Safepay ransom is a new ransomware gang that has surfaced and is taking advantage of numerous well-known businesses and government organisations. Let us examine the group’s history, the exploitation it engaged in, and some important conclusions in this piece.

Who Is Safepay Ransomware Group ?
Two instances of SafePay ransomware distribution across several customer infrastructures, divided by business vertical and location, were noted by Huntress analysts in October 2024. Huntress analysts had not previously noticed that the ransom letter was named readme_safepay.txt and that the encrypted file extension in both cases was.safepay.
Their Tor leak website merely provides a list of previous victims that may be clicked on to view more information.

Because the SafePay ransomware group is a less well-known cybercrime gang than others, there is not much conversation about it on illegal forums or chat rooms.
Their ransom note does, however, contain a V3 onion link to their leak site and a less well-known link to a “TONNE” website, probably “The Open Network,” which bills itself as a “decentralised and open internet, developed by the community utilising a technology designed by Telegram.“
Triton Sourcing & Distribution, a New Zealand importer, acknowledges the ransomware attack
“We are aware of the incident – we suffered an attack in early October and communicated with our clients and staff about it at the time.It did disrupt our operations for a few days, but we were able to recover relatively quickly and are catching up on some of our delayed orders. We’ve since been taking advice on the incident and the subsequent data leak posting.”
Triton spokesperson
The importer Triton Sourcing & Distribution, located in Auckland, has been identified on the darknet leak website of the SafePay ransomware group, which claims to have taken at least 10 terabytes of data from the business.
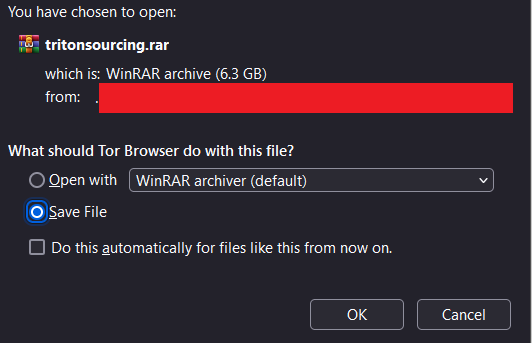
“Information included in our Exo order system, which is the same system that was compromised by the attack,” is the subject of a large portion of the stolen data. Order details and other operational procedures account for a large portion of this data.
Triton believes the leak is comparatively insignificant after taking into account the type of data that was disclosed and its legal responsibilities. Although the hackers have not provided a date for the intrusion, a company representative has acknowledged that the event happened in October.
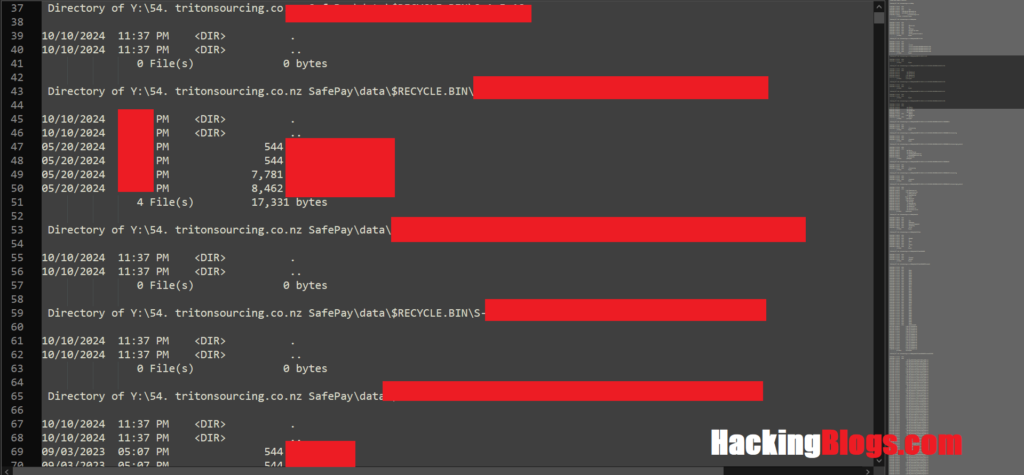

Researchers Found Flaws In Ransomgroup Server
Due to an exposed Apache server status endpoint, the researchers were able to inspect the site’s download folder and obtain additional information on the backend server on the Tor website, which as of November 14, 2024, listed 22 victims.
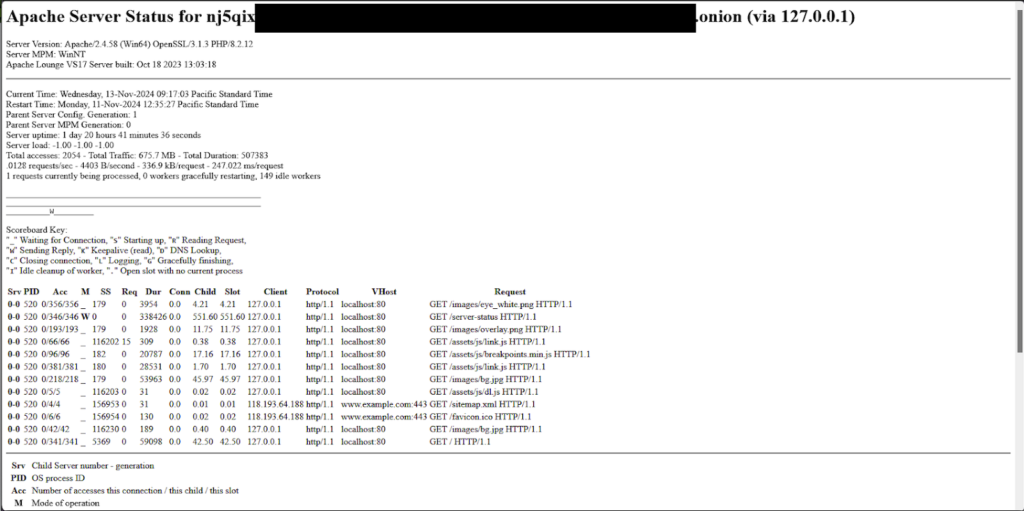
Huntress saw two incidents that targeted businesses in various sectors and regions. By using the Remote Desktop Protocol (RDP) to gain access to the compromised endpoint, SafePay was able to effectively encrypt and retrieve data before being discovered.

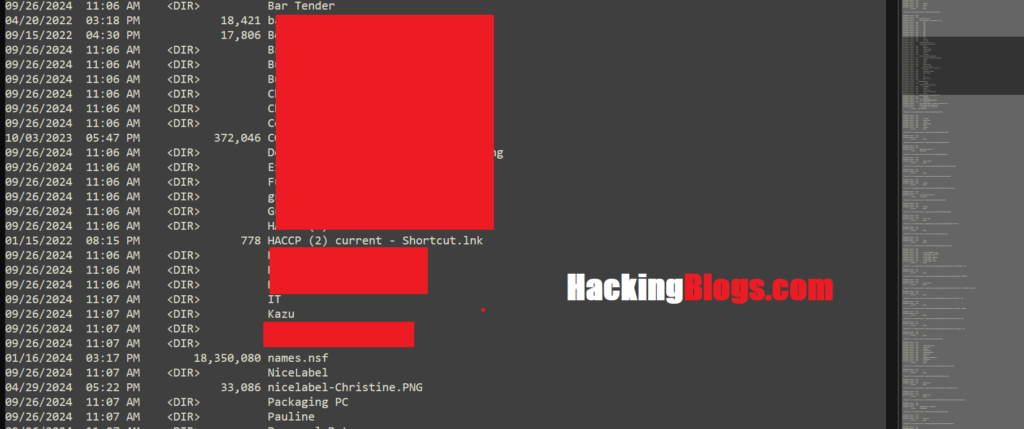
SafePay ransomware attack confirmed by Snow Brand Australia
“Snow Brand recently experienced a cyber incident where unusual activity was detected on our network.We acted immediately to secure our network and initiate an investigation to understand what happened, including any impact to information.”
A representative for Snow Brand told Cyber Daily
Sometime during the past week, Snow Brand and 23 other victims were listed on the gang’s darknet leak website. The gang seems to be a relatively new enterprise, with a potential base in Russia.

The leak site for SafePay is extremely basic; it only lists each victim, their earnings, the publication location, and links to the files and stolen data. The group has released an archival dataset for Snow Brand that is nearly 24 terabytes in size. Some employee data is also included, including Medicare applications, medical certificates, and superannuation information.


