Hi everyone that reads HackingBlogs!
In this article, we’re looking into a recent research macOS malware by Jamf Threat Labs, which discloses how attackers use PyInstaller to spread malware on macOS devices. We’ll examine the technical aspects, analyze the methods employed, and describe how these malicious campaigns are being carried out. So let’s go right in without further ado.
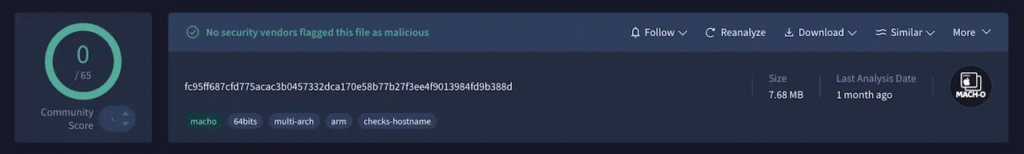
The researchers start by looking at a prior investigation where they found a suspicious Mach-O file called stl on VirusTotal. For those of you who don’t know, macOS and iOS use a file format called Mach-O (Mach Object) for shared libraries, executables, and object code. It is the format in which macOS loads and runs applications. They discovered that this Mach-O file was an infostealer malicious software meant to steal confidential data after closer examination.
MacOS malware: How the Mach-O Infostealer Behaves ?
Although some actions were seen on VirusTotal, the infostealer’s function is not fully explained in this article. Through an AppleScript dialog, the malware asks the user for their password several times until the right one is entered. Additionally, it uses /usr/bin/osascript /tmp/osascr.scpt to run a secret script and tccutil reset AppleEvents to reset system privileges. A suspicious domain ending in “/connect," which is a common pattern observed in previous infostealer samples, is another domain with which it communicates.
What is PyInstaller? Never Heard of It Before?
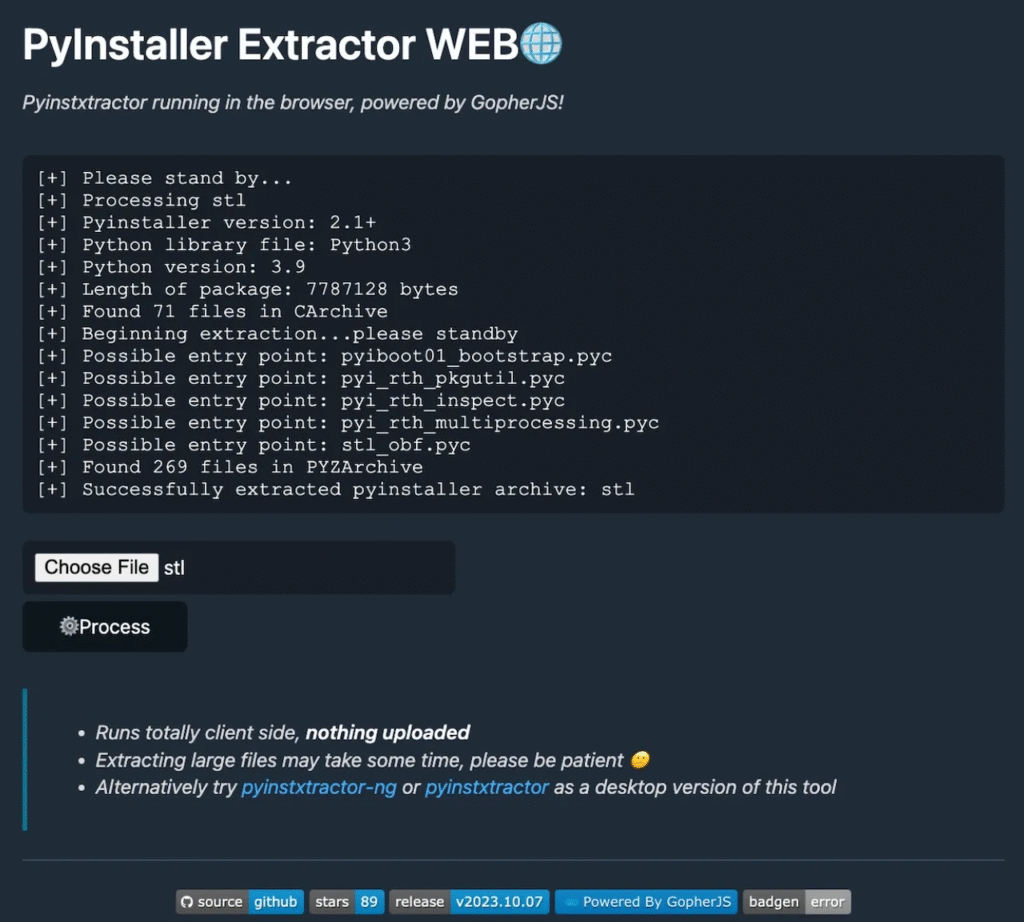
PyInstaller is an application for creating independent executable files from Python programs. In other words, you may package a Python script which normally requires Python to run into an executable file that can run on a computer without using Python.
A Python script, the Python interpreter, and all of its dependencies are combined into a single executable file by PyInstaller. This implies that Python does not need to be installed on the system in order to run the executable because the file contains all the necessary components. After analyzing the Python script, it gathers all of the files and libraries it needs and bundles them into a single executable file.
Let’s Breakdown The Static Analysis ?
“Static analysis means looking at the file without running it, to figure out what it does and if it’s dangerous.“
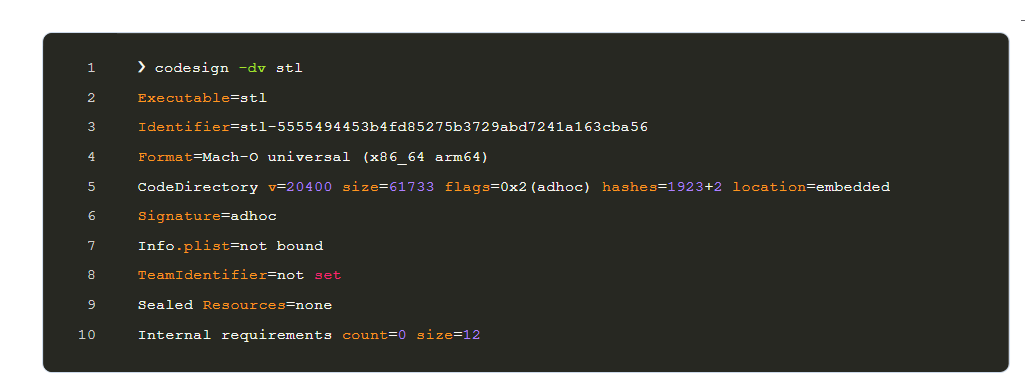
Checking the Signature
First, the file’s code signature is verified using the <codesign> command. A legitimate code signature indicates that a reliable developer has signed the file. The term “adhoc” indicates that it was not signed by a recognized authority, which raises suspicions about files.
Codesign -dv stl indicates that the file is ad-hoc signed, which means that a reliable authority did not sign it. Additionally, it indicates that the file is not from a verified developer because it lacks a “Team Identifier” and “Sealed Resources.”
Confirming the Architecture (Which Computers the File Can Run On)
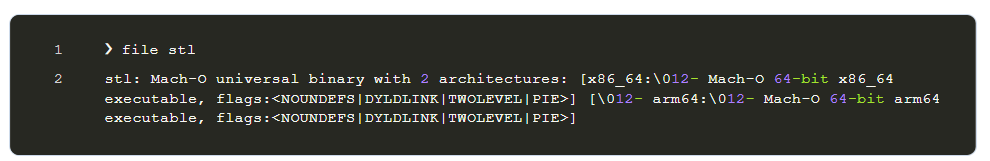
The file command checks what kind of computer the file can run on. It shows that the stl file is a Mach-O FAT binary, meaning it can work on both Intel (x86_64) and Apple Silicon (arm64) Macs.
Both x86_64 (Intel-based Macs) and arm64 (more recent, Apple Silicon-based Macs) are supported by the file, according to the file stl command.
Identifying PyInstaller Usage
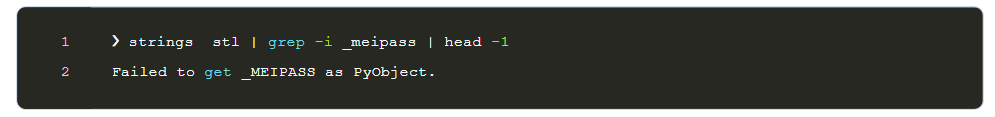
A <strings> command is used to search for any hints (such as certain terms or patterns) in the file to determine whether PyInstaller was used to build it.
strings stl | grep -i _meipass indicates that “_MEIPASS” is present. PyInstaller uses this unique marker to arrange its bundled files. This demonstrates that the file was packaged using PyInstaller.
Examining the PyInstaller Archive
Python code, libraries, and a bootloader are all included in the file that PyInstaller packs into the software. These components are extracted into a temporary folder when the file is launched. This procedure includes the _MEIPASS folder name.
The arm64 slice (version for Apple Silicon) is significantly larger than the Intel slice (for earlier Macs), according to the research conducted using the lipo command. This suggests that the PyInstaller archive is not included in the Intel component but rather in the arm64 component.
Verifying the Presence of PyInstaller’s Archive
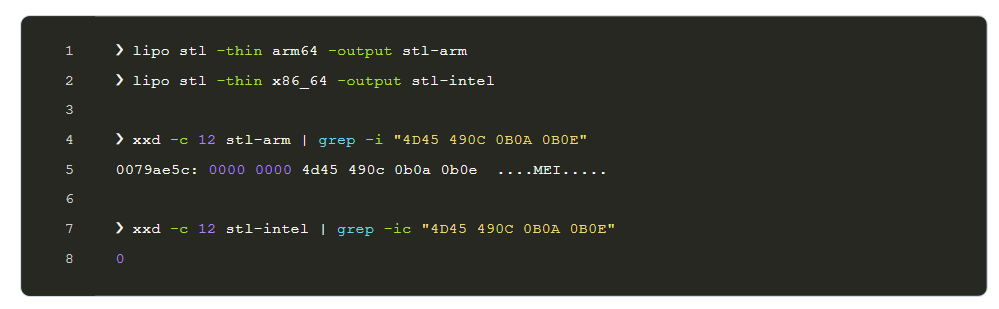
Using the xxd command, one can examine the file’s raw content and look for particular markers also referred to as magic numbers that show the location of the PyInstaller archive.
The presence of the PyInstaller archive on the arm64 slice is confirmed by the discovery of the magic number. Without the arm64 slice, the Intel slice would not function because it lacks the PyInstaller archive and has the magic number.
Breaking Down Dynamic Analysis
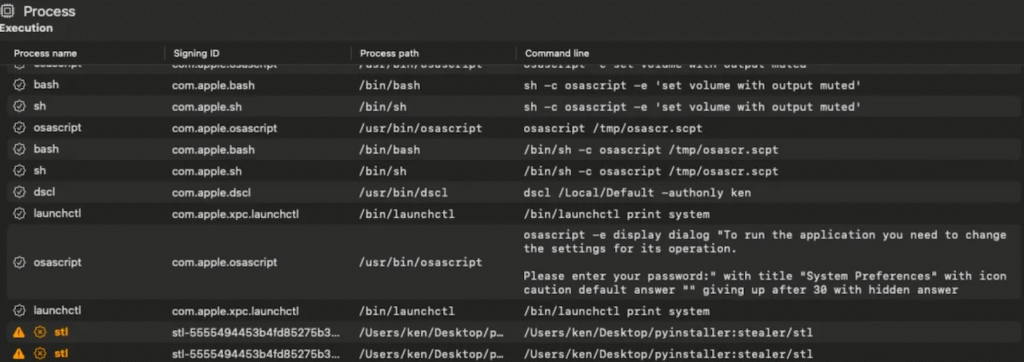
The dynamic analysis was performed using Mac Monitor.
They executed the stl file to check what it performs in real-time after completing the static analysis. Researchers saw a number of questionable actions using programs like Mac Monitor. The file activated instructions like osascript, which are frequently employed by malware, to show the user a password prompt and even minimize the system volume.

When the team looked at the environment variables, there were hints that pointed to PyInstaller, a program that packages Python scripts into standalone files, even though at first appearance there were no clear indications that Python was being used.
This verified the file was a Python application. The Python libraries were unpacked into a temporary folder when the file ran. Additionally, researchers observed actions like creating and deleting files, which suggested it was gathering private information. In the event decompiled the code, they discovered that it had been obfuscated using XOR encryption, base85 encoding, and string reversal.
The malware’s primary capabilities, as demonstrated by the decompiled script, include password theft, malicious AppleScript command execution, macOS Keychain credential extraction, and cryptocurrency wallet information theft. The fact that the stl file is an infostealer is confirmed by all of these actions.
“Infostealers are becoming more common on macOS, and attackers are using PyInstaller to hide malware.”
IOC’S : MacOS malware
filename: stl
sha1: 35ce8d5817ab7a7c5be33ea03c3234181286fd61
contacted domains:
hxxps://grand-flash[.]com/connect
hxxp://vapotrust[.]com/mac/stl
filename: stl-deobf.py
sha1: cd2ef119c9120ea56548f5cf0a3ff7d6ffc7613a
filename: installer
sha1: 878dcf854287e1dae3d5a55279df87eb6bdf96b3
contacted domains:
hxxps://grand-flash[.]com/connect
filename: sosorry
sha1: 90d33f249573652106a2b9b3466323c436da9403
contacted domains:
hxxp://138[.]68[.]93[.]230/connect
hxxp://138[.]68[.]93[.]230/Ledger-Live.dmg

