Summary

- A malicious programme called Atomic, also called Atomic macOS Stealer (AMOS), targets Mac OS X systems.
- Hackers now frequently use this software to steal cryptocurrency, passwords, and session tokens.
- The malware, which was formerly sold for $1000 per month, is now being offered for $3000 per month on open Telegram channels.
- It is said that the malware starts with the console hidden.
- Targets are being infected with AMOS by numerous threat actors using “SEO poisoning” or malvertising.
What is Atomic macOS Stealer (AMOS) ?
Its objective is to take private information from compromised systems, such as passwords, autofill information, and cryptocurrency wallet contents, and deliver it back to a threat actor.
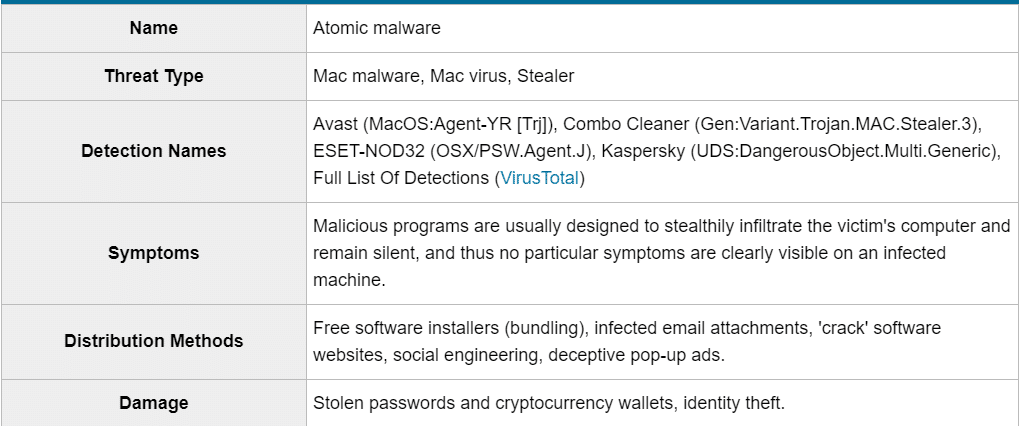
After running a sample of the Atomic Stealer on our test system, it faked a pop-up window and asked the user to input their password in order to gain access to System Preferences. This social engineering method allows the malware to obtain its initial piece of data.
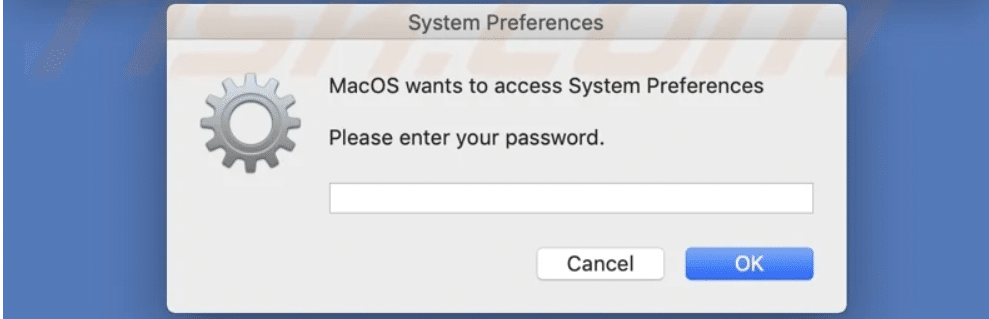
Additionally, Keychain, the Mac password management system, has data that can be extracted by the stealer. Credit card information, website and FTP usernames and passwords, Wi-Fi credentials, and other data can all be stored in Keychain.
How is it Being Distributed ?
Public Telegram channels are used for selling and promoting AMOS. It was offered for a “lifetime” licence at an undisclosed price of $1000 per month, but as of May 2024, it seemed to have gone up to $3000 per month.
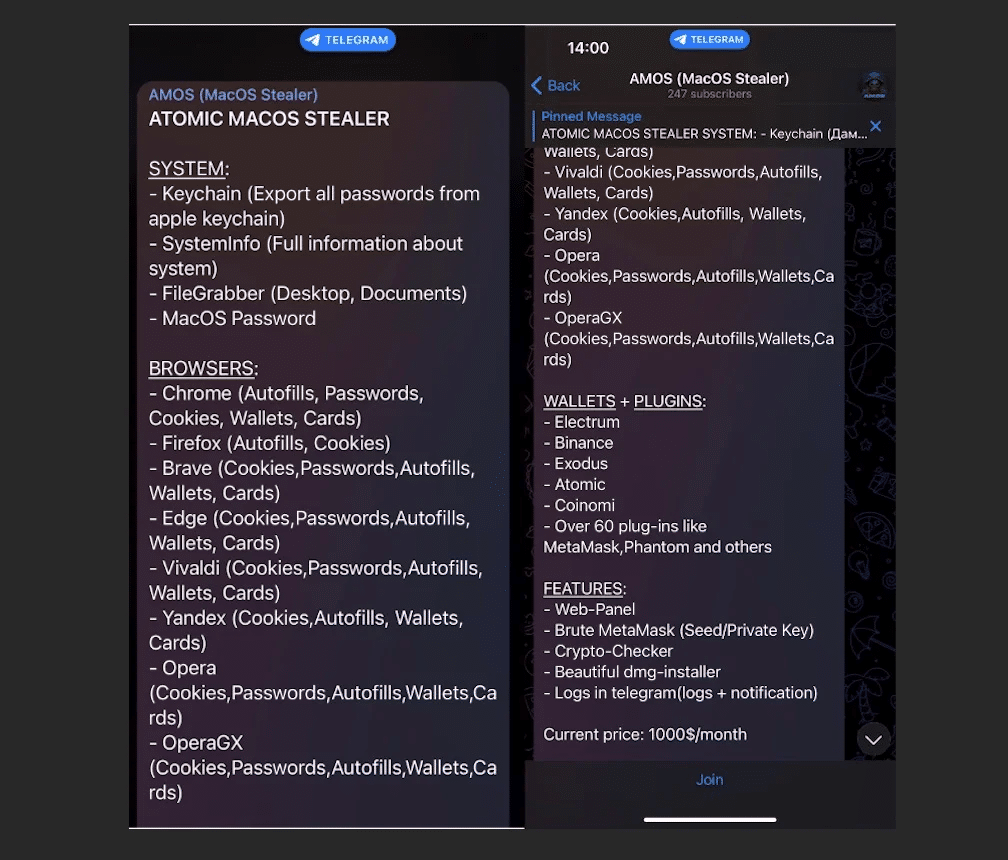
Infecting targets with SEO Poisoning, Malvertising, Installers
Through malvertising, numerous threat actors are able to infect targets with AMOS.
What is Malvertising ?
A tactic used by threat actors to steer users towards malicious websites that contain malware by abusing legitimate online advertisement systems.
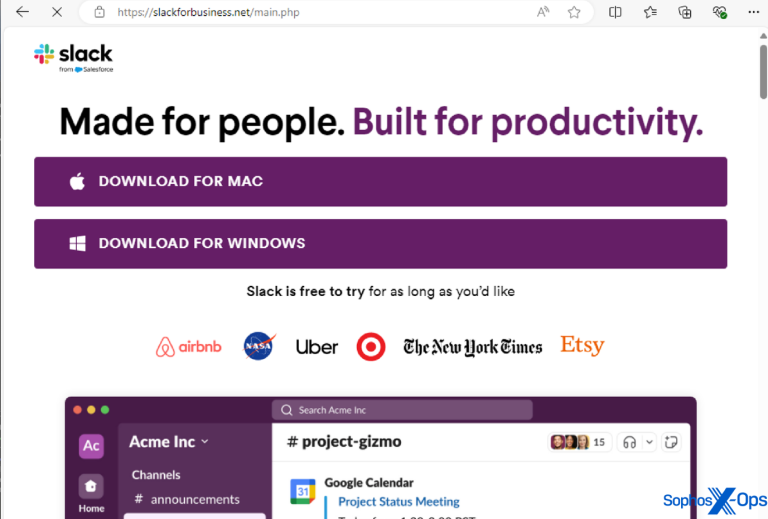
Pretending to be installers for trustworthy programmes, such as the Tor browser, or offering users access to cracked versions of well-known programmes, such as Photoshop CC, Notion, Microsoft Office, and others.
Malvertising by AMOS is also present on social media. For example, Sophosx saw a malvertising campaign on X.com that resulted in a phoney “Clean My Mac X” installer.
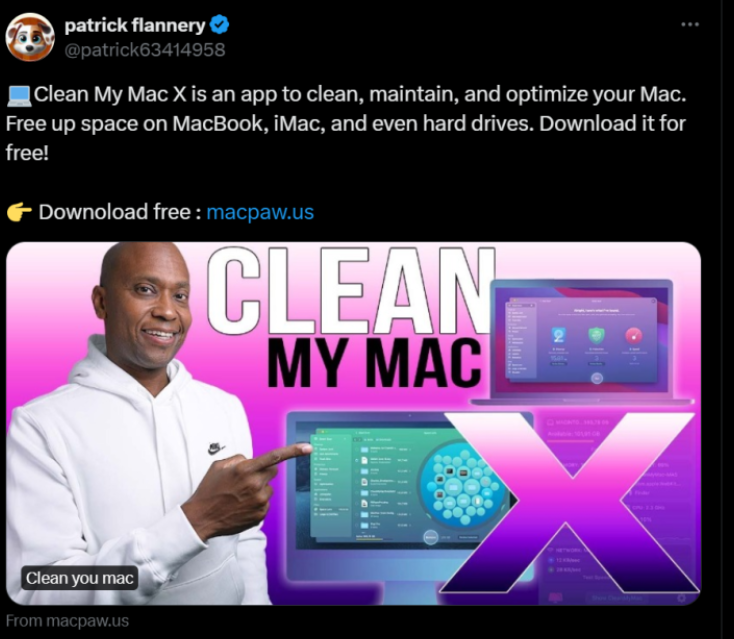
Threat actors host AMOS binaries via abusing reputable infrastructure, including GitHub.
Since the start more than a year ago, AMOS has changed. Its code has been obfuscated in order to prevent detection. Newer versions also include Python scripts that reimplement older routines, probably to evade discovery, instead of Mach-O executables.
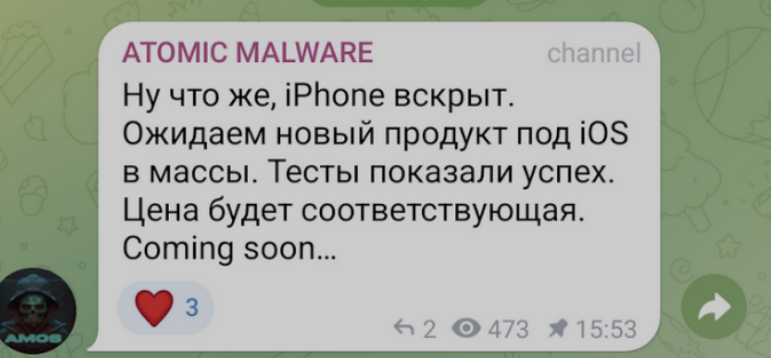
Creators of Atomic Malware now claim to have skills for iOS as well, according to Sophos.


