Here at HackingBlogs, we offer a concise summary of the most significant data breaches that have rocked the internet community in the past week.
In our weekly report, we will discuss the details of these breaches, the sectors they impacted, and the steps companies are—or should take—to improve their defences. Stay informed, stay safe, and allow us to look at the most recent security lapses.
ICICI BANK DATA IS LEAKED BY THE RANSOMWARE GROUP BASHE
ICICI Bank data was made public by the ransomware gang Bashe, and they have given a deadline of January 25, 2025, unless the demands are met.
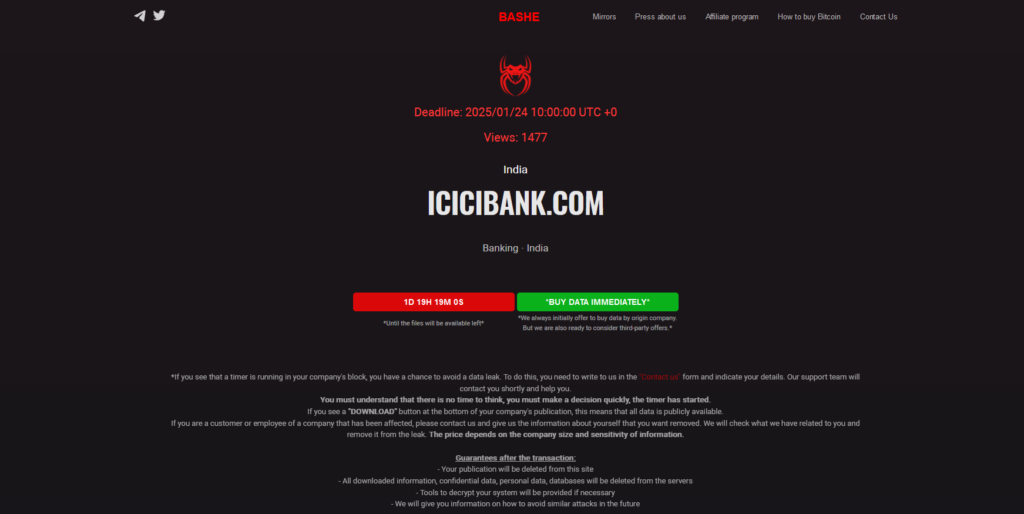
Once the demand for it’s ransom is made, the threat actor promises to provide the following guarantees following the transaction: That the publication will no longer be available on this website. All downloaded data, private information, and databases will be removed from the servers.
If required, tools to decrypt your machine will be sent. We will also educate you on how to prevent future attacks of this nature.
INC ransomware compromised Stark AeroSpace, a DoD defence contractor
The INC ransom organisation has claimed Stark Aerospace, a US-based manufacturer of aerial weaponry and missile systems under contract with the Department of Defence (DoD) and the US Military.
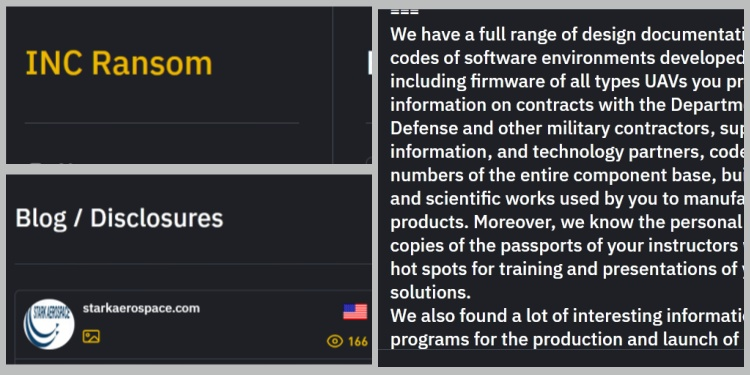
The defence contractor, whose tagline is “What We Do Protects & Saves Lives,” is also filled with extremely sensitive information that may be deadly if it ends up in the wrong hands, particularly in the hands of hostile countries like North Korea, China, and Russia.
The ransomware group claimed to have 4TB of data, including source code, design blueprints, employee passports, and firmware for every UAV manufactured, when they posted Stark Aerospace on its dark leak site on Thursday.
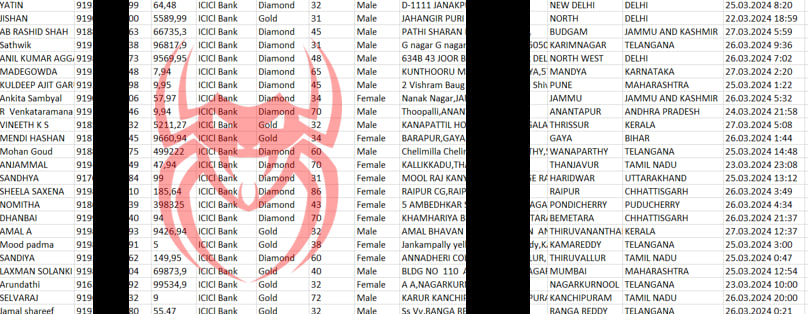
Alarms Are Raised by a Massive Leak of Online Loan User Data

Important information like phone numbers, email addresses, loan amounts, and financial transaction records are allegedly included in the compromised database. If confirmed, there could be major dangers from this breach, such as fraud, identity theft, and illegal access to bank accounts.
The urgent necessity for improved cybersecurity measures in digital lending platforms to protect user data is highlighted by this occurrence. To strengthen security, impacted users are encouraged to keep an eye on their accounts, report suspicious behaviour, and turn on multi-factor authentication.
Palo Alto Firewalls Were Discovered to Be Open to Firmware Exploits and Secure Boot Bypass
Three Palo Alto Networks firewall models (PA-3260, PA-1410, and PA-415) were examined and the results showed a number of security vulnerabilities known as PANdora’s Box. These include a number of UEFI firmware defects that could result in privilege escalation or malicious code execution, as well as serious firmware vulnerabilities like the BootHole (CVE-2020-10713) that permit Secure Boot to be bypassed.
Attackers may be able to get around security measures like Secure Boot thanks to the vulnerabilities, which impact devices’ boot procedures and network protocol stacks.
In response, Palo Alto Networks said that elevated privileges and certain conditions are necessary for successful exploitation, and that employing secure management interfaces and updated software reduces these risks. For some of the problems, they are also collaborating with outside manufacturers to upgrade the firmware.
The FTC Alerts People to a Risky New Brushing Scam Using Malicious QR Codes in “Gift” Packages
The Federal Trade Commission (FTC) has warned of a new malicious scam version in which scammers deliver dangerous QR codes in unwanted “gift” packages. The purpose of these presents, which could include upscale goods like jewellery or cosmetics, is to steal personal data.

The QR codes try to install malware on the victims’ devices or direct them to phishing websites. Credit card data, usernames, passwords, and compromised phones are the targets of the fraud. When interacting with dubious QR codes, the FTC suggests changing passwords, turning on multi-factor authentication, and keeping an eye on credit reports for indications of identity theft.
A New Malware Campaign Spreads Lumma Stealer by Using Phishing CAPTCHA Pages
Researchers have discovered a global malware campaign that uses fake CAPTCHA pages to spread the Lumma information stealer. The attack targets a number of industries in nations like Argentina, the United States, and the Philippines, including telecom and healthcare.
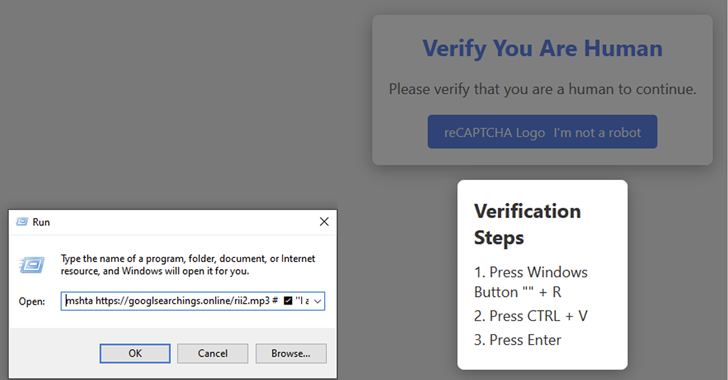
Through a sequence of PowerShell scripts intended to evade detection technologies such as the Windows Antimalware Scan Interface, victims are misled into executing a command from a compromised website that downloads and runs an HTA file, resulting in the installation of Lumma Stealer.
Additionally, the malware spreads through phoney domains that mimic Reddit and WeTransfer, and password-protected archives that contain a malware dropper. By employing many delivery channels, this campaign makes detection more difficult by utilising malware-as-a-service.


