Hi everyone in the HackingBlogs community!
Your trainer, Dipanshu Kumar, is here. I started API-HACKING BOOTCAMP where i went into the topic of API security a few weeks ago when I gave a free API Hacking Masterclass. Although I am aware that some of you were unable to attend the live session, the feedback I received was extremely positive.
As a token of appreciation, I’m giving you access to my private, handwritten notes from the course or free. Unlike other free classes, this one has an added benefit: you are welcome to join our WhatsApp group. It’s a community where we talk about hacking and exchange ideas in addition to being a place for resources. Let’s begin by delving into the notes!
Thanks for the amazing response on API-HACKING BOOTCAMP
What Are APIs?
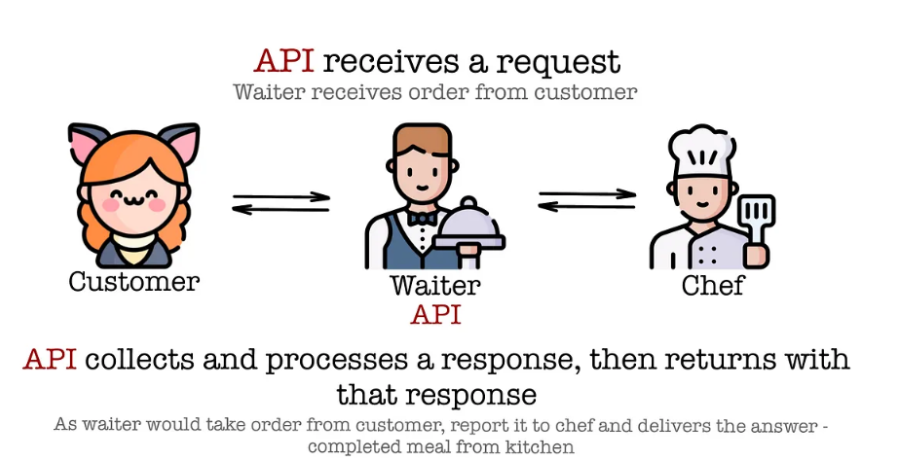
Understanding the fundamentals of our topic APIs (Application Programming Interfaces) is crucial before we begin hacking. To put it simply, APIs are a collection of protocols that facilitate communication between various software programs. APIs are the foundation of today’s web applications, whether they are used for data extraction, request processing, or service integration.
What are Remote APIs and RESTful APIs?

Although there are many other kinds of APIs, RESTful and remote APIs are two of the most popular. Your application can communicate with services on a distant server or network by using remote APIs. On the other hand, REST (Representational State Transfer) APIs use a client-server, stateless architecture. REST APIs are simple to use and integrate into modern applications since they execute activities using common HTTP methods like GET, POST, PUT, and DELETE.
Using APIs (Integration)
One of the first things you should do when interacting with external services is to integrate an API into your project. We’ll walk through the steps of investigating, connecting, and utilizing APIs in this part. This could involve making requests and using authentication tools like OAuth tokens and API keys.
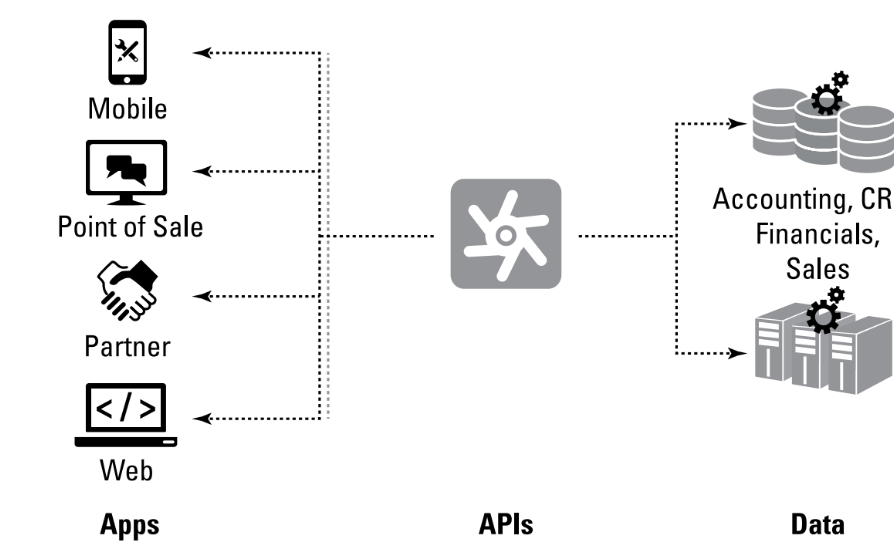
The fundamental processes for investigating and integrating APIs are as follows :-
- API Authentication: It’s critical to comprehend how to approve and authenticate requests. This covers OAuth, tokens, and API keys.
- Creating Requests: Discover how to use Postman and other tools to send GET, POST, PUT, and DELETE requests to APIs.
- Parsing Responses: JSON and XML are common formats that APIs return. Developing useful apps requires an understanding of how to respond to these responses.
Setting Up for API Testing
Setting up the appropriate tools and environment is crucial before we begin testing actual APIs. This covers anything from containerized systems to web proxy solutions that enable us to replicate real-world situations.
Tools of the Trade: Setting Up & Installation
- Burp Suite: A powerful tool for web application security testing. We’ll use Burp to intercept API requests and responses, modify parameters, and manipulate data to identify vulnerabilities.
- Postman: An API testing tool used to send HTTP requests to APIs and inspect responses. It’s great for manual testing of API endpoints.
- Docker: We’ll use Docker to create isolated environments for running vulnerable APIs (like dvapi and crapi) and testing them against security exploits.
- dvapi and crapi: Vulnerable APIs specifically designed for practice. They allow us to simulate real-world API vulnerabilities safely.
The Links Have Been Added Just Click On The Images To Reach Through The Destination Application Download Page

Common API Vulnerabilities We’ll Explore
Broken Object Level Authorization (BOLA) : Because APIs frequently neglect to appropriately verify authorization at the object level, attackers can manipulate object identifiers to obtain data that is not authorized.
Broken Authentication: Attackers may be able to compromise authentication tokens, take over sessions, and impersonate users due to inadequate security procedures.
Excessive Data Exposure: APIs may provide responds that contain too much information, exposing private data that an attacker could use against you.
Unrestricted Resource Consumption: Attackers may misuse resources due to API vulnerabilities, which could result in DoS (Denial of Service) attacks or higher operating expenses.
Broken Function Level Authorization : Attackers can escalate privileges and gain access to sensitive functionality when APIs fail to distinguish between administrator and ordinary user functions.