Alert: IPv6 systems are vulnerable to TCP/IP bugs that spread without input from users. Users should be aware that all Windows computers with IPv6 setup by default are vulnerable to remote code execution (RCE) due to a major TCP/IP vulnerability, as disclosed by Microsoft.
What is the Bug About ?
This security flaw, discovered by Kunlun Lab’s XiaoWei and listed as CVE-2024-38063, is the result of an integer underflow vulnerability that attackers may utilise to cause buffer overflows on vulnerable Windows 10, Windows 11, and Windows Server systems, which might be exploited to execute arbitrary code.

“Considering its harm, I will not disclose more details in the short term,”
Security Researcher (Microsoft)
Exploits cannot be prevented by blocking IPv6 on the local Windows firewall since the vulnerability is activated before the firewall processes it.
What is Integer Overflow
The term “integer underflow” is occasionally used to describe signedness problems, which occur when a subtracted number turns an initially positive value negative. Bad subtraction is not always a signedness problem, though; there are instances of it involving unsigned integers.
Sometimes array index issues with a negative index are referred to as “integer underflow.”
Microsoft clarified in its official notification that by constantly sending specially designed IPv6 packets, attackers can remotely exploit the flaw. Since the problem is extremely hard to exploit, attacks are more likely to take advantage of it. Similar vulnerabilities have been exploited in the past, according to the corporation, which makes the problem extremely attractive to hackers.

Additionally, Microsoft released its exploitability assessment for this serious vulnerability, classifying it as “exploitation more likely” and indicating that threat actors may be able to “repeatedly exploit the defect in assaults” by writing exploit code.
Furthermore, Microsoft is aware of previous exploits of this kind of vulnerability. Because of this, it would be a more desirable target for attackers, increasing the likelihood that exploits may be developed,” says Redmond.

“Therefore, consumers should give this higher priority after reviewing the IPv6 security update and determining its relevance inside their context.”

CVE-2024-38063 was identified by Trend Micro as one of the most critical vulnerabilities that Microsoft patched in the most recent security update. The vulnerability, like computer worms, may spread between systems automatically, according to the business, which highlighted its “wormable” characteristics.
Additionally, Trend Micro pointed out that practically all devices come with IPv6 enabled by default, making attack prevention more difficult.
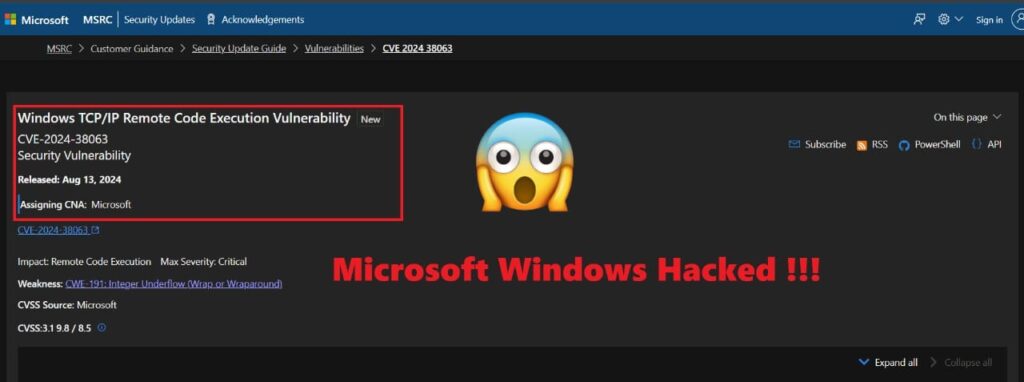
CVE-2024-38063

A remote code execution vulnerability in Windows TCP/IP, known as CVE–2024–38063, has a 9.8 CVSSv3 score and a maximum severity level of Critical. Important information consists of:
- An attacker can send specially constructed IPv6 packets to a target host in order to remotely exploit this vulnerability.
- This vulnerability can be exploited with just one click, or a “0-click.”
- This vulnerability can only be exploited with IPv6 packets.
- The vulnerability has been categorised by Microsoft as “Exploitation More Likely.”


