By Dipanshu Kumar HackingBlogs – May 17, 2025 | 5 min read
The Metasploit 6.4.64 RCE Privilege Escalation Exploits 2025 update demands immediate attention from security researchers, pentesters, and bug bounty hunters.
Highlights at a Glance:
- RCE Exploits: Car Rental System, WordPress SureTriggers
- Privilege Escalation: WP User Registration and Membership plugin
- Persistence: LINQPad .NET deserialization flaw
- Information Gathering: POWERCOM UPSMON PRO vulnerability
- Post-Exploitation: 32-bit support added to execute-assembly module

The popular offensive security framework used by red teamers and ethical hackers, Metasploit, recently received a major update that included important vulnerability fixes and powerful new modules. This week’s Metasploit release (v6.4.64) requires immediate attention by all security researchers, pentesters, and bug bounty hunters.
Along with important architecture improvements and bug fixes, the version, which was released on May 16, 2025, adds new remote code execution (RCE) exploits, a privilege escalation module, and substantial persistence and information collecting capabilities.
“This week’s release is packed with new module content… We also added support for 32-bit architectures to our execute-assembly post module,”
wrote Spencer McIntyre, in the official Metasploit Wrap-Up.
New Modules Every Researcher Should Know
1. Car Rental System 1.0 – File Upload RCE (CVE-2024-57487) :
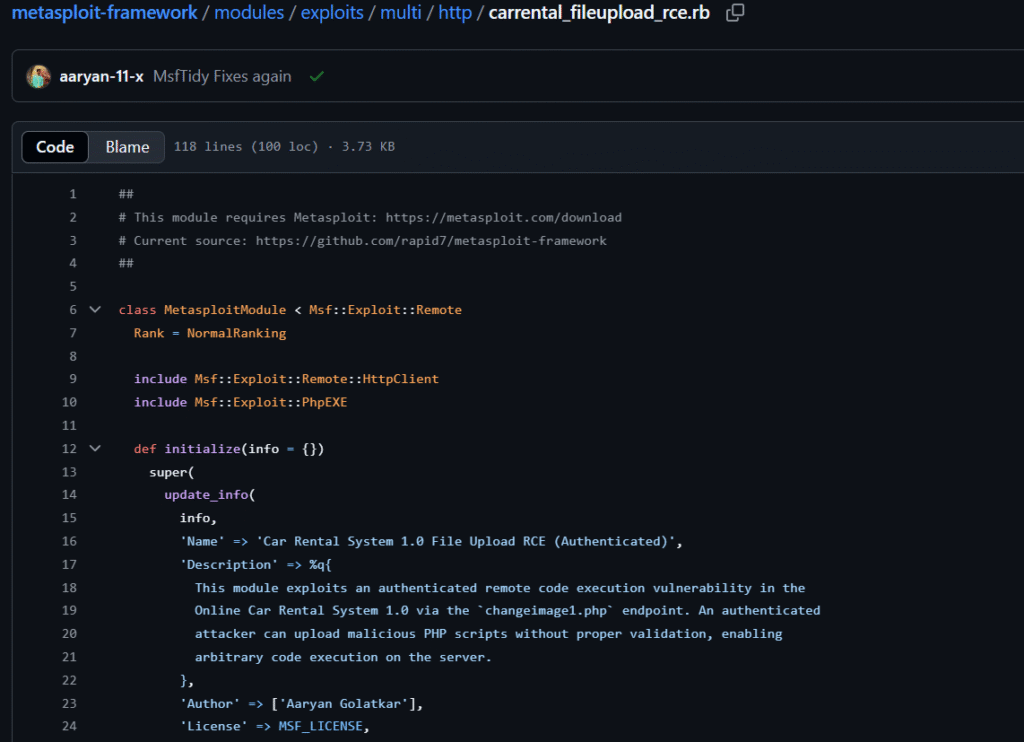
Through a weak file upload capability, this authenticated exploit enables attackers with admin credentials to carry out RCE. Aaryan Golatkar supplied this module, which is now accessible at multi/http/carrental_fileupload_rce
2. WordPress SureTriggers – Auth Bypass to RCE (CVE-2025-3102)
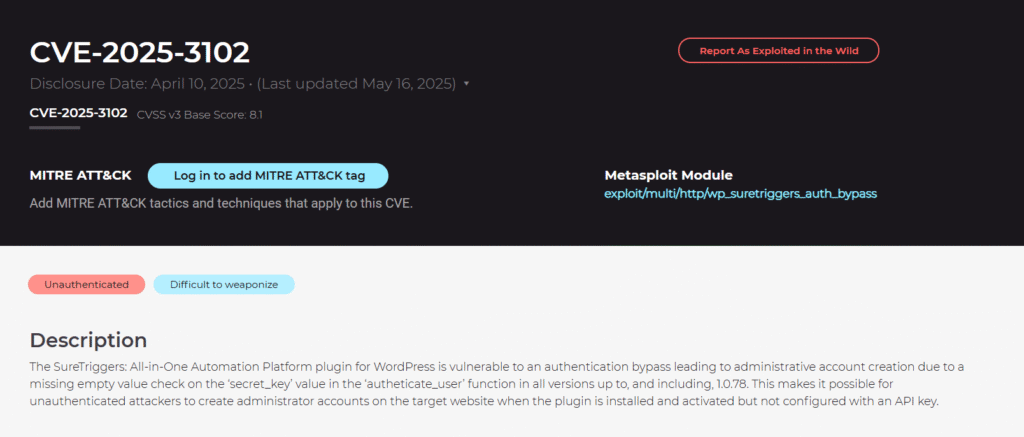
This vulnerability allows an unauthenticated attacker to generate an admin user and run arbitrary code. The flaw is present in versions ≤ 1.0.78. This was a joint effort by researchers Valentin Lobstein, Michael Mazzolini, and Khaled Alenazi (Nxploited). Multi/http/wp_suretriggers_auth_bypass is the metasploit path.
3. WP User Registration & Membership – Privilege Escalation (CVE-2025-2563)
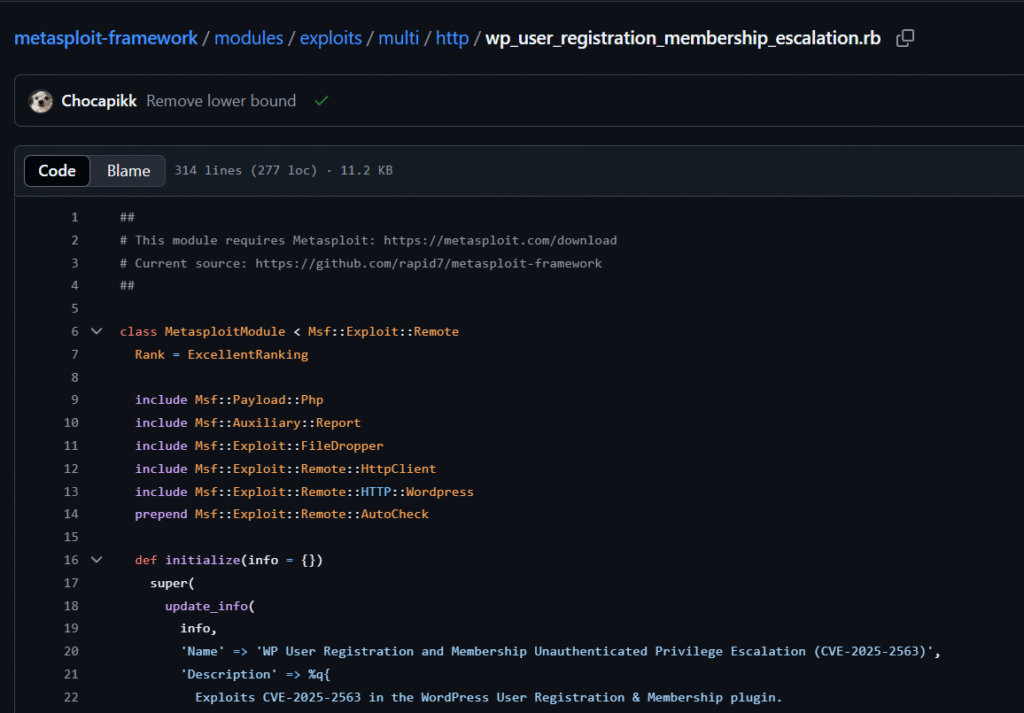
Unauthenticated users can obtain administrator capabilities in WordPress by taking advantage of this flaw. This module was added under multi/http/wp_user_registration_membership_escalation by Valentin Lobstein and Wesley (wcraft).
4. LINQPad Persistence – .NET Deserialization (CVE-2024-53326)
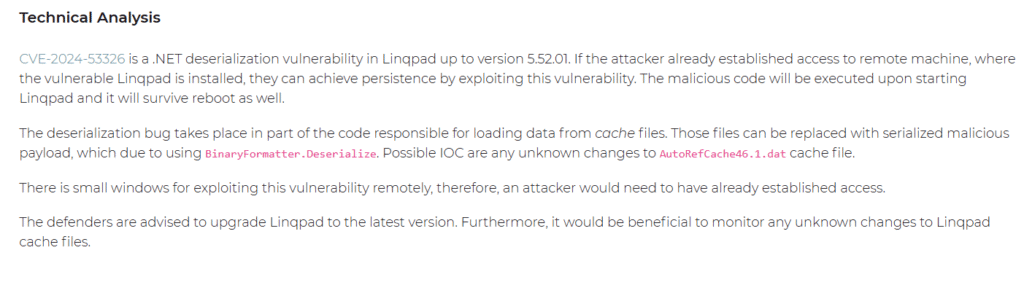
Maintains persistence on Windows computers by taking advantage of a deserialization bug in versions prior to 5.52. Martin Sutovsky and James Williams wrote it (msutovsky-r7).
5. POWERCOM UPSMON PRO – Path Traversal & Credential Harvesting (CVE-2022-38120/38121)
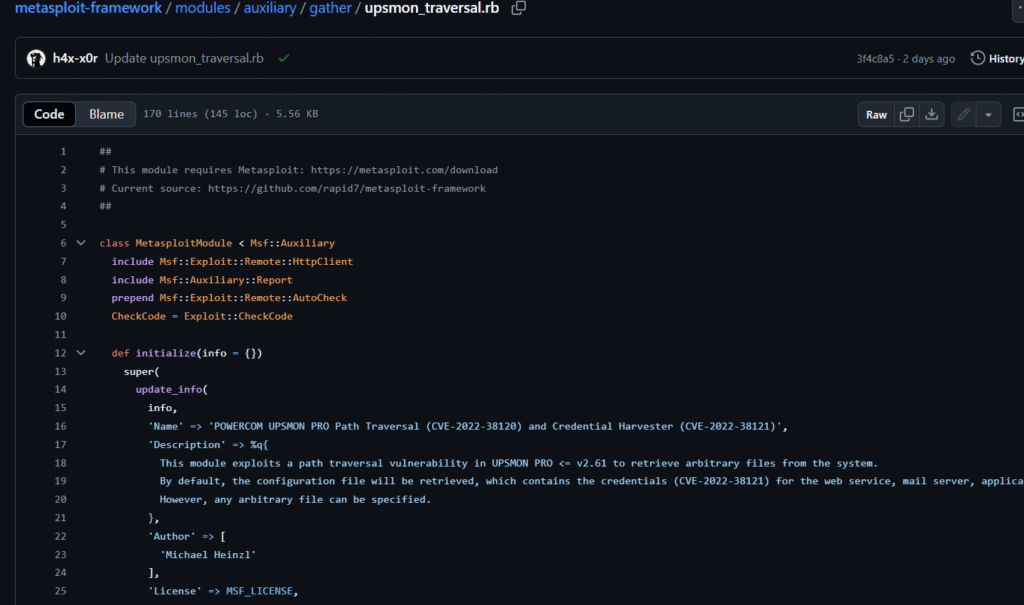
An auxiliary module reads arbitrary files and leaks plaintext credentials by taking advantage of two different vulnerabilities. Gather/upsmon_traversal is the module path. The author is Michael Heinzl.
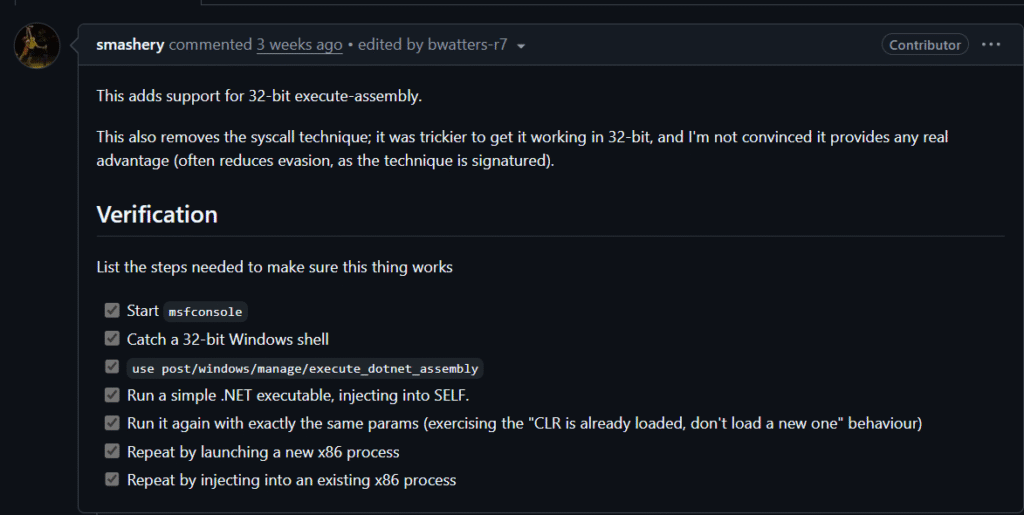
Post-Exploitation in Metasploit 6.4.64 RCE Privilege Escalation Exploits 2025
32-bit.NET assemblies can now be injected into Metasploit using the new execute-assembly post module. The range of target system payload compatibility is increased by this dual-architecture capabilities (64-bit + 32-bit). A smashery improvement that is essential.
Key Fixes and Enhancements (Notable Mentions)
- WordPress Login Fix: Metasploit’s login process was occasionally failing, but it has been resolved.
- SMB_to_ldap Update:
RHOSTSis used in place of theout-of-date RELAY_TARGETS option. - Yama ptrace_scope Checker: Local post modules speed up using a new Linux technique.
- Web Crawler Logs: Testing is now simpler thanks to modules’ support for HTTP logging.
Additionally, several typos, metadata issues, and command crashes (especially under specific Ruby environments) were fixed to improve stability.
How to Get the Update
- Run
msfupdatein your terminal. - Or install fresh from the Metasploit Nightly Installer.