Hi, HACKINGBLOGS Community, This is Dipanshu Kumar.
Don’t worry, the articles are back and regular! I know you’ve missed me! However, this one is quite significant. I’ll be analyzing some startling CYBLE research today, which found 20 fake apps that are actually Crypto Keys stealers rather than apps. Let’s get started immediately! Additionally, remember to share the word as widely as you can.

What Analysis Took Place : A Brief Overview Of Crypto Keys Stealers
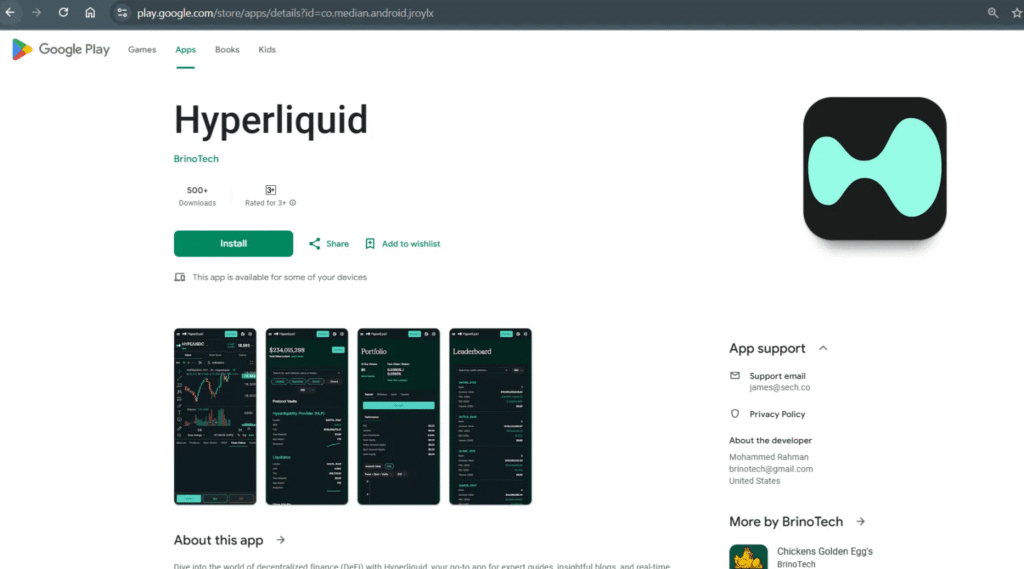
More than 20 confirmed apps on the Google Play Store were discovered to be Crypto Keys stealers in CYBLE‘s surprising discovery. These apps used phishing techniques to trick users by impersonating well-known wallets such as SushiSwap, PancakeSwap, Hyperliquid, and Raydium. Phishing URLs, which ask users to enter a 12-word mnemonic phrase to access fake wallet interfaces, were a typical approach used by these apps. These apps’ fake nature was made worse by the fact that they were being posted using developer accounts that had been hacked.
After being successfully reported to Google, the majority of the malicious apps were taken down from the Play Store. Some of these shady programs are still out there, though, actively pursuing users in an attempt to obtain their login information. Everyone must continue to be alert and watchful. But don’t worry, I’ve got you covered if you follow HACKINGBLOGS. I’ll keep you updated and assist you in avoiding these dangers!

By using same profiles and logos to authentic wallets, these malicious apps go one step further in making it more difficult for users particularly those who are not familiar with security to distinguish between the two. Because of this degree of dishonesty, it is even more important to remain vigilant and aware.
Pattern And Protocol Analysis : Critical Observation
When the behavior of these applications was examined, it was found that, in addition to the previously stated phishing URLs, they also use additional misleading strategies. The incorporation of Command and Control (C&C) URLs into their privacy policies is one such technique that makes it more difficult to detect and facilitates remote management of these malicious programs by attackers.
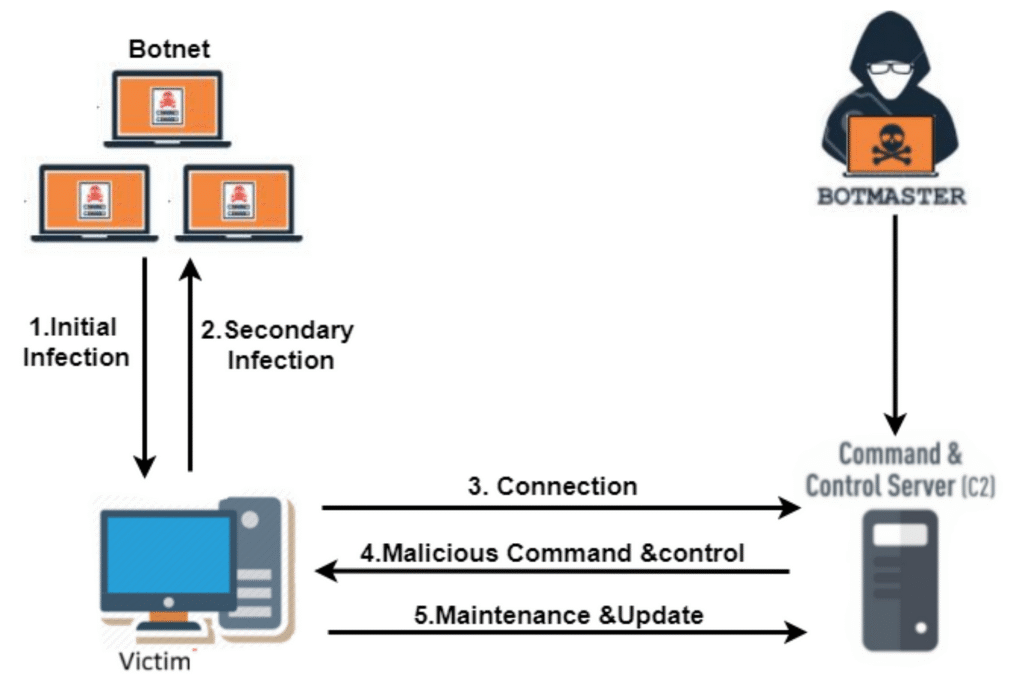
Hacked Developers Account Spreading The Malware : Major ISSUE*
The main issue I discovered during my investigation is that the developer accounts that were spreading this malware were in fact compromised. The fact that these accounts were previously validated and had a solid reputation for spreading trustworthy and secure software only serves to increase the danger.
This indicates that consumers already saw these identities as trustworthy, increasing the likelihood that even tech-savvy people would become victims of these Crypto Keys stealers . This reputation made it even more difficult to identify these malicious programs.
Let’s Have A Look At The List Of These 20 Alleged Appliactions
I understand that you feel as though we have covered a lot of ground, so let’s move on to the list of the 20 apps that CYBLE found to be Crypto Keys stealers. Remember that while many have already been removed, some remain on the Play Store, ready to attract susceptible people.
| Name | Package name | Privacy Policy |
| Pancake Swap | co.median.android.pkmxaj | hxxps://pancakefentfloyd.cz/privatepolicy.html |
| Suiet Wallet | co.median.android.ljqjry | hxxps://suietsiz.cz/privatepolicy.html |
| Hyperliquid | co.median.android.jroylx | hxxps://hyperliqw.sbs/privatepolicy.html |
| Raydium | co.median.android.yakmje | hxxps://raydifloyd.cz/privatepolicy.html |
| Hyperliquid | co.median.android.aaxblp | hxxps://hyperliqw.sbs/privatepolicy.html |
| BullX Crypto | co.median.android.ozjwka | hxxps://bullxni.sbs/privatepolicy.html |
| OpenOcean Exchange | co.median.android.ozjjkx | hxxps://openoceansi.sbs/privatepolicy.html |
| Suiet Wallet | co.median.android.mpeaaw | hxxps://suietsiz.cz/privatepolicy.html |
| Meteora Exchange | co.median.android.kbxqaj | hxxps://meteorafloydoverdose.sbs/privatepolicy.html |
| Raydium | co.median.android.epwzyq | hxxps://raydifloyd.cz/privatepolicy.html |
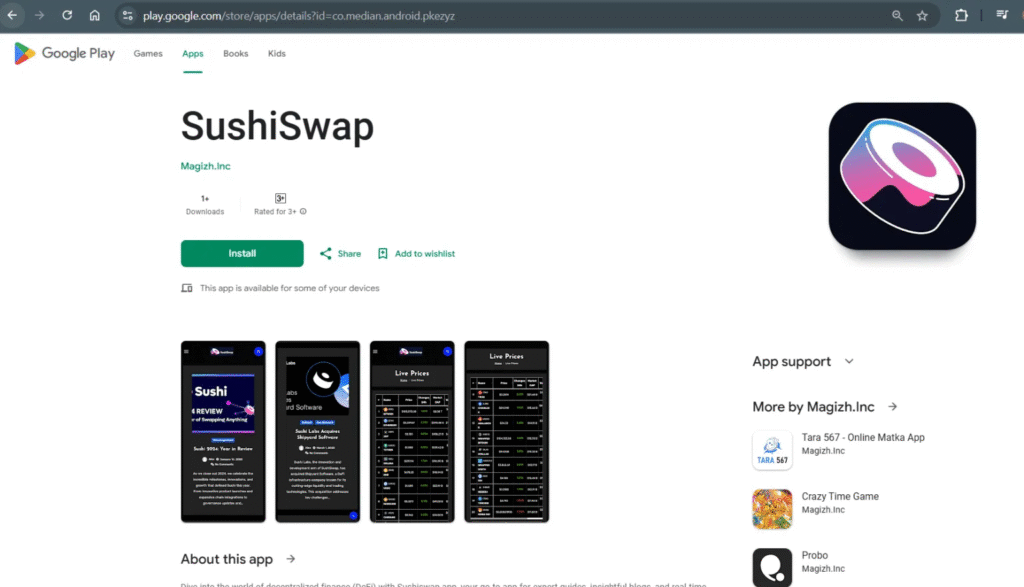
| SushiSwap | co.median.android.pkezyz | hxxps://sushijames.sbs/privatepolicy.html |
| Raydium | co.median.android.pkzylr | hxxps://raydifloyd.cz/privatepolicy.html |
| SushiSwap | co.median.android.brlljb | hxxps://sushijames.sbs/privatepolicy.html |
| Hyperliquid | co.median.android.djerqq | hxxps://hyperliqw.sbs/privatepolicy.html |
| Suiet Wallet | co.median.android.epeall | hxxps://suietwz.sbs/privatepolicy.html |
| BullX Crypto | co.median.android.braqdy | hxxps://bullxni.sbs/privatepolicy.html |
| Harvest Finance blog | co.median.android.ljmeob | hxxps://harvestfin.sbs/privatepolicy.html |
| Pancake Swap | co.median.android.djrdyk | hxxps://pancakefentfloyd.cz/privatepolicy.html |
| Hyperliquid | co.median.android.epbdbn | hxxps://hyperliqw.sbs/privatepolicy.html |
| Suiet Wallet | co.median.android.noxmdz | hxxps://suietwz.sbs/privatepolicy.html |
As Analysis says these two badboys got a different package for exploitation.
| Raydium | cryptoknowledge.rays | hxxps://www.termsfeed.com/live/a4ec5c75-145c-47b3-8b10-d43164f83bfc |
| PancakeSwap | com.cryptoknowledge.quizzz | hxxps://www.termsfeed.com/live/a4ec5c75-145c-47b3-8b10-d43164f83bfc |
Technical Details of the Malicious Apps
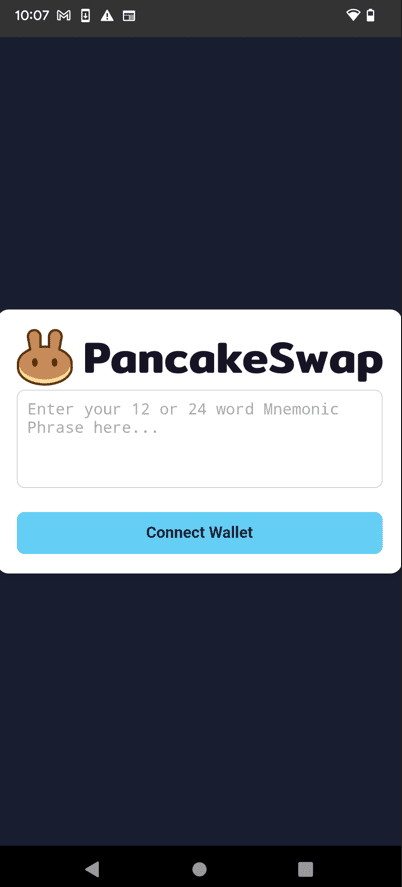
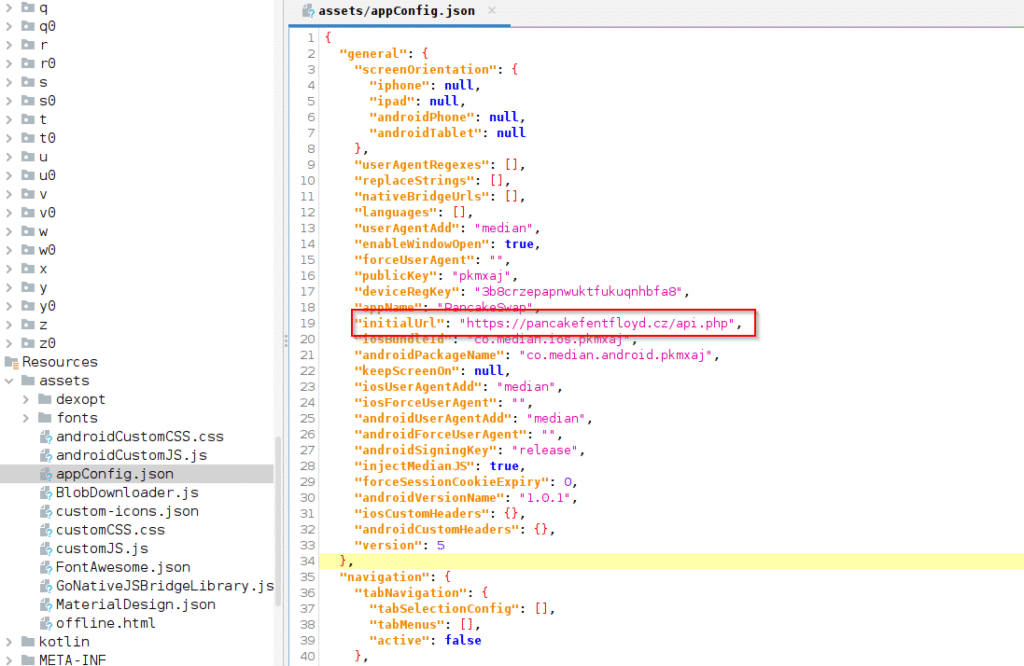
Two primary methods are used by the malicious apps found in CYBLE’s investigation to steal users’ mnemonic phrases. First, phishing websites, like the PancakeSwap–impersonating website located at hxxps://pancakefentfloyd[.]cz/api.php, may be quickly transformed into Android apps using the Median framework. Users are asked to submit their 12-word mnemonic phrase on this website.
Another strategy involves threat actors impersonating Raydium and tricking users into disclosing their mnemonic phrases by directly loading phishing URLs, such as hxxps://piwalletblog[.]blog, within a WebView. Malicious apps of both kinds are linked to an infrastructure located on IP 94.156.177[.]209, which is associated with more than 50 phishing domains that pose as well-known cryptocurrency services.
Since these domains are utilized by several fake apps, discovery and prevention become more difficult.