Hey hackers, were you aware that a significant zero-day attack recently affected Viasat’s satellite modems? A serious flaw in these devices, which are essential for satellite internet, could allow attackers to run remote code without authentication. Read on to learn how this attack operates and why it is important it will change the face of embedded device security.

Executive Summary : “An attacker might change the responses in order to inject code that causes a buffer overflow on the modem if they manage to obtain access to the WAN interface and intercept the Dynamic DNS (DDNS) communication between the modem and DDNS services. This vulnerability does not, however, affect users who have not activated Dynamic DNS on their devices.“


What Are Viasat Satellite Modems and Why Should You Care?
Viasat offers satellite internet services to a variety of businesses, including rural broadband and military communications. These services rely on their modems, which are used in situations where security is of the utmost importance.
Given the large number of devices in use, modem security is essential, particularly since any malfunction could have significant implications.
The Discovery: How This Zero-Day Flaw Was Found
The ONEKEY Research Lab was responsible for the unexpected discovery of the vulnerability. The binary zero-day analysis feature, which automatically checks firmware for any vulnerabilities, had just been activated by one of their clients. The system discovered a stack buffer overflow in the Viasat firmware while doing its routine checks.

A stack buffer overflow: what is it and why is it dangerous? To put it simply, it is a method by which hackers transfer more data than a program can process, leading it to “overflow” into memory spaces that should not be accessible. This can provide hackers the ability to remotely run malicious code, which is precisely what this bug made possible.
The Vulnerability: CVE-2024-6198 Explained
Remote unauthenticated attacker on the WAN interface with the ability to intercept traffic can gain remote code execution on the device by intercepting and modifying HTTP responses returned by remote endpoints (dyndns, tzo) contacted by the binary.Customers that have not enabled Dynamic DNS on their modem are not vulnerable.
Said Researchers At ONEKEY

Officially known as CVE-2024-6198, the vulnerability impacts Viasat satellite modems, particularly those with the RM5110, RM5111, EG1000, and RG1100 types. Because of its support for remote code execution (RCE), attackers can execute code on the device without requiring authentication.




The SNORE web interface yes, that is what it is called handles incoming HTTP requests poorly, which leads to this problem.
By intercepting HTTP communication between the Viasat terminal and either echo.tzo.com or checkip.dyndns.org, a remote unauthenticated attacker could return an HTTP response that contains more bytes than the public_ip buffer can hold, leading to a stack buffer overflow.
Said ONEKEY Researchers
- The SNORE interface fails to accurately verify the amount of incoming data when processing queries. When the request data exceeds the buffer size, this results in a stack buffer overflow.
- The buffer might overflow and overwrite important portions of the device’s memory if an attacker sent a carefully constructed HTTP request, such as this: http://192.168.100.1:9882/snore/blackboxes/ followed by 512 repeated characters
- Using wild code execution and bypassing of standard authentication, this overflow could grant attackers control of the device.
How Does This Affect You?
There could be serious consequences if you are using one of the impacted devices. This flaw could be used by an attacker to access the modem without authorization. remotely run malicious code with the ability to take over vital infrastructure, interfere with device-to-device connection or modify traffic.
You are safe if your modem is not using Dynamic DNS (DDNS); only devices that have DDNS enabled are vulnerable.
What Is Dynamic DNS ?
When the IP address of the device linked to a domain name changes, a service called Dynamic DNS (DDNS) instantly updates the DNS (Domain Name System) records for that domain name.
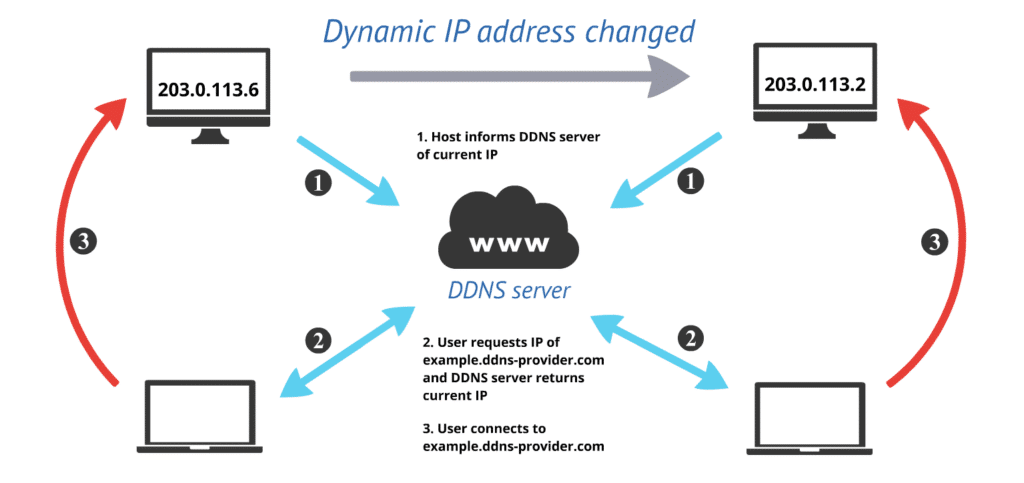
In order to enable people to visit websites using memorable domain names rather than complex numerical IP addresses, DNS typically maps domain names (such as example.com) to static IP addresses.The public IP address that an Internet service provider (ISP) assigns to a network can change frequently, especially in networks that are homes or small business networks. We call this a dynamic IP address.
Even if an IP address changes, DDNS enables a device (such as a server or router) to maintain its domain name pointing to the proper location.
How Was This Fixed?
Viasat took quick action to fix the vulnerability after it was found. Viasat was first notified of the defect in May 2024.Version 4.3.0.3 of the vulnerable modems was issued with a patch.Viasat distributed the patch to users through over-the-air updates, so all you need to do is keep your device online and avoid any manual labor.


