Hackingblogs Users need to be alert The discovery of EagleMsgSpy, a well-known Chinese spying program used by the Chinese intelligence agency and law enforcement to gather huge quantities of data from mobile devices, is the subject of this article, which is both vital and crucial. Several versions of the Android-focused tool have been received by Lookout, and internal papers retrieved from public directories on the attacker’s infrastructure also point at the presence of an iOS component that has not yet been discovered.
The Lookout Threat Lab’s researchers have identified a surveillance family called EagleMsgSpy
Understanding EagleMsgSpy
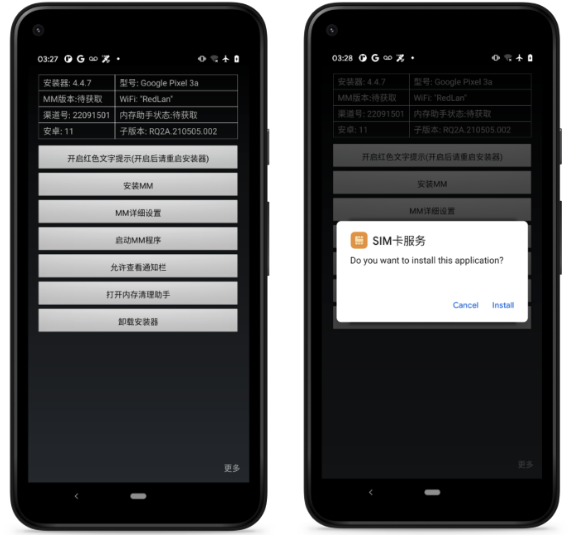
In order to start surveillance operations, EagleMsgSpy seems to need physical access to the device. A headless surveillance module that stays on the device and gathers a lot of private information is delivered by an installation component, which is likely to be used by law enforcement officials who were able to access the unlocked device.
The developers of this surveillance software are always working to keep it safe from detection and examination. A large amount of information about the victim device is gathered by the surveillance payload.
- Notification Services for People who listen and Accessibility track device usage and intercept messages
- gathers all messages from WeChat, WhatsApp, Viber, Telegram, and QQ and starts recording the device’s screen using the Media Projection service.
- takes screenshots
- records the device’s sound while it is being used.
- gathers call logs
- gathers contacts for devices
- Gathers SMS messages
- creates a list of the apps that are installed on the device.
- retrieves GPS coordinates and provides information about network and wifi connections.
- creates a list of external storage files.
- gathers bookmarks from the browser on the device.
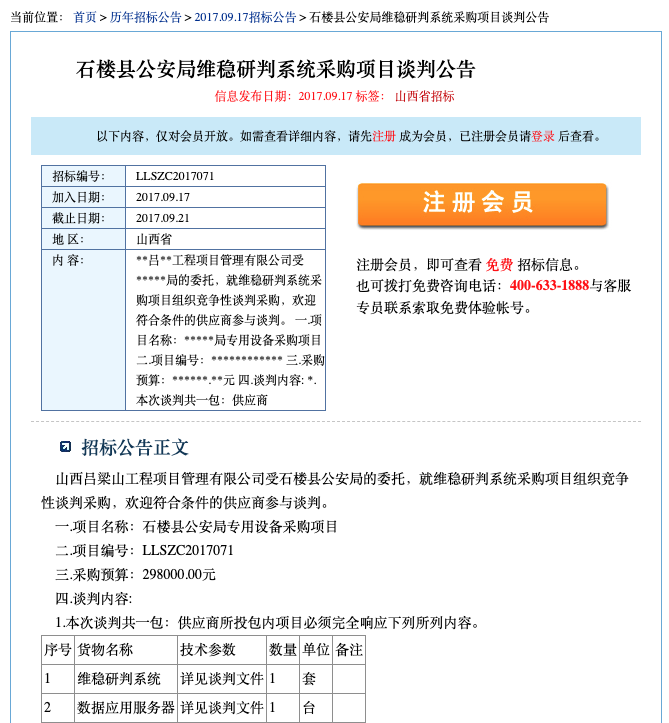
EagleMsgSpy C2 servers have landing pages that read “维稳研判系统” (Stability Maintenance Judgement System) and an administrator panel that requires user authentication. This. Following collection, the data is kept in a staging area within a device’s secret directory for potential leakage. Following compression and password protection, the data files are transmitted to the command-and-control (C2) server.
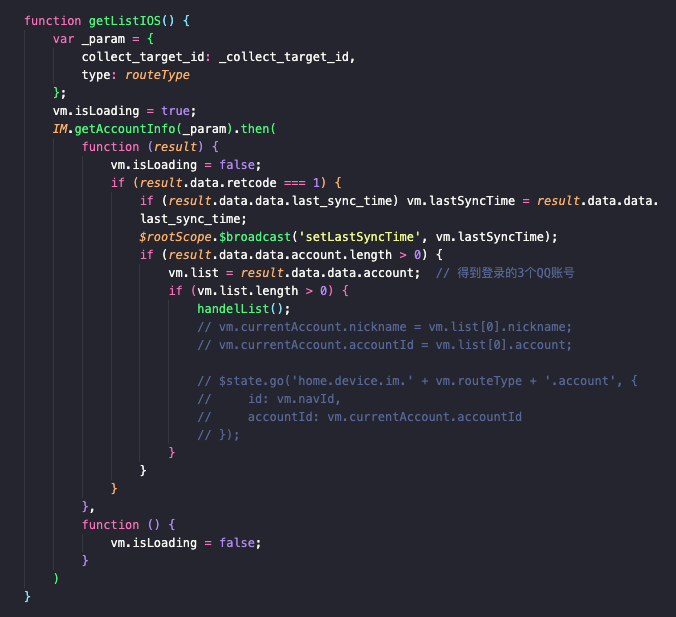
Several features that differentiate between Android and iOS device platforms were exposed in the source code. Although Lookout researchers have not yet been able to find it, this suggests that there is an iOS version of this monitoring program.
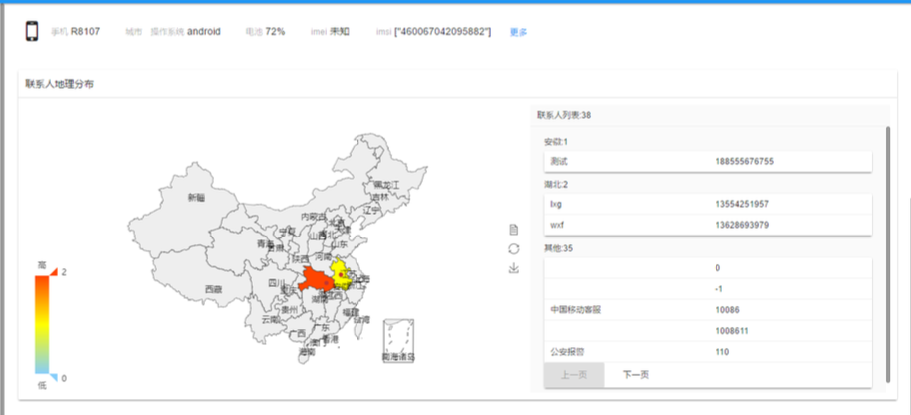
Many of the views that administrators can access via the Eagle web panel are also documented in the Eagle System User Manual.
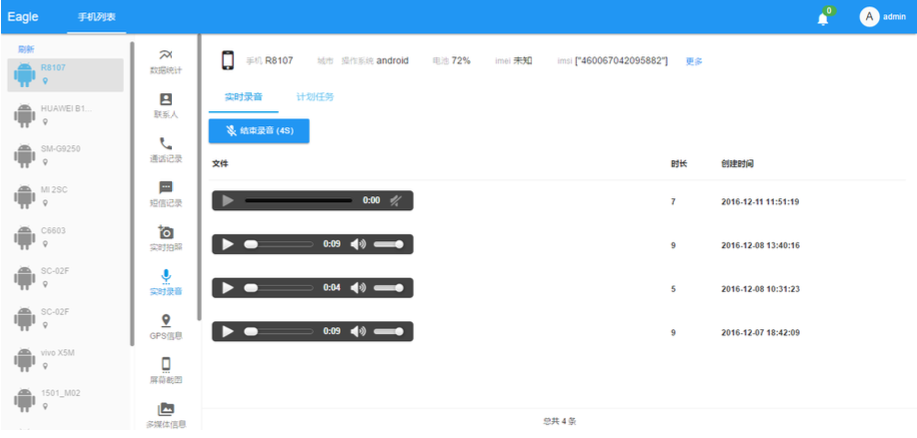
A private Chinese technology company, Wuhan Chinasoft Token Information Technology Co., Ltd. (武汉中软通证信は㊀术㜉限公司), has previously been linked to the IP address of one of the C2 servers that were found during the research. Promotional materials discovered during an OSINT investigation into this Wuhan-based IT company contained the root domain, tzsafe[.]com.
The fact that EagleMsgSpy C2s’ infrastructure matches with domains used by mainland China’s public security bureaus (公唉局) suggests that the surveillance tool was probably utilised by a number of people in the area.A hardcoded C2 address that operated as the resolving IP for two Chinese government websites at the time this EagleMsgSpy change was packaged is specified in an early EagleMsgSpy variant dated 2017.