ALERT: Around in July, a new threat actor known as “Mad Liberator” appeared and is causing problems for businesses. While stealing data from the target device, the attack displays a fake Microsoft Windows update screen to distract everyone’s attention.
The group responsible for ransomware attacks use social engineering strategies and occasionally skips encrypting the stolen data.
About the Threat Actor
Since Mad Liberator focusses on data exfiltration, the team has not personally observed any instances of data encryption that can be linked to the organisation. However, data from watchguard.com indicates that the gang also engages in double extortion, which involves stealing data, encrypting the victim’s systems, and threatening to reveal the stolen material if the victim refuses to pay to decode it.

In an effort to increase victim pressure to pay, Mad Liberator runs a leak website where it posts victim details. The files are available for download “for free,” according to the website.
Targeting victims who utilise remote access tools placed on servers and endpoints, Mad Liberator uses social engineering techniques to get access to the environment. IT teams often utilise Anydesk, for example, to manage their environments, especially when collaborating with distant users or devices.
The Sophos X-Ops Incident Response team has been studying the strategies used by the Mad Liberator ransomware organisation.
In this case, the attackers are misusing legitimate software, which is Anydesk. The way we will demonstrate how the attackers abuse that application will probably apply to any remote access software.
How the attack operates
Anydesk functions by giving each device it is installed on a unique ID, in this example a ten-digit address. After installing the application on a device, the user has two options: either they can ask another user to take control of their device through a remote session, or they can request to access a distant device and take control by inputting the ID.
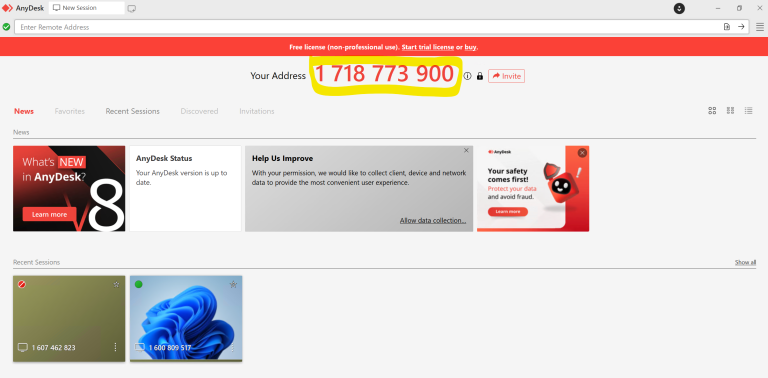
Whether or how the attacker targets a specific Anydesk ID is unknown at this time. Although it is potential to simply keep cycling through possible addresses until someone accepts a connection request, this seems a bit inefficient given that there may be 10 billion 10-digit numbers.
When the Incident Response team looked into a case, they discovered that the victim had not been in contact with the Mad Liberator attacker before the victim got an unwanted Anydesk connection request.
The user was not a well-known or conspicuously visible employee, and there was no discernible motive for their targeted behaviour.

The victim knew that the IT department of their firm used Anydesk. They clicked Accept, believing the inbound connection request to be just another routine IT department maintenance request.
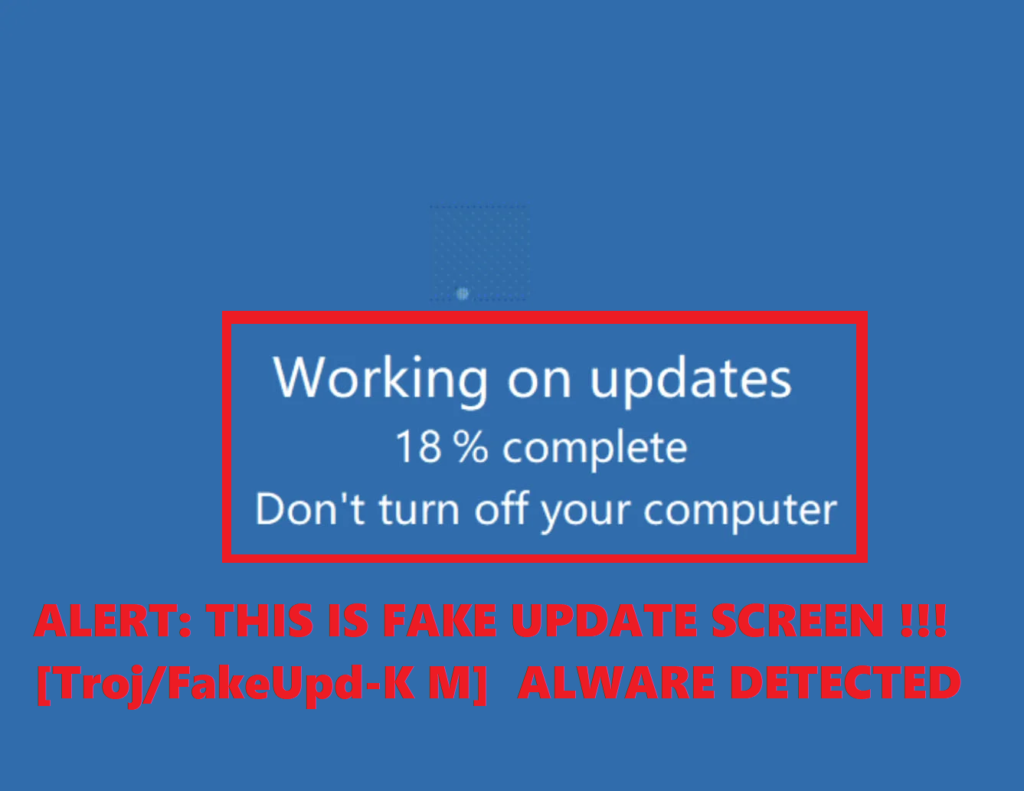
The attacker moved a binary to the victim’s device and ran it after the connection was made. According to our research, this file is called “Microsoft Windows Update” and has a SHA256 hash.
f4b9207ab2ea98774819892f11b412cb63f4e7fb4008ca9f9a59abc2440056fe
This binary was a very basic application that replicated the look and feel of a Windows Update splash screen. The moving screen gave the impression that the system was being updated.Troj/FakeUpd-K is a detection that Sophos has created for this specific malware.

Because the user might have accidentally hit the “Esc” key to end this straightforward programme, the attacker took advantage of a feature in Anydesk that prevented keyboard and mouse input.
Ransom Notes
The attacker then used another programme to generate several ransom notes after gaining control of the stolen files. It is interesting to notice that rather than being generated on the victim’s device, these ransom notes were created in different locations on a common network site that was linked to the device.
These ransom notes disclosed the existence of data theft and offered instructions on how the victim may pay the ransom to keep the stolen files secret. The victim’s screen was hidden from the attacker’s operations by the fake Windows Update screen.

In the event that the targeted company fails to reply within a day, their identity is made public on the extortion portal and they have seven days to get in touch with the threat actors.
All stolen files are now available on the Mad Liberator website, which presently contains a list of nine victims, five more days after the ultimatum was given and passed without a ransom payment.
The setting up of Anydesk Access Control Lists by administrators serves to significantly reduce the danger of this kind of attack by limiting connections from particular devices.


