Cyberalert: If you believe that you are not being watched, you should be aware that research has revealed WhatsApp vulnerabilities that let government agencies access your private messages.
Whatsapp Vulnerability “traffic analysis,”
The security team at WhatsApp reported an important danger to its users in March. Users are still at risk from government spying even with strong encryption. The content of 2 billion conversations between users is protected, according to an internal document published by The Intercept, but government agencies can get around encryption to find out who is talking to whom, what makes up secret groups, and maybe even where individuals are.
“THIS UNDISCLOSED WHATSAPP VULNERABILITY LETS GOVERNMENTS SEE WHO YOU MESSAGE,” according to The Intercept.
The weakness arises from a decades-old network monitoring method called “traffic analysis,” which surveys internet traffic on a large national scale. It is obvious from the document that other messaging services are vulnerable besides WhatsApp. It argues, however, that Meta, the company that owns WhatsApp, needs to make an immediate choice on whether to put the security of a small but vulnerable group of users first or the functionality of its chat service.
The research study concluded that WhatsApp “should reduce the ongoing exploitation of traffic analysis vulnerabilities that allow nation governments to discover who is chatting to whom.” “We require strong and practical defences against traffic analysis for our at-risk users.”
How is the ongoing Gaza War impacted by the flaw
In context with the ongoing war in Gaza, many Meta employees found the threat alert to be disturbing. Four WhatsApp employees told The Intercept that they had fears that Israel would be using this vulnerability as part of a programme to monitor Palestinians at a time when digital surveillance is being used to assist determine who gets killed in the Gaza Strip
Thousands of Gaza citizens have been caught up in Israel’s extensive monitoring of Palestinian faces as a result of its efforts to identify Hamas militants since the strike on October 7. Many of individuals who had been detained or imprisoned, frequently on the basis of minimal or no evidence, later claimed to have endured torturous questions.

The Times highlighted Palestinian poet Mosab Abu Toha in its report on facial recognition technology, citing how the Israeli military’s use of the technology led to his imprisonment and torture.
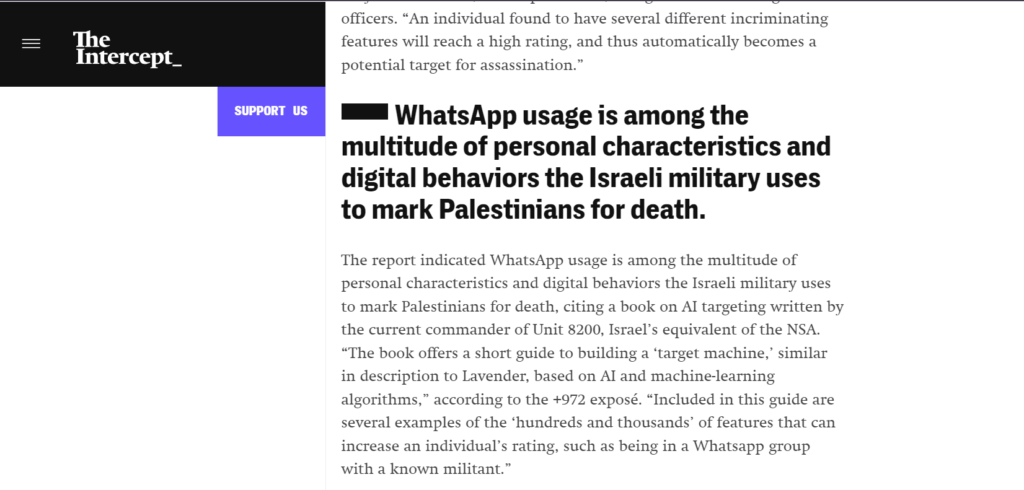
The Israeli military automatically approves the death of Palestinians in the Gaza Strip through a software programme known as Lavender, according to a joint article published last month by +972 Magazine and Local Call.
According to the report, which cited six Israeli intelligence organisations, Lavender algorithmically awards “nearly every Gazan a grade between 1 and 100, suggesting the chance that they are militants” using a vast data set of 2.3 million people.
“WhatsApp has no backdoors and we have no evidence of vulnerabilities in how WhatsApp works,”
Meta spokesperson Christina LoNigro
Despite the fact that WhatsApp messages cannot be read, the analysis demonstrates how governments can use their access to internet infrastructure to track the times and locations of encrypted conversations, much like they would if they were watching a postman delivering a sealed item.
“We kill people based on metadata,”
National Security Agency chief Michael Hayden
All participants in WhatsApp group chats, or both parties to the conversation, must be on the same network and in the same country for traffic sniffing attacks to be successful. Although individuals residing in nations with sufficient privacy regulations would be considered less vulnerable, instances of similar telecom monitoring methods have been documented in the US.
Because the Israeli government controls internet access in Gaza, Palestinian users are particularly exposed to attacks of this nature. This makes the situation there more disturbing.
The right course of action is obvious to WhatsApp‘s security staff. According to the study, “WhatsApp Security cannot solve traffic analysis alone.” “In order to develop protection for these targeted, at-risk users, we must first come to an agreement to unite and fight this battle together.


