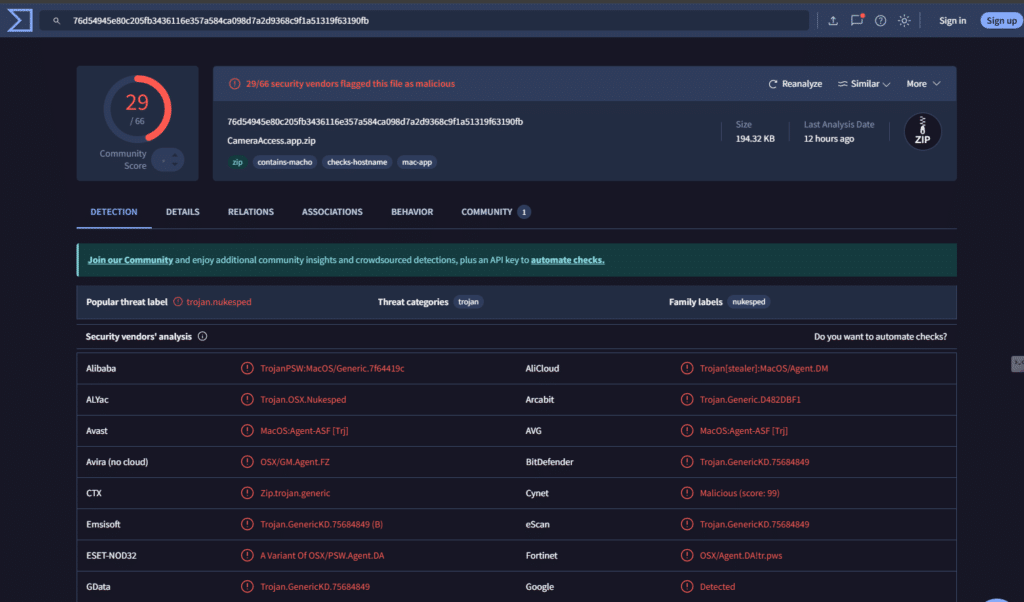
Hi, my dear Hackingblogs readers! The malware that is wreaking havoc on MacOS users will be the topic of today’s article, but before we do that, I would like you to read this report first because it is relevant to the one we will be discussing today.
A Short Glimpse On Today’s Topic
Apple upgraded its XProtect tool last week to stop many macOS Ferret family variations that have been connected to the Spreading Interview malware campaign from North Korea. This campaign uses job interview scams to trick victims into installing malware, which is frequently passed off as software updates.
New malware samples known as “FlexibleFerret,” despite Apple’s update addressing some dangers, are still undiscovered. Key indicators for threat hunters and defenders are provided in this piece, which also examines these new threats and summarises previous findings.
A social engineering technique is used at the start of the campaign. Hackers use fake job interview procedures to trick their victims, who are frequently job searchers, into downloading malware. They transmit a link, such as a fake virtual conference app, that seems like it needs a software update.
Notably, the “Ferret” malware family was first identified in September 2024 and targeted Blockchain specialists with fake video conferences and employment frauds. SentinelLabs found the most recent form, “FlexibleFerret,” which demonstrates how hackers are always altering their techniques to evade detection.
Let’s Talk How This Thing Works
Initial Steps Of Victimising
Usually, targets are invited to connect with an interviewer via a link that displays an error notice and requests that they install or update a necessary piece of software, like CameraAccess or VCam for virtual meetings.
Researchers found malware that installed an executable and persistence agent under the name of a Google Chrome update, as well as executing a malicious shell script. A backdoor that poses as an operating system file with the name com.apple.secd (also known as FRIENDLYFERRET) and the ChromeUpdate and CameraAccess persistence modules (also known as FROSTYFERRET_UI) are among the elements of this malware campaign that were targeted by Apple’s signature update last week.
21 22 3.__TEXT.__cstring ascii https://api.ipify.org
39 40 3.__TEXT.__cstring ascii https://api.dropboxapi.com/oauth2/token
45 46 3.__TEXT.__cstring ascii https://content.dropboxapi.com/2/files/uploadFERRET and other recent DPRK efforts share the use of api.ipify.org to determine the host’s public IP address and Dropbox for exfiltration.
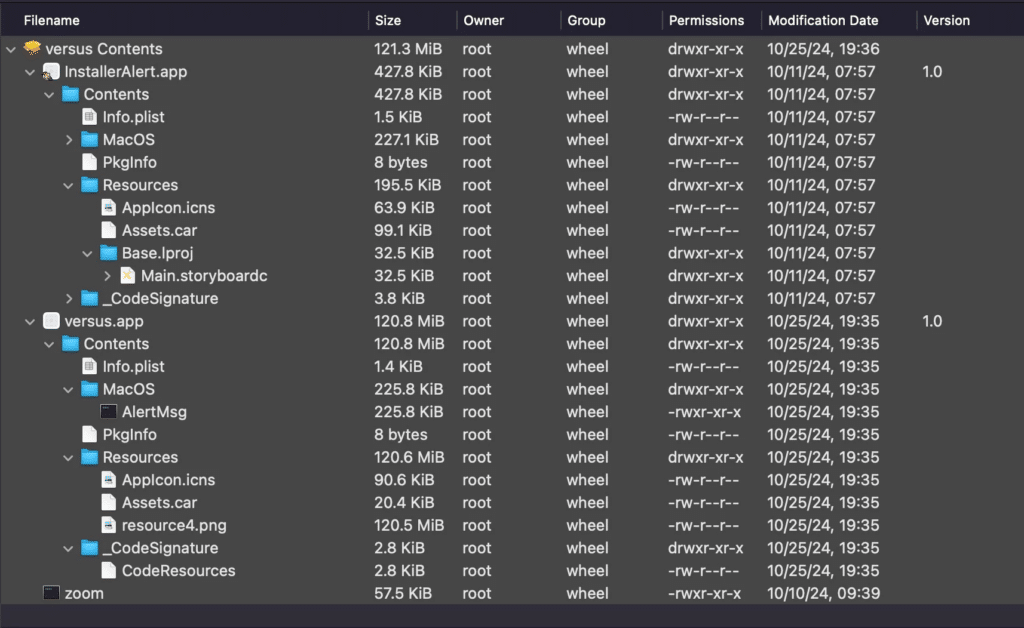
In their blog post, Sentinelone said that they had been monitoring malware found by earlier researchers and examining a ChromeUpdate sample variant known as Mac-Installer.InstallerAlert.
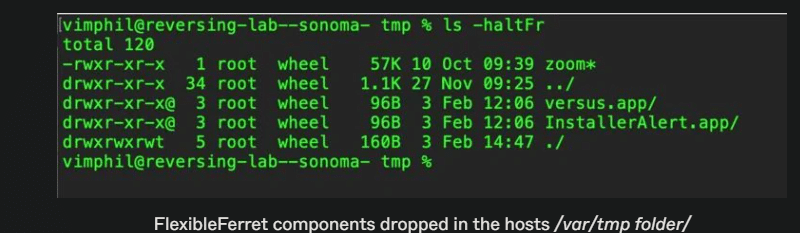
They stated The installer package uses the postinstall script to drop and run many components in /var/tmp/ after obtaining elevated access. The postinstall script is a bash script that also records its progress to a file named postinstall.log located in the distinct /private/tmp/ subdirectory.
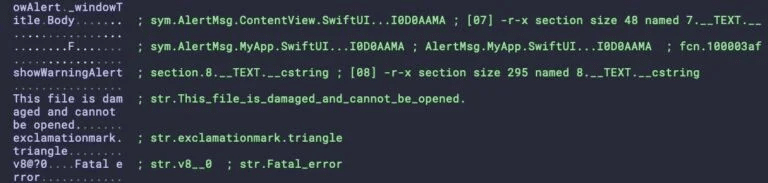
“This file is damaged and cannot be opened”, a message that mimics the genuine warning message typically thrown by Gatekeeper.
Sentinelone Said In There Research Article
The InstallerAlert.app is run by the same script, and its main purpose is to fool the user into believing that the malware is a genuine application that failed to run by displaying an alert dialogue with the error message “This file is damaged and cannot be opened,” which imitates the real warning message that Gatekeeper usually displays.
The “Contagious Interview” campaign, which started at least as early as November 2023, includes the FlexibleFerret virus. Consequently, attack methods spread out from a broader perspective.


