Doctor Web’s cybersecurity specialists have discovered a significant malware campaign aimed at Android-based TV sets. A new Vo1d backdoor malware has been installed on over 1.3 million Android TV streaming boxes by threat actors, giving the attackers complete access over the devices.
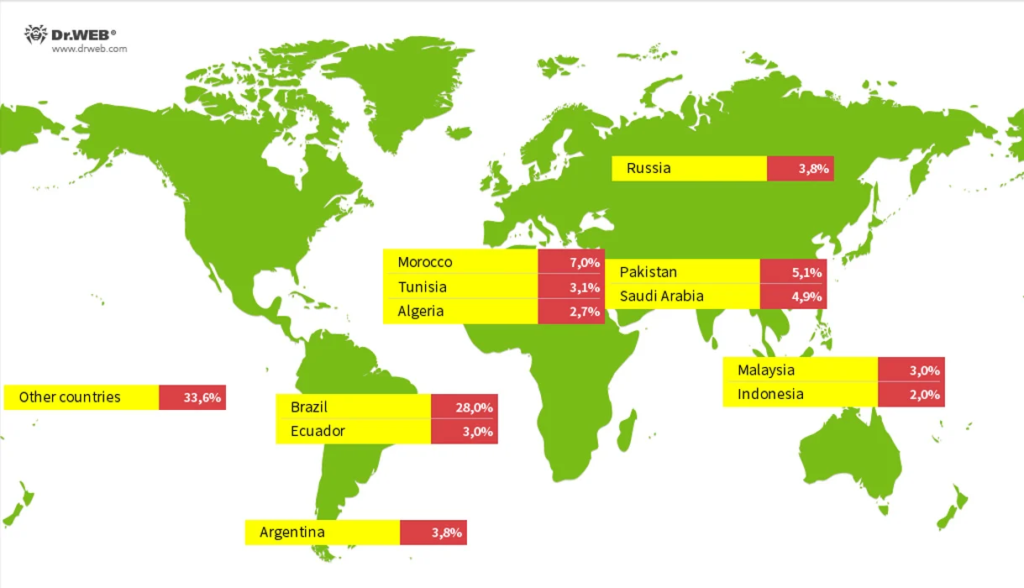
According to a recent analysis published on Dr.Web, researchers discovered that the Vo1d malware had infected 1.3 million devices across 200 countries. The majority of these devices were identified in Brazil, Morocco, Pakistan, Saudi Arabia, Russia, Argentina, Ecuador, Tunisia, Malaysia, Algeria, and Indonesia.
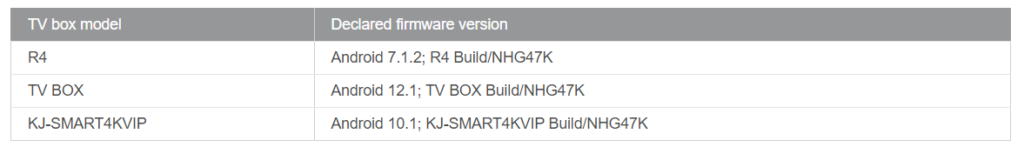
A number of individuals contacted Doctor Web in August 2024 when their Dr.Web antivirus software discovered changes to the system file area of their device. There was an issue with these models:
Similar indications of infection were seen in each patient. The install-recovery.sh and daemonsu files were modified, and new files named were added to the devices’ system files.
File Name Are as Follow :
install-recovery.shdaemonsu
Renamed As :
/system/xbin/vo1d,
/system/xbin/wd,
/system/bin/debuggerd,
/system/bin/debuggerd_realThe Android contains the vo1d and wd files. Trojan Vo1d. The attackers attempted to pass off one of the components as the system programme /system/bin/vold by changing the name’s “l” character to “1”.
Vulnerable versions
Vo1d most likely targets Android-based boxes because these devices run older versions of Android (7.1, 10, and 12) that have unpatched vulnerabilities. This is according to the cybersecurity firm.
Due to manufacturers’ decision to forego using more recent platform versions or customers’ perception that TV boxes are less vulnerable than other Android devices, security software may not be installed on these devices, leaving them vulnerable.
“One possible infection vector could be an attack by an intermediate malware that exploits operating system vulnerabilities to gain root privileges,”
Dr.Web
Google informed BleepingComputer that the compromised devices are utilising the Android Open Source Project (AOSP) rather than Android TV.
“These off-brand devices discovered to be infected were not Play Protect certified Android devices. If a device isn’t Play Protect certified, Google doesn’t have a record of security and compatibility test results. Play Protect certified Android devices undergo extensive testing to ensure quality and user safety. To help you confirm whether or not a device is built with Android TV OS and Play Protect certified, our Android TV website provides the most up-to-date list of partners. You can also take these steps to check if your device is Play Protect certified.”
Google spokesperson.
Method of Infection
Android.Vo1d makes use of a number of techniques to guarantee its operation on
- Adding new components to the install-recovery.sh file, which is launched during system starting, is one way to modify the startup script.
- Using Root Privileges: Changes the daemonsu file associated with root access to run malware at boot.
- Replace system daemon: To run its components, a malicious script is substituted for the system daemon debugger.
= Void captures over a million Android TV boxes -- Indicators of compromise == Samples All hashes are SHA1 === Known Android.Vo1d.1 variants (/system/xbin/vo1d) |=== | SHA-1 | Decrypted payload SHA-1 | f3732871371819532416cf2ec03ea103a3d61802 | 675f9a34f6f8dc887e47aa85fffda41c178eb186 | 637c491d29eb87a30d22a7db1ccb38ad447c8de8 | 9a8b7a85742330970e067f2b80ada9e295b0e035 | 42def5b7eb8b1bcc727739cca98efe42c022a3f6 | 4b1135c6cade7e17548982338bfa9382e3c234f0 |=== === Known Android.Vo1d.3 variants (/system/xbin/wd) |=== | SHA-1 | Decrypted payload SHA-1 | 8399c41b0d24c30391d7fba6b634ba29c0440007 | ccf8c0cb83160a20fa4c89b028fb63884f7b6a86 | e5b16486eebd6c6f7c45197f530e854a4f1373dd | cd3c8d0ca99400c86e7e4943e85669f291c52a74 | 51bd967bd7d59a8a9db8083094603a9d10e61ded | 3e941c34af4e07496f515c35eddaff145e06c42a | 0b3c8113e996ac4e08552761731f9f97b8f0f6a2 | 2d2ceddafbce5afe79e3424ebc32dea4d5dff1fe | 0d51c034a6deda4d2db21c5852b8ceb8a1e1c68b | 51d17a5a1950db3236c9db3249ab0dcb03223d11 | 9dcc109ac2c5f873ece422aed0687ba21d594e9b | e05c1338426a07a49eb3491e08abbc3f96b047b3 | e5406ae7482c0062cedafbd118a493ab8b7fe530 | c53a76845a78ec9b613442a208b5b2ea8fbecc91 |=== === Known Android.Vo1d.5 variants (/data/google/daemon) |=== | SHA-1 | Decrypted payload SHA-1 | e34c6a13ccbecf7560d4cb8a32872b8aabd5f8db | 825df85d82a3de5e4bf6347dcba47e3ec48dbd52 | 3e21821a1e6edb684f3931d685b908d4a8df3f19 | 6707cbb2b4e09911c4ada7e24c05e4fbd66a7851 | b1cf85aaf1a355677534ea12c19b034c656804ec | 89788eabef15303c142fff33dfd560e619595ae5 | ed975255eba30345de74936e24b9b3090f26ed7e | 182939085a9aa1d6f0e60da31b200cd644522748 | 3ce81fbb1d968e01e970c4c673a7eeb61c247c85 | 436f200abfc0db4ae6138b0b2f1ab67af57ca506 | 0c7f9f33a40a6028dbef416b2385876c87f1bd48 | df71b68c4172ef7f23949c643550c40d0f81fa83 | 6e06d0decf5e211183a751b206dd533f91c13b22 | b6a00590a3b0b175fa2ec910744875dd5be995ac |=== === Known Android.Vo1d.1.origin variants (com.google.android.services) |=== | SHA-1 | 7f87f9f059a58eb830d59af5bcb29c612b2a6ccf | 9fcdfb9cadabe12283a002755a27a4a68a101949 | 25f93476cb8dc6a7f727a88ece0c5a0c19157c0b | 3a4d90b9911e7e582cf3279b15f2f822a5bb2823 | b315be9d64e22960f6072aac60538b13d50da054 | 618b98eb97f38ffa7b384b0932fd4b92c8877f60 | b474c279da7b08fd64f92b0781e2663bf6cbb4b6 |=== == Network indicators === Domains ---- hxxp[:]//meiboot[.]com/ hxxp[:]//bitemores[.]com/ hxxp[:]//6f33933ce4a5c0e1b32fea736a61351a[.]com/ hxxp[:]//catmos99[.]com:81/ ----


