Hackingblog Exclusive : The FBI has obtained over 7000 lock bit description keys that can be used to recover the encrypted data of the lock bit random where attack victims and is urging them to come forward and report to them.

LockBit
This news was announced by the assistant director of FBI cyber division Bryan Vorndran on Wednesday at the 2024 Boston conference on cyber security.

The FBI cyberlead key noted
“from our ongoing description of lock bet be now have over 7000 description keys and can help victims reclame their data and get back online.”

Bryan Vorndran Also Mentioned
“we are reaching out to known locket victims and encouraging anyone who suspects they were a victim to visit our Internet crime Complaint Centre at ic3.gov“
The mastermind behind the lockbit infrastructure downfall is due to the international operation dubbed operation cronos.

In this specific case the FBI was able to seize 34 service which were containing over 2500 description keys which have the FBI to create a lock bit 3.0 black ransomware decryptor.
Although the FBI was successful by regaining a vast amount of keys the lock bit random where attack is still active and as since Switch to new servers and domains in the dark web.
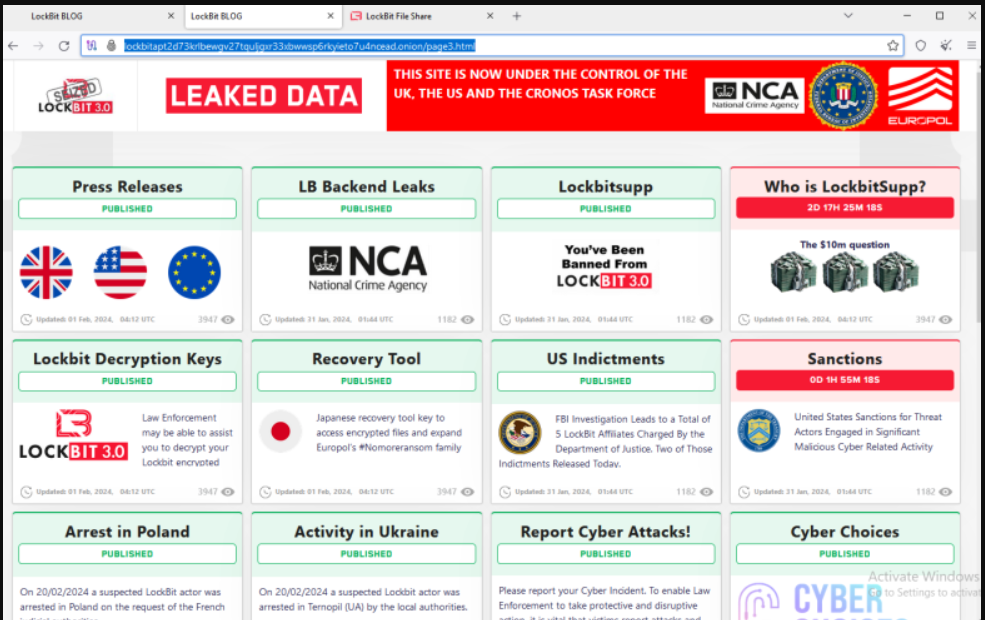
The US department is offering over 10 million to any individual who is able to uncover any information leading to lockbit with leadership arrest or conviction and an extra 5 million reward for tips leading to the arrest of log with ransomware affiliates.
A recent statement on operation cronos from European police agency europaul set the months long ago when they infiltrated the systems of log bits primary platform and other critical interest structures led to the take down of 34 servers which were from Netherlands Germany Finland France Switzerland Australia and the United States and the UK.
A total of 5 log bit affiliate now have been officially charged in arrested by the FBI. In May 2023 us authorities unsilled a wanted list with two alleged LockBit affiliates, Mikhail “Wazawaka” Matveev and Mikhail Vasiliev.
Matveev is still at large, most likely in Russia. Who is the Network Access Broker “Wazawaka?” was published by KrebsOnSecurity in January 2022. The article traced Wazawaka’s several aliases and contact information on Russian-language cybercrime forums down to Mikhail Matveev, a 31-year-old resident of Abaza, Russia.

Several denizens of XSS wondered aloud why the PHP flaw was not flagged by LockBit’s vaunted “Bug Bounty” program, which promised a financial reward to affiliates who could find and quietly report any security vulnerabilities threatening to undermine LockBit’s online infrastructure.
This prompted several XSS members to start posting memes taunting the group about the security failure.
“Does it mean that the FBI provided a pentesting service to the affiliate program?,” one denizen quipped. “Or did they decide to take part in the bug bounty program? :):)”
Frequently Asked Questions
What is Lockbit Ransomeware ?
One kind of ransomware called LockBit is meant to prevent users from accessing computer systems unless they pay a ransom. It is a very focused attack meant to coerce businesses and people into paying money. Key details of the LockBit ransomware are as follows:
Formation: In 2019, LockBit was initially discovered.
Type: A cybercrime tool called LockBit is used to launch ransomware attacks.
Major Incidents: LockBit has been implicated in a number of high-profile attacks, including as the hacking of the BlueLeaks Twitter account, the data breaches at the European Medicines Agency, Nintendo, the US federal government, EasyJet, Vastaamo, and numerous more.
What is operation cronos ?
What is the purpose of Operation Cronos?
With assistance from the business sector, law enforcement agencies from the US, the UK, and several other nations have joined forces to disrupt the LockBit ransomware group’s operations through Operation Cronos. The operation, which began in February 2024, entailed a months-long probe and compromise of LockBit is hidden web leak site and public face infrastructure.



Pingback: Bulletproof Hosting(BPH), Hacker's illegal Weapon Part 1 - Hacking Blogs