ALERT: SLUBStick is a recently-discovered cross-cache attack that targets the Linux kernel and has a 99% success rate in transforming restricted heap vulnerabilities into read-and-write access to arbitrary memory. Threat actors can escalate privileges or escape containers thanks to this exploit, which presents serious security risks.
Researchers have discovered a 99% effective method of getting around Linux kernel security.
A new attack known as SLUBStick, developed by researchers at the Technical University of Graz in Austria, allows an attacker to take advantage of a limited heap vulnerability and read and write memory at will. This attack can be used to escalate privileges or break out of containers.
Linux kernel versions 5.9 and 6.2 were used to evaluate the attack, demonstrating the method’s great degree of adaptability. Nine known vulnerabilities were employed in the research on 32- and 64-bit systems.

Furthermore, the attack functioned with all modern kernel defences turned on, including Kernel Address Space Layout Randomisation (KASLR), Supervisor Mode Execution Prevention (SMEP), and Supervisor Mode Access Prevention (SMAP).
Details of SLUBStick
Memory is managed by the Linux kernel by allocating and releasing memory blocks, or slabs, for various kinds of data structures. A cross-cache attack is when an attacker uses flaws in the memory management mechanism to damage or alter data structures. These kinds of attacks frequently cause system crashes and are usually successful in 40% of cases.
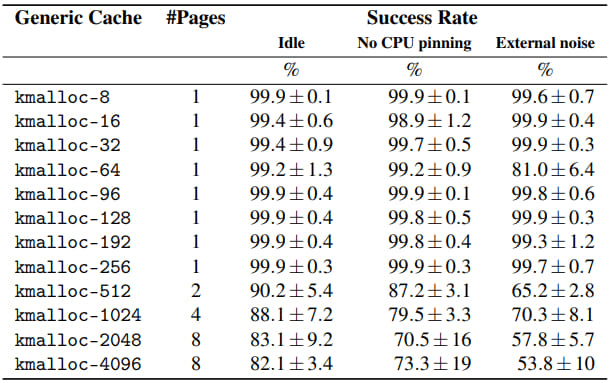
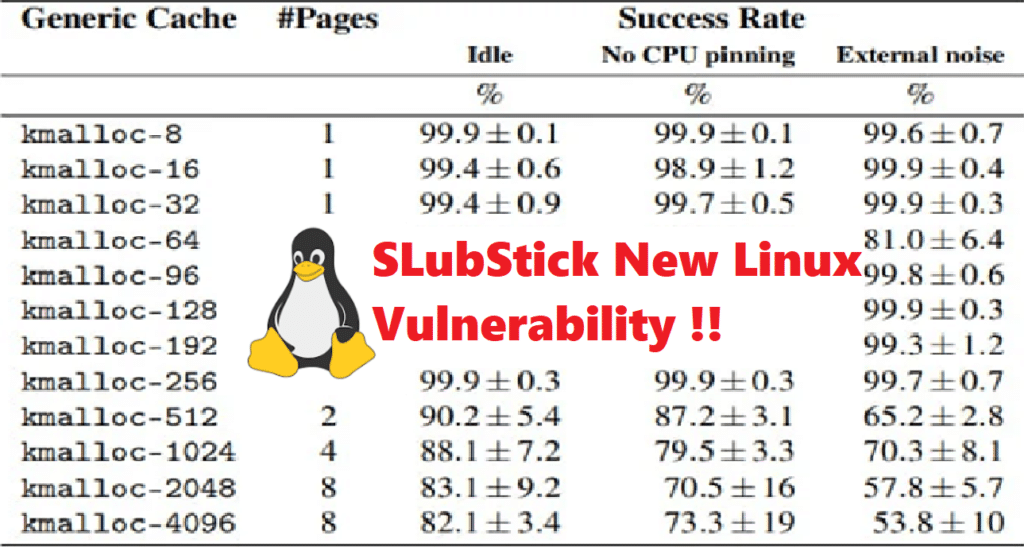
SLUBStick manipulates the memory allocation process by taking use of heap vulnerabilities like double-free, use-after-free (UAF), or out-of-bounds writes. The attacker can then prepare for and control memory reuse by using a timing side channel to pinpoint the precise moment at which memory blocks are allocated and released.
With this knowledge, there is a 99% chance of effectively launching a cross-cache attack, which makes SLUBStick extremely useful.
Three steps are involved in converting the heap bug into an arbitrary memory read-and-write primitive:
- Wait for the kernel to utilise the memory chunks that you have freed up.
- Make sure these portions are repurposed for important data structures such as page tables by controlling their reallocation.
- The attacker has the ability to read and write any memory location by overwriting the page table entries after reclaiming them.

Actual Defence Effect
SLUBStick requires local access to the target machine with code execution capability, much like the majority of side-channel attacks. In addition, the attack has to take use of a Linux kernel heap vulnerability in order to access memory.
Attackers can benefit from the attack in a number of ways. SLUBStick opens the door to escalation of privileges, bypassing of kernel protections, escape from containers, and integration into complex attack chains—even for individuals who already possess code execution capabilities.

Both container escape and privilege escalation provide ways to break out of the isolated environment and reach the host system. Using privilege escalation, one can obtain root access and carry out any activities. SLUBStick has the ability to alter kernel structures or hooks during the post-exploitation stage in order to remain active and evade detection.


