Affiliates of the RansomHub ransomware have compromised over 210 victims from a variety of important U.S. infrastructure sectors since the malware first appeared in February 2024.
Understanding RansomHub

This relatively recent ransomware-as-a-service (RaaS) method demands victims to keep stolen files secret and, if agreements fail, distributes the information to the highest bidder. The ransomware gang was also found to be interested in purchasing the source code for the Knight ransomware, but their primary emphasis is blackmail based on data theft.
As RansomHub continues to accumulate hundreds of victims and hunt for senior executives from the bankrupt LockBit and ALPHV operations, security and law enforcement authorities in the US believe it is time to officially warn about the group striving for supremacy in ransomware.
Since starting up in February of this year, RansomHub has reportedly amassed at least 210 victims, according to the security advice from CISA, the FBI, the HHS, and the MS-ISAC.
FBI threat response initiatives and reports from third parties as late as August of 2024. The alert #StopRansomware: RansomHub Ransomware has comprehensive details about this threat, including with related IOCs and TTPs.
Damages Leveraged By RansomHub
RansomHub was founded in February 2024 and has since encrypted and exfiltrated data from at least 210 victims, including those in the critical manufacturing, transportation, and communications infrastructure sectors as well as those in the fields of water and wastewater, information technology, government services and facilities, healthcare and public health, emergency services, food and agriculture, and financial services.
“The authoring organizations do not encourage paying a ransom, as payment does not guarantee victim files will be recovered,”
federal agencies
Analysis Of Scandal Performed
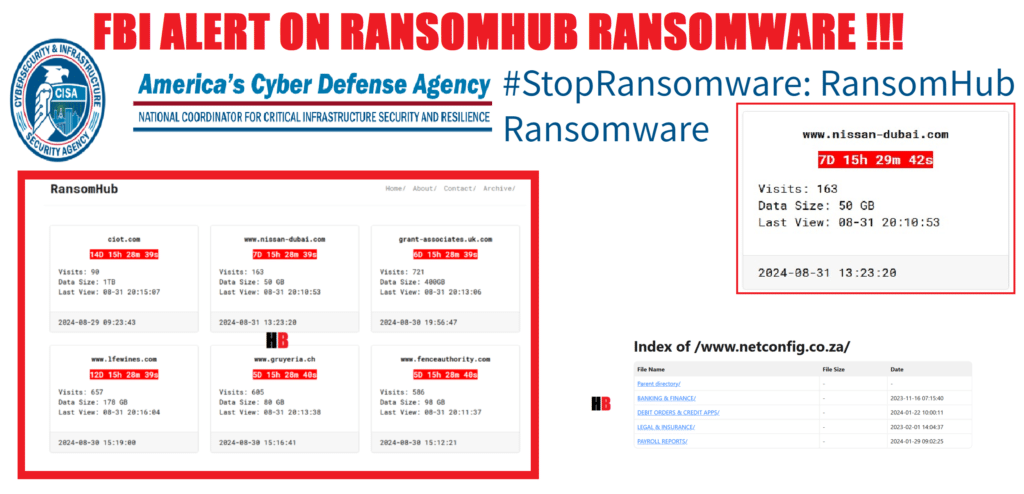
After a bit of lokking and finding the site we came to find that the site uses a timer with the victim’s detail and if the victims fail to respond the data is published. Hackingblogs was able to discover some information while monitoring the ransomware site.

We See that still there are sites which represent a timer which shows that they have been infiltrated by the Ransomhub ransomware. Well Scrolling down we see there are data’s referring to sites like Nissan Dubai Branches – https://nissan-dubai.com that have been infiltrated.


The Ransomware Site Sites that the data exfiltrated out is around – 50gb. Here we have data for and exposed victims site on the website www.netconfig.co.za


On Visiting The Link We Find out the Following Data :

On Futher Examination we find out that all data about the business was uploaded as they failed to meet the demands of the ransomware so it is important to understand that this group basically works on extrotion of important data.
Safeguarding Yourself: FBI Guidelines
The organisations who authored this cybersecurity warning advise network defenders to apply the suggestions found in the Mitigations section in order to lessen the probability and severity of ransomware events.
How do these ransomware take access ?
Typically, ransomHub affiliates utilise techniques like phishing emails [T1566], exploiting known vulnerabilities [T1190], and password spraying [T1110.003] to infect internet-facing systems and user endpoints. Data breaches are the source of accounts that are targeted by password spraying. One can acquire proof-of-concept exploits from resources like GitHub [T1588.005] and ExploitDB. The following CVEs have been used to identify exploits:
- Citrix ADC (NetScaler) Remote Code Execution.
CVE-2023-27997 (CWE-787 | CWE-122)
- A heap-based buffer overflow vulnerability
- The Java OpenWire protocol marshaller, such as in Apache ActiveMQ, is vulnerable to Remote Code Execution.
- A vulnerability in publicly accessible Confluence Data Center and Server instances that allows the creation of unauthorized Confluence administrator accounts and access to Confluence instances
CVE-2023-46747 (CWE-306 | CWE-288)
- Undisclosed requests may bypass configuration utility authentication
Affiliates of RansomHub do out network scanning using programmes like AngryIPScanner, Nmap, and PowerShell-based living off the land techniques.
Encrytption
Intermittent encryption is used by RansomHub, which encrypts files in blocks of 0x100000 bytes and skips 0x200000 bytes of data in between. Files with a size of less than 0x100000 bytes are fully encrypted. 58 (0x3A) bytes of data are appended to files at the conclusion. A value in this data is probably a component of an encryption or decryption key. Below is a list of the appended 0x3A bytes’ structure along with screenshots from three separate encrypted files.

Usually, executable files are not encrypted by the ransomware executable. A ransom letter, commonly named How To Restore Your Files.txt, is placed on the hacked machine along with a random file extension appended to file names. The ransomware executable usually uses the vssadmin.exe utility to erase volume shadow copies in order to further impede system recovery [T1490].
Important Signs To Notice



