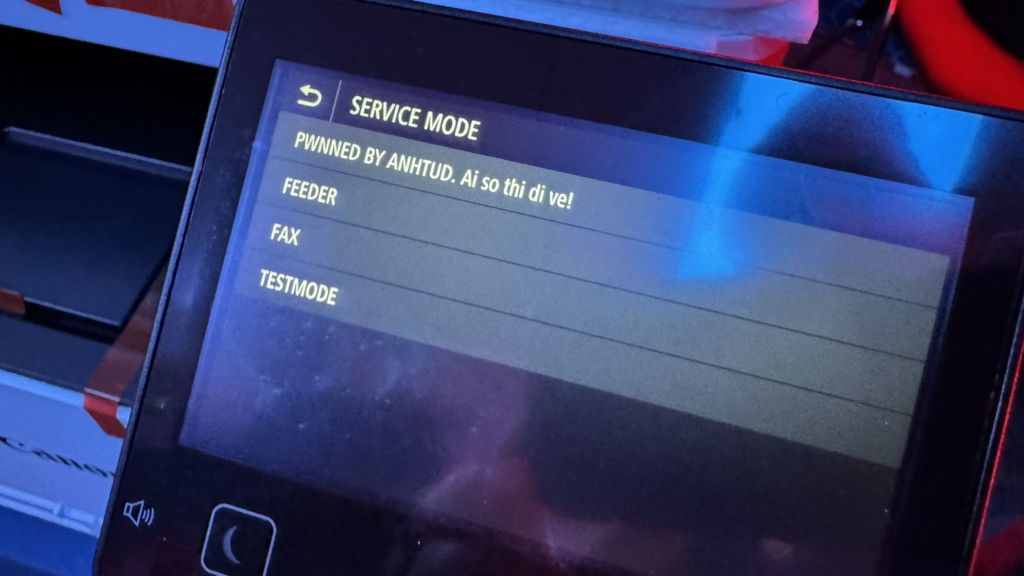
Canon imageCLASS MF656Cdw printer Hacked
ExLuck (@ExLuck99) and Pham Tuan Son (@Little_timmy) from ANHTUD exploited the Canon imageCLASS MF656Cdw printer via a single stack-based overflow. They receive two Master of Pwn points and $10,000 for their victory in the second round.

Samsung Galaxy S24 Hacked
Ken Gannon (@yogehi) of NCC Group (@NCCGroupInfosec) used five different bugs, including a path traversal, to get a shell and install an app on the Samsung Galaxy S24. He earns $50,000 and 5 Master of Pwn points.


Sonos Era 300 Hacked
The Sonos Era 300 was exploited by dungdm (@_piers2) and Viettel Cyber Security (@vcslab) using a single Use-After-Free (UAF) issue. He receives six Master of Pwn points and $30,000 for winning the second round.
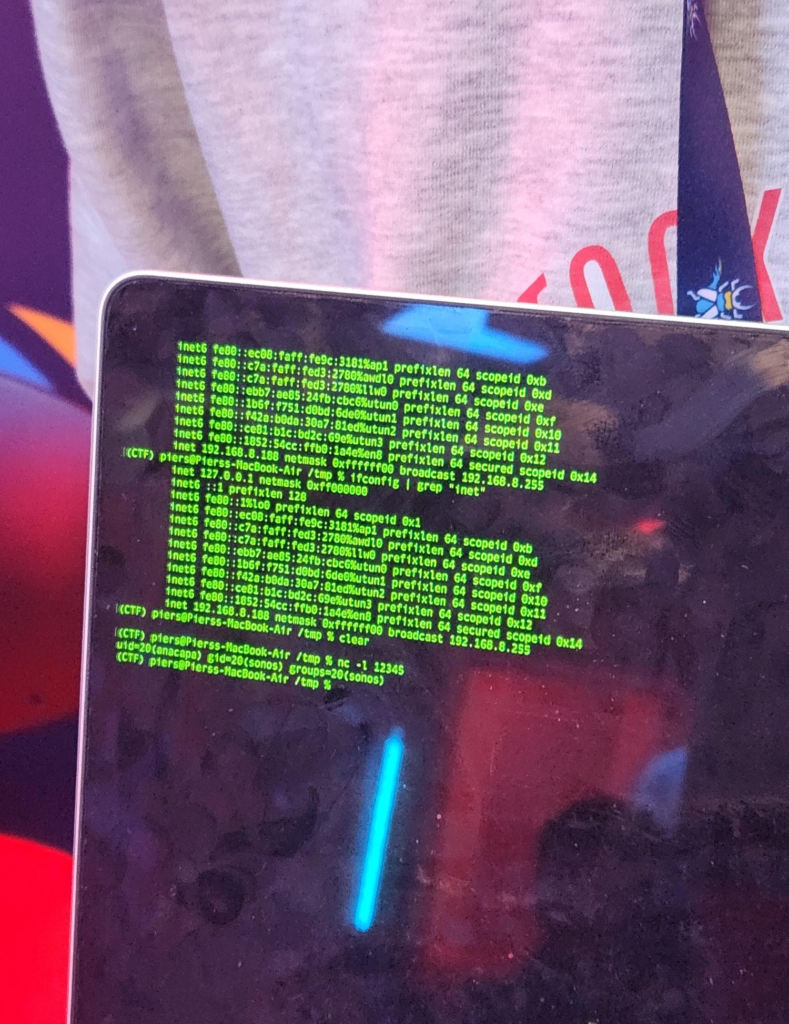
The Sonos Era 300 speaker was taken over by the InfoSect (@infosectcbr) organisation using a heap-based buffer overflow. They receive six Master of Pwn points and $30,000 for their victory in the second round.



