We will begin a five-day series on the fundamentals of cryptography today. Why is it basic? Because I only want to light the fire, not confuse you with complex technical language or complicated arithmetic. I would like to turn the switch. You will be the one to follow the path, dig deeper, and fully understand the power of cryptography once it is activated. And do not fear, when you are ready to level up, I will be right here with deeper knowledge. But for the time being, let us keep things straightforward, understandable, and above all useful.
Coach & Instructor, Dipanshu Kumar (Hackingblogs)

What is Cryptography?
In the digital age, cryptography is how we protect our secrets. When necessary, it transforms readable data (plaintext) into unintelligible code (ciphertext) and back again.

We can build trust a system that does not trust anyone by using cryptography.
It is about control, proof, integrity, and privacy, not just about hiding data. Cryptography provides us with the means to protect communication, confirm identities, prevent manipulation, and show something is true in a world where every digital transaction could be intercepted, altered, or falsified.
Famous Personality You Should Know Who Contributed in Cryptography
Claude Shannon – The Father of Modern Cryptography

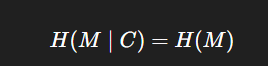
Because of his groundbreaking contributions to information theory, Claude Shannon is regarded as the father of modern cryptography. The main idea is perfect secrecy, in which the ciphertext provides no knowledge into the plaintext.
Where H is entropy, M is the message, and C is the ciphertext.
→ This means: knowing the ciphertext reveals nothing about the message.
Whitfield Diffie & Martin Hellman – Public Key Revolution

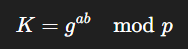
The creation of asymmetric cryptography (Diffie–Hellman Key Exchange) is what Whitfield Diffie and Martin Hellma are famous for.
Where:
- g is a generator,
- a, b are private keys,
- p is a large prime,
- K becomes the shared secret key.
→ This allowed two parties to agree on a key over an insecure channel—a massive breakthrough.
Ron Rivest, Adi Shamir, Leonard Adleman – Creators of RSA
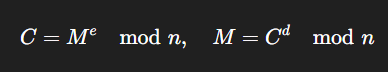
Leonard Adleman, Adi Shamir, and Ron Rivest Known For: The foundation of secure web traffic, the RSA algorithm.
Where:
- M is the plaintext,
- C is the ciphertext,
- e, d, and n are components of the public/private keys.
Quick Look At The History Of Using Cryptography In Ancient Times, WWII

In the past, Julius Caesar protected Roman military communications with a straightforward letter-shifting technique that is now known as the Caesar Cipher. An important turning point in World War II occurred when Allied cryptographers cracked the German Enigma machine.

These days, encryption protects everything, including online banking and WhatsApp conversations.
Why Does Cryptography Matter in Cybersecurity?
| 🔧 Use Case | 🔒 Role of Cryptography |
|---|---|
| Online Banking | Secures transactions and sensitive data (via HTTPS) |
| Messaging Apps | Protects conversations with end-to-end encryption |
| Password Storage | Uses hashing so passwords aren’t stored in plain text |
| VPN Services | Encrypts your internet traffic from spying eyes |
| Email Security | Validates sender identity through digital signatures |
Key Terms You’ll Hear Often
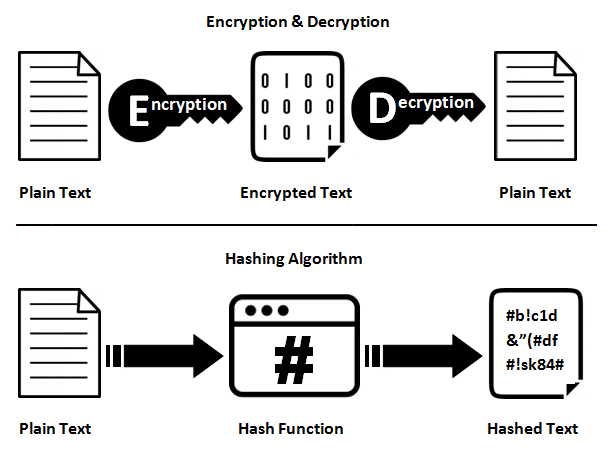
Encryption
The process of using a key to transform readable data (plaintext) into unreadable data (ciphertext). Even if someone else intercepts your chats or information, it is what keeps them secret.
Decryption
Encryption in reverse. If you have the right key, it can turn ciphertext back into plaintext.
Key
Both encryption and decryption employ a secret value. Consider it a kind of password that regulates the way data gets jumbled and unjumbled.
The same key is used for both encryption and decryption in symmetric encryption. A private key is used for decryption and a public key for encryption in asymmetric encryption.
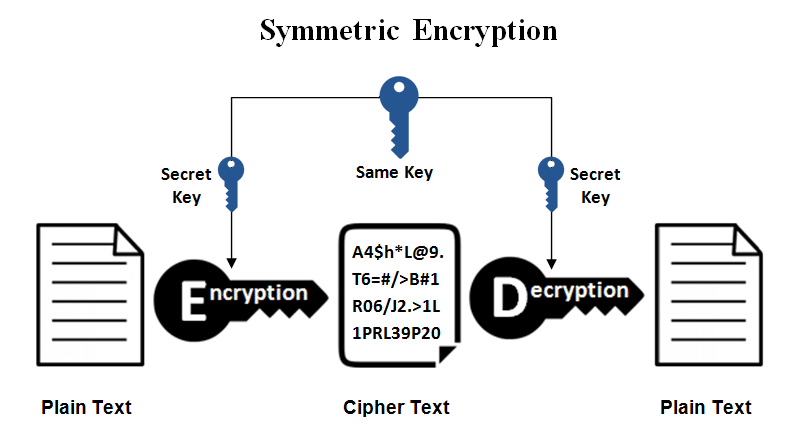
Ciphertext

After encryption, the output became jumbled and meaningles. It appears to be nonsense without the key.
Hashing
A one-way procedure that creates a hash, which is a fixed-length string from data. Hashing cannot be reversed, in comparison to encryption.
Used in: password storage, data integrity checks, blockchain.
Example: The hash of “password123” might look like
ef92b778ba5c...
Same input = same hash, but you can’t go backward.
Salting
To ensure that each hash is different even when users have the same password, random data is added to passwords prior to hashing.
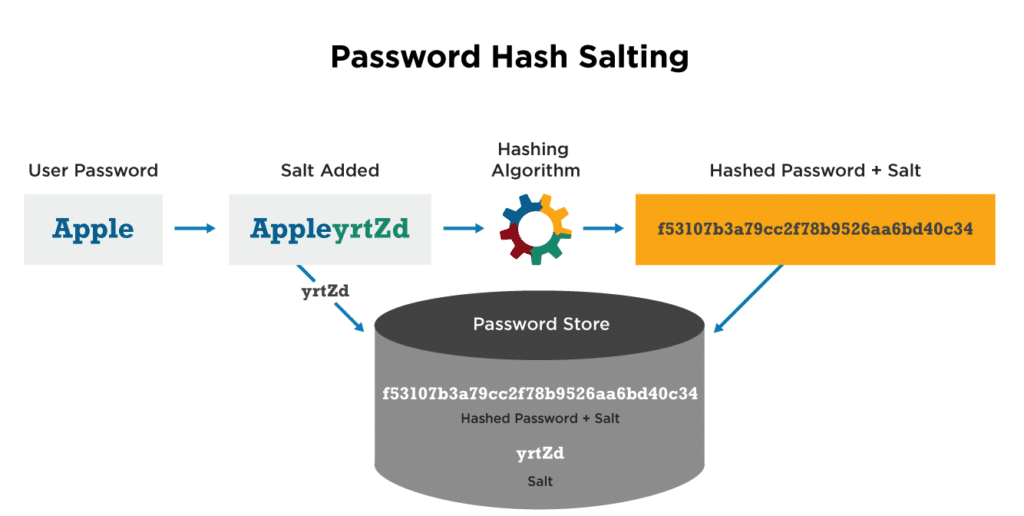
Digital Signature
A cryptographic method of proving integrity and reliability. It is similar to signing a paper, but much safer and digital. Used in: secure email, software verification, blockchain transactions.
Public & Private Keys
Used in asymmetric encryption:
- The public key is shared with anyone.
- The private key is kept secret.
You encrypt with one and decrypt with the other.
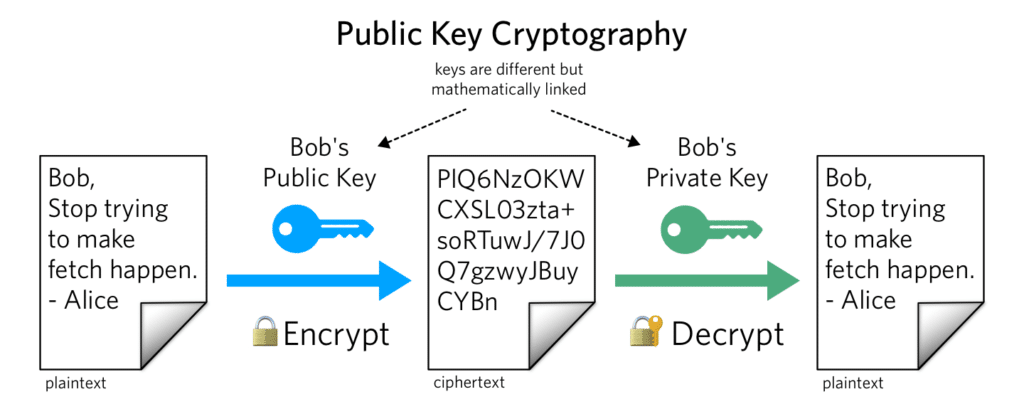
Public key = lock
Private key = key that opens the lock
Different Types of Cryptography (No Deep Dive Yet!)
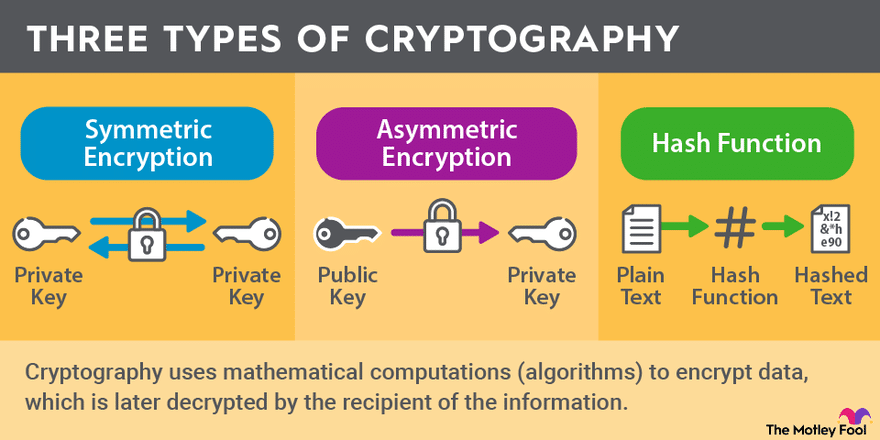
- Symmetric Encryption: Same key used to lock and unlock the data.
- Asymmetric Encryption: Uses two keys—one to encrypt, another to decrypt.
- Hashing: No key needed. One-way function, can’t be reversed.
Coming Up Tomorrow (Day 2) The fundamental components keys, ciphers, and algorithms will be broken down, along with their definitions, functions, and applications in practical systems.


