Cyberalert: The Void Banshee Cybercrime Group hacks the Microsoft MSHTML protocol. Hackers are breaking the Atlantida malware using the protocol.
How does Atlantida Malware work? How Microsoft Was Hacked and How Can You Avoid It? To find the solutions, read the article.
What is the Atlantida Malware ?
The name of a stealer is Atlantida. This type of malware targets installed systems and programmes in order to obtain confidential data from them. It has been noted that unknown free software and “cracked” software websites are rapidly spreading the Atlantida stealer.
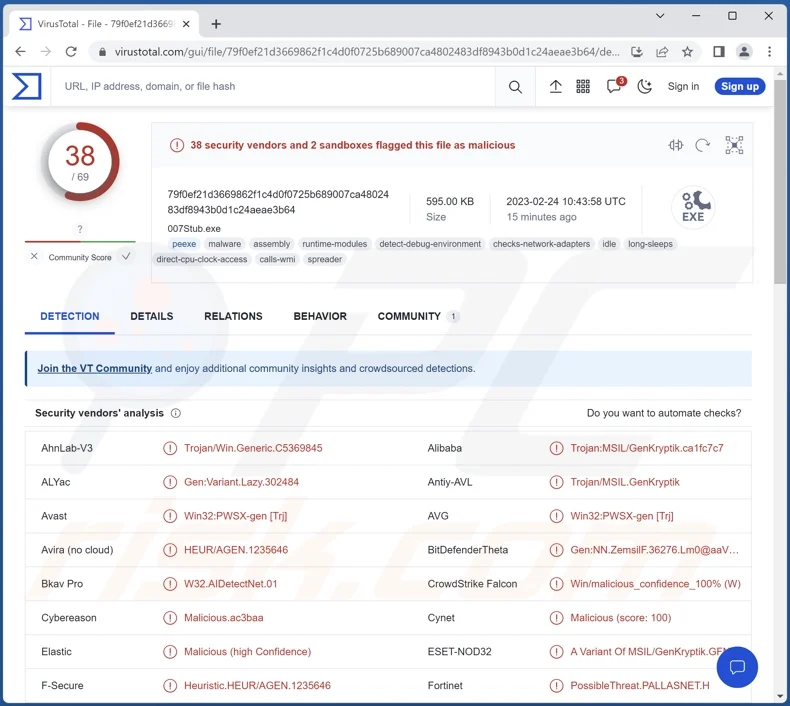
Malware of the stealer type is designed to steal data. Files kept on hacked computers can be stolen, or downloaded, by these malicious programmes.This malware can be capable of extracting log-in credentials (usernames/passwords) from other apps as well, e.g., email clients, VPNs, messengers, FTP clients, cryptocurrency wallets, and others.
A couple of examples of targeted apps are FileZilla, Telegram, and Steam. Also, Atlandida may capture screen and get information about the installed hardware (e.g., RAM, GPU, and CPU).
Devices running Atlantida software run the risk of serious privacy problems, large financial losses, and identity theft.
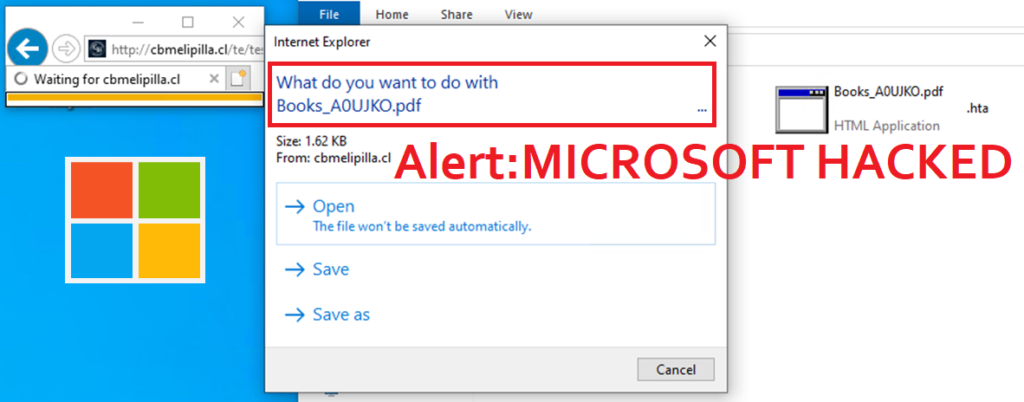
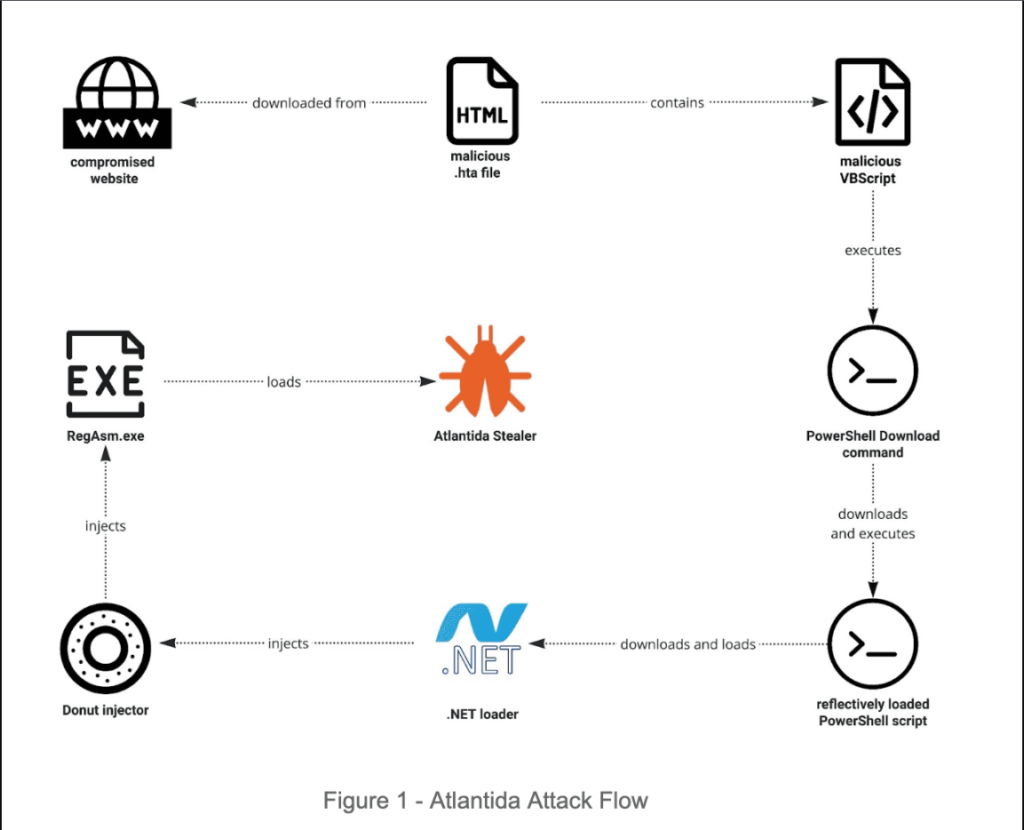
An information stealer known as Atlantida has been reported to be delivered by the advanced persistent threat (APT) group Void Banshee, which is taking use of a recently discovered security hole in the Microsoft MHTML browser engine as a zero-day.
The vulnerability, identified as CVE-2024-38112, is utilised to open the outdatedand unsafe Internet Explorer browser through specially constructed web shortcuts, enabling multi-stage attacks.

In the middle of May 2024, Trend Micro discovered Void Banshee activity. The criminal group is well-known for stealing financial information and focusing on North America, Europe, and Southeast Asia. The Atlantida campaign was more active this year, according to researchers, and it recently modified the CVE-2024-38112 vulnerability to fit its infection chains.
Experts stress that organisations all around the world are seriously threatened by APT outfits like Void Banshee’s ability to successfully target disabled Windows system services like Internet Explorer.
Check Point earlier revealed a campaign that distributed further malware via the same vulnerability. Microsoft fixed the issue, CVE-2024-38112, last week as part of their Patch Tuesday upgrades.
How CVE-2024-38112 was exploited by Void Banshee
Haifei Li, a researcher at Check Point, explained that the attackers used files that had been created to take use of the vulnerability and were made to look like PDFs.

Through the use of internet shortcut (URL) files and the MHTML protocol handler, the threat actor exploited CVE-2024-38112 to run malicious code. The threat actor was able to access and execute files directly through the disabled Internet Explorer instance on Windows computers by using this method, according to Trend Micro researchers.
“The Atlantida virus was used to infect users and organisations through this MHTML code execution vulnerability.”
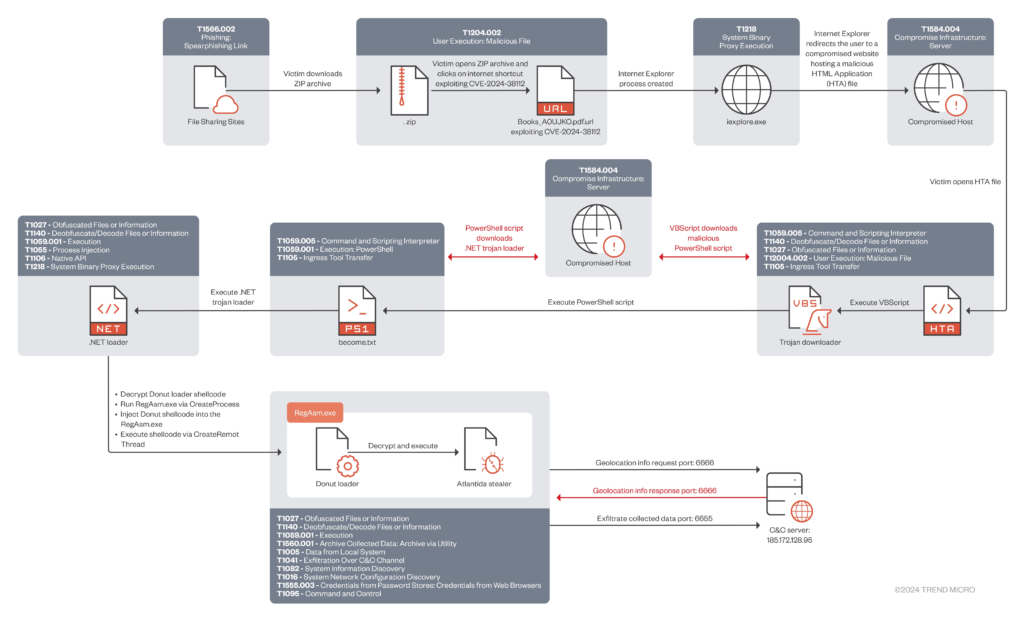
The threat actors directed victims to ZIP files that included malicious files acting as PDFs and PDF copies of books by using spear-phishing methods. The ZIP files were stored on hacked websites, cloud sharing platforms, online libraries, and Discord.
Microsoft Reaction toward the incident
Researchers from Check Point and Trend Micro discovered the CVE-2024-38112 attack in the middle of May 2024, and they informed Microsoft of their discoveries. Microsoft accepted the former in the vulnerability’s security advisory and on July 2024 Patch Tuesday, the company published remedies for the vulnerability that prevent MHTML from being utilised inside internet shortcut files (.url).
Li stated that “coordinated disclosure can not be just one-side coordination” and added, “This is not the first time [Microsoft] tells us they’re going to correct the issue in month X but published the patch sooner without contacting us.”
ZDI stated “I hate to say this,” he continued, “but it seems like they really don’t have a full grasp of what’s going on with this patch.”””
Unexpected access points for attackers might be created by inactive or infrequently used components, exposing the infrastructure of the entire company. Any modern company’s cybersecurity strategy should now include regular updates and thorough audits of all IT environment components, including those that are hidden or thought to be dormant.



Pingback: Microsoft Outage: How to Fix Bsod Blue Screen Of Death - Hacking Blogs