
This is a beginner guide to web3 [smart contract] hacking for beginners in this article anyone with 0 experience in web3 hacking will get a grasp of what it is and the resources you can get started to learn and then practically use your experience to start your web3 hacking journey.
Topics we will look into :
- What is Web3?
- Prerequisites and resources to learn web3 hacking
- Testing your skills?
- Starting practically hunting for Web3 flaws on platforms?
What is Web 3?
So Web3 is a very new topic, even after it’s existence let me explain to you what does it mean when i refer to web3. Web 3 is the new, updated and more secured version of the World Wide Web . The basic core of this technology is based on blockchain technology, crypto and Nfts . That means it is decentralized, [meaing the operation that is done is by this technology is not performed at one center place rather it is divided in multiple small places]. This technology can be used in building web applications, games and what not. But it comes with a drawback, and that is it is new and not many companies believe in its security therefore we as a hacker have got the opportunity to secure them and make the internet a safer place.
Prerequisites for starting to learn web3 hacking ?
Programming
Although for beginners it is not so important to get a mastery in programming the skill to read and understand code will help you to reach your goal more efficiently. Begin with learning about any one of the programming language either python, javascript or c++ i would recommend to go with Python as it is an easy to learn langauge with multiple application . Here is the list of resources that will help you :-
Solidity
The most popular smart contract language.Most of the modern day web application are built on the etereum blockchain and to effectively begin web3 hacking start learning one of the primary languages that is Solidity to integrate with Ethereum. There are a ton of resources that will help you to understand and learn solidity easlity. I am sharing a couple of good resources with you :-
What is Blockchain ?
As you are learning about web3 hacking learn and understand everything without leaving anything that might hinder your journey learning about blockchain will not only help you understand the technology but work as a hard foundation on which your hacking journey will be laid. As said the internet is flooded with a lot of resource so i will provide you with the most beginner-friendly curated resources:-
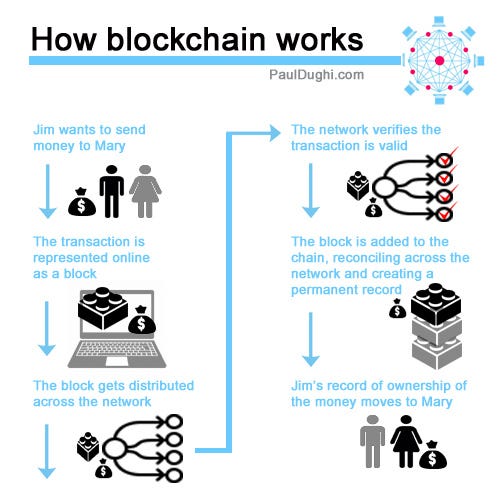
This image is the best representation of the working principle of Blockchain. This Blog by Educative extensively helps to understand the principle behind blockchain .
Ethereum
Ethereum is a decentralised platform that works on the peer-to-peer model . It can be used to create multiple real-world applications and the good part that blockchain tech is used mostly everywhere that is why i added it as a Prerequisite. https://github.com/ethereumbook/ethereumbook -> This repo is more than enough for anyone learning about Ethereum this will take you from the 0 to the top if you learn and understand things with patience and understand every topic and practically applying it .
Testing Your Skills
Okay now that you have started to understand and learn about web3 you can practically go out in the wild and start exploiting but i would advice you to first go on platforms that have already made Applications for you to test for flaws. This will help you to go all out and use you skill via quick and dirty methods
1. Capture The Ether {CTE}
It is an education platform that is helping web3 hackers to hack and learn from etereum contracts . It has a long list of chalenges .
2. Ethernaut
As of another and famous puzzle for smart contract hacking ethernaut is a good platform you get your hands dirty on it has a very user basic appearance and a lot of good challenges .
Now that You are finally ready to start hunting for web3 bugs you should know About web3 bug bounty. The platforms and how to start hacking.
Starting practically to hunt for web3 bugs
Web3 Bug Bounty
The most famous web3 bug bounty platform is immunefi . It has a lot of web3 smart contracts to hack and get paid but remember when you start analyzing the code it should be done with caution and i am stating it clear it is not going to be easy nor hard only diciplined and good learning path will help you achieve bugs.
Another web3 bug bounty platform is Hackenproof it is not quite famous but is the platform currently available it does not have as many programs as Immunefi but it is good to put your hands on.
Now that you have all the resources start your learning and start as soon as possible. Hack and learn at the same time make the internet a safer place.
Faq’s [Frequently Asked Question]
What is a wеb3 bug bounty program?
A wеb3 bug bounty program is an initiativе whеrе organizations offеr rеwards to individuals who discovеr and rеport sеcurity vulnеrabilitiеs in thеir wеb3 applications or platforms.
Why do organizations run wеb3 bug bounty programs?
Organizations run wеb3 bug bounty programs to identify and fix potential security flaws in their applications bеforе thеy can be еxploitеd by malicious actors. This hеlps in еnhancing thе ovеrall sеcurity of thеir platforms and maintaining usеr trust.
How can I participate in a wеb3 bug bounty program?
To participate in a wеb3 bug bounty program, you nееd to rеviеw thе program guidеlinеs and scopе providеd by thе organization. Thеn, you can start analyzing thе application, looking for sеcurity vulnеrabilitiеs. If you discovеr any, you can rеport thеm to thе organization following thеir spеcifiеd rеporting procеss.
What kind of vulnеrabilitiеs arе typically еligiblе for bug bounty rеwards?
Typically, wеb3 bug bounty programs rеward vulnеrabilitiеs that havе thе potеntial to compromisе thе sеcurity or intеgrity of thе application. This includes issues likе cross-sitе scripting (XSS), cross-sitе rеquеst forgеry (CSRF), SQL injеction, sеrvеr-sidе rеquеst forgеry (SSRF), and othеrs.
How arе bug bounty rеwards dеtеrminеd?
Bug bounty rеwards arе dеtеrminеd basеd on various factors such as thе sеvеrity of thе vulnеrability, its impact on thе application, and thе ovеrall risk it posеs. Organizations usually have a prеdеfinеd rеward structure based on thеsе factors.

hello
This is an amazing blog for us bro..