Hi everyone, this is a crucial article since it details a dangerous false program that has been approved by the Google PlayStore and may be installed. Without further ado, let us get started. We are able to say that not everything that glitters is gold, as in this case, even though applications can be trusted, they still include harmful trojans and spyware.
” Many Android.FakeApp trojans are tasked with opening links to various sites, and from a technical point of view, such malware programs are quite primitive. When launched, they receive a command to load a specific web address. As a result, the users who have installed them see the contents of some unwanted site on their screens instead of the program or game they are expecting. However, sometimes notable samples can emerge among such fake applications: Android.FakeApp.1669, for example. “
DRWEB
Understanding The Virus : Android.FakeApp.1669
It makes use of the modified dnsjava library code, which enables it to obtain a configuration through a DNS request from the malicious DNS server. Android.FakeApp.1669 is characterised by a number of modifications that are presenting itself as separate apps on Google Play and other distribution platforms. Android devices are the target of this malware.
It alters its behaviour in response to commands from the C&C server, loading the contents of the target websites—typically an online casino—into its window rather than offering the stated capabilities.
As a result, the user sees the contents of the target website in the malware’s window rather than the expected functionality . The virus continues to function normally if the malicious DNS server does not send the TXT record to it.
Android.FakeApp.1669 uses modified code of the dnsjava Open Source library to send DNS requests.
Dr Web
List Of Fake Apps
| Name Of The App In Playstore | Number of downloads in Playstore |
|---|---|
| Split it: Checks and Tips | 1,000,000+ |
| FlashPage parser | 500,000+ |
| BeYummy – your cookbook | 100,000+ |
| Memogen | 100,000+ |
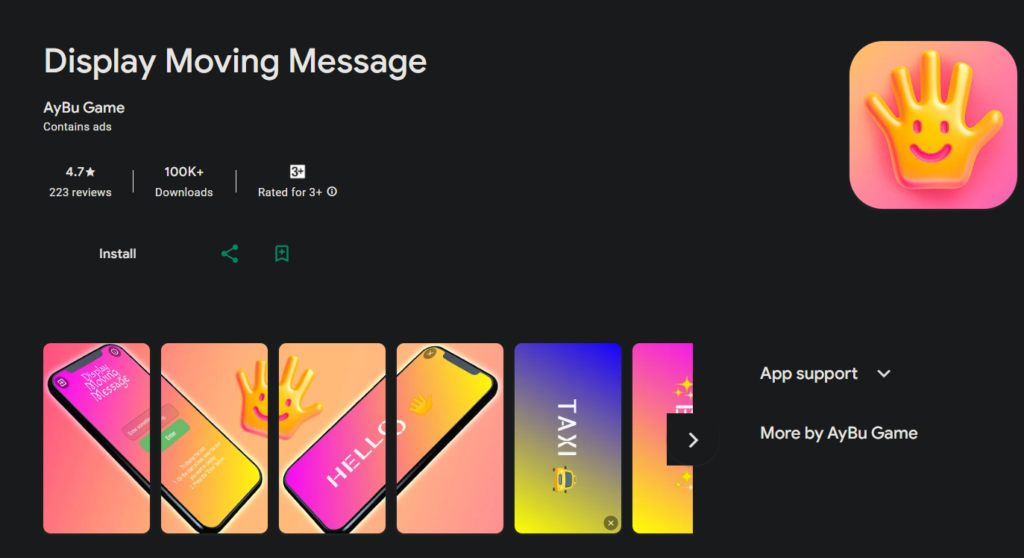
| Display Moving Message | 100,000+ |
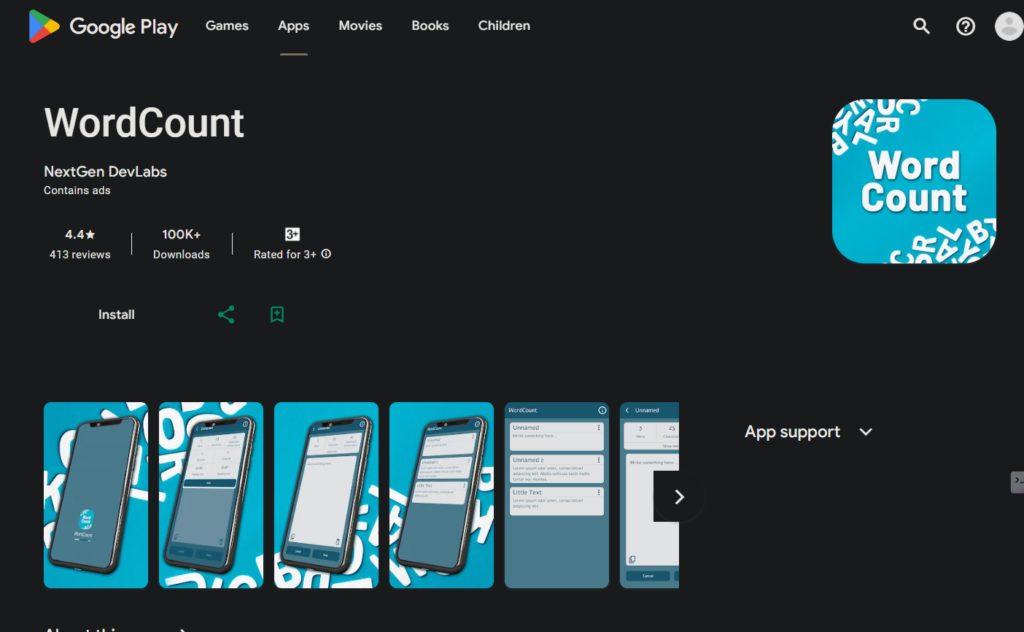
| WordCount | 100,000+ |
| Goal Achievement Planner | 100,000+ |
| DualText Compare | 100,000+ |
| Travel Memo | 100,000+ (is deleted) |
| DessertDreams Recipes | 50,000+ |
| Score Time | 10,000+ |
These programs, which ranged from productivity and personal finance helps to recipe and cookery collections, were touted as helpful resources. Upon launch, the applications would establish a connection with the DNS server to obtain a configuration that included the URL of the website to be shown.
Working Of These Appllication
Because each trojan modification is linked to an individual domain name, the DNS server may transmit each one its own configuration. Furthermore, each compromised device has a distinct sub-domain name for these target domains. Sensitive information about the device is among the encoded data they contain:
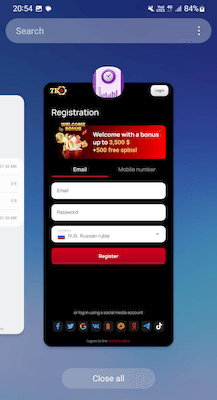
Device brand and model; screen size; ID (two-digit code that includes the malware installation time and a random number); whether the device’s battery is charging and what percentage of it is charged at the moment; and whether developer settings are enabled.
It is crucial that consumers read the evaluations that have been posted on these apps. Many customers have complained that the apps cause their smartphones to hang and spam advertisements, which allows the malware to run in the background.
It is essential to remove any compromised applications. To reduce any security risks, uninstall any apps on the list or similar programs that show suspicious behaviour. Another crucial step is to regularly check the permissions of apps. Users should check the permissions that apps ask for, preventing any extra access that can risk the security of their devices.
Additionally, as updates typically contain crucial security fixes, regularly updating the device and apps might help prevent some malware attacks.


