Hello users, are you aware of the latest AMD Vulnerability that is gaining popularity? This vulnerability was of high severity and could result in the loss of SEV protection. Let us have a look at the vulnerability and go into more detail later in the post.

“may allow an attacker with local administrator privilege to load malicious CPU microcode resulting in loss of confidentiality and integrity of a confidential guest running under AMD SEV-SNP,”
CVE-2024-56161
“The vulnerability is that the CPU uses an insecure hash function in the signature validation for microcode updates. This vulnerability could be used by an adversary to compromise confidential computing workloads protected by the newest version of AMD Secure Encrypted Virtualization, SEV-SNP or to compromise Dynamic Root of Trust Measurement,”
An incorrect signature verification in the microcode patch loader on the AMD CPU read-only memory is the vulnerability. Microcode is usually loaded during startup, therefore if malicious microcode is loaded, it may enable attackers to alter CPU operation.The vulnerability may be exploited by an attacker with root access from outside a virtual machine to load malicious microcode patches, according to Google security experts who were credited with exposing it.
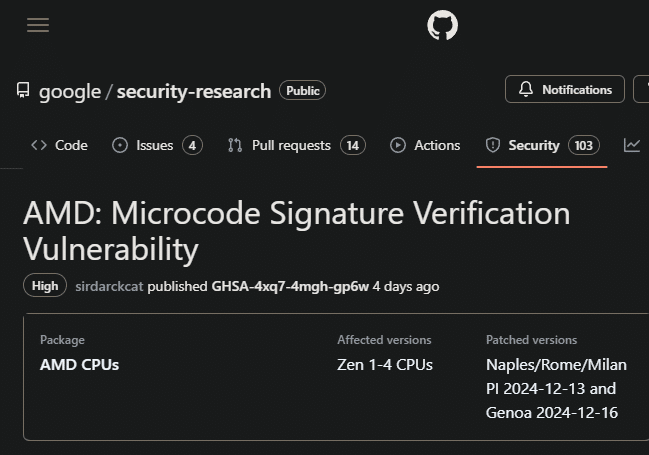
Google claimed to have discovered a security flaw in a few AMD Zen-based CPUs. Due to this vulnerability, malicious microcode patches can be loaded by an attacker with local administrator rights. On Zen 1 through Zen 4 CPUs, they have shown that they can create arbitrary harmful microcode patches. The CPU’s usage of an unsafe hash function for microcode update signature validation is the weakness.
An attacker might use this issue to compromise Dynamic Root of Trust Measurement or sensitive computing workloads safeguarded by the most recent version of AMD Secure Encrypted Virtualisation, SEV-SNP.
To show that this vulnerability enables an attacker to create arbitrary microcode patches, they supplied these Proofs of Concept. In addition to setting the carry flag (CF) to 0 to show that the returned value is incorrect, they make the RDRAND instruction always return the constant 4.
# Load the microcode patch on every CPU
PAGE_OFFSET_BASE=$(
objdump -s --start-address=0x$(cat /proc/kallsyms |
awk '/D page_offset_base/{print $1}') /proc/kcore |
awk '/ffff/{print $2 $3; exit}' |
sed 's/\(..\)\(..\)\(..\)\(..\)\(..\)\(..\)\(..\)\(..\)/\8\7\6\5\4\3\2\1/')
for i in `seq 0 $(nproc)`; do ./ucode_loader ./milan_rdrand_carryclear_encrypted.bin 0x${PAGE_OFFSET_BASE:?} $i; done
# Test rdrand
./rdrand_test
rdrand_test: rdrand failed and returned 4
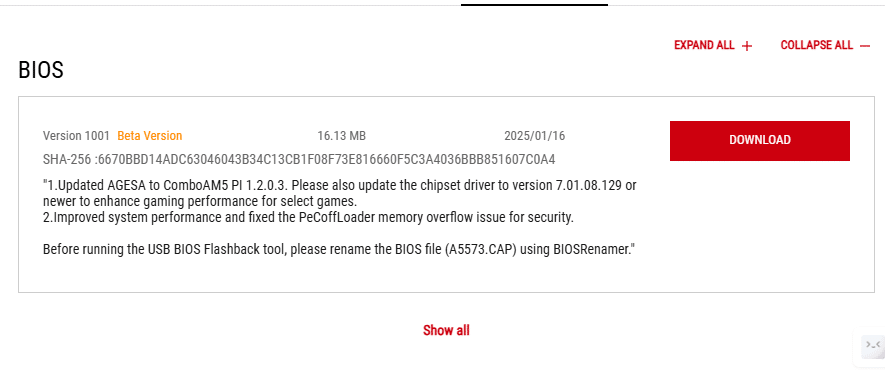
PC manufacturer Asus accidentally disclosed the patch for the vulnerability in the release notes for a beta BIOS update for a few of its motherboards last week, presenting it as a microcode signature verification issue. This led to the discovery of the vulnerability.
Additionally, SEV-SNP provides memory integrity protection that helps against malicious hypervisor-based attacks (e.g., data replay, memory re-mapping, and more) and separates guests and the hypervisor from one other, according to AMD’s development materials.
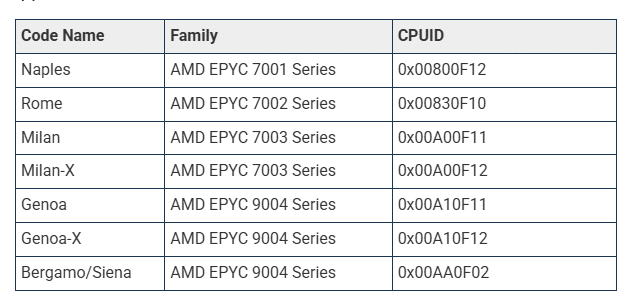
To verify that the mitigation has been installed appropriately, see if the microcode version or versions match those in the table below. Users must upgrade the system BIOS and restart in order to allow certification of the mitigation on certain systems, which additionally require a SEV firmware update for SEV-SNP attestation.
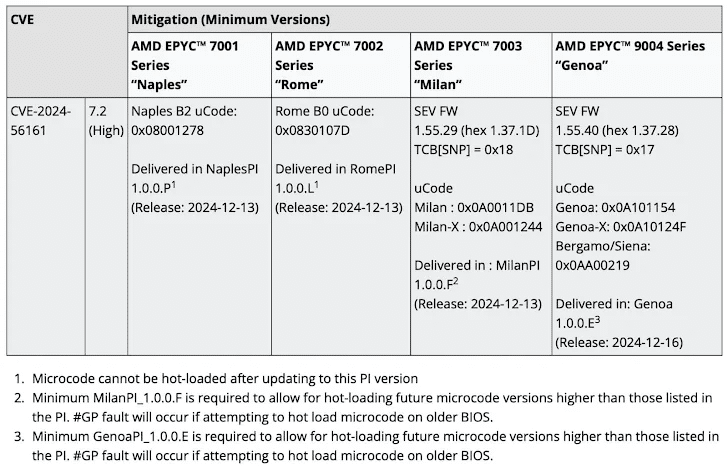
Understanding AMD SEV-SNP
An additional security feature called AMD SEV-SNP (Secure Nested Paging) is designed to isolate virtual machines from hypervisors and guard against side-channel and memory remapping attacks. SEV-SNP establishes a reliable execution environment for processing sensitive data by implementing memory integrity checks and encrypting virtual machine memory using distinct keys.
CVE-2024-56161, on the other hand, compromises these safeguards by permitting malicious microcode to alter CPU operation, which may reveal encrypted virtual machine data or permit privilege escalation.
It is necessary to upgrade the system BIOS images to include the updated firmware and microcode. SEV-SNP authentication may be enabled by rebooting the platform following the upgrade. This enables confidential guests to use authentication reports to confirm that mitigations are in effect.


