Microsoft has found many vulnerabilities in OpenVPN, a popular VPN software that is incorporated into millions of PCs, routers, mobile devices, firmware, and other smart devices. They could be used in privilege escalation and remote code execution (RCE) attacks when chained together.
Microsoft Says “Attack-chained: OpenVPN flaws that could cause RCE and LPE found”

Certain vulnerabilities have been found that might be remotely exploited by attackers to create a chain of attacks that includes both local privilege escalation (LPE) and remote code execution (RCE). Attackers may be able to take complete control of the targeted endpoints using this attack chain, which might lead to data breaches, system compromise, and unauthorised access to private data.
However, taking advantage of these vulnerabilities requires intermediate knowledge of the operating systems, user authentication, and a thorough comprehension of OpenVPN’s internal workings.
During there presentation at Black Hat USA 2024, Microsoft revealed this study and provided a demonstration of the found attack chain.
Among the vulnerabilities found are:

- CVE-2024-27459: Impacts the openvpnserv component, potentially causing local privilege escalation (LPE) and denial of service (DoS) attacks on Windows.
- CVE-2024-24974: This vulnerability, which is also present in openvpnserv, permits unauthorised access to Windows.
- CVE-2024-27903: On Windows, this vulnerability may lead to remote code execution (RCE), and on Android, iOS, macOS, and BSD, it may lead to LPE or data manipulation.
- CVE-2024-1305: May cause a DoS on Windows via affecting the Windows TAP driver.
The most interesting thing is that all of the vulnerabilities that have been found are client-side vulnerabilities. Microsoft highlighted that it has found no vulnerabilities in OpennVPN’s server security.
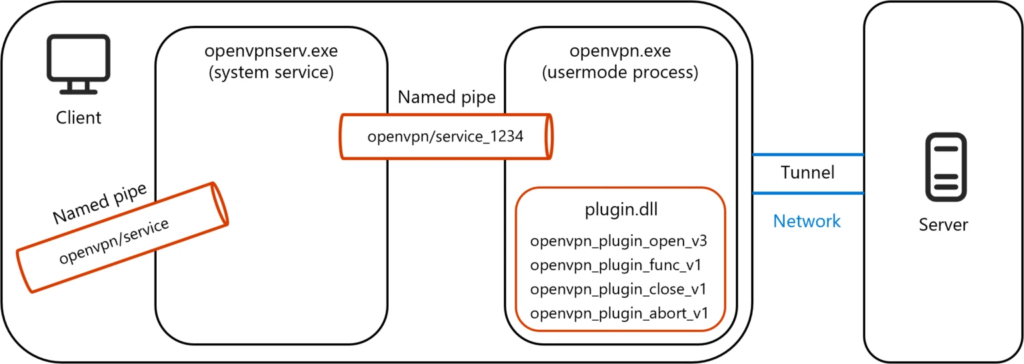
Through Coordinated Vulnerability Disclosure (CVD) and the Microsoft Security Vulnerability Research (MSVR) team, Microsoft disclosed these vulnerabilities to OpenVPN in March 2024. After then, OpenVPN and Microsoft worked to repair the vulnerabilities, which resulted in the release of OpenVPN 2.6.10. Microsoft does, however, advise customers to install the most recent security upgrades as soon as they become available in order to reduce potential risks.
“All the identified vulnerabilities can be exploited once an attacker gains access to a user’s OpenVPN credentials, which could be accomplished using credential theft techniques, such as purchasing stolen credentials on the dark web, using info-stealing malware, or sniffing network traffic,” the report reads.
To make sure the version of OpenVPN you are using is current
openvpn --versionKeep your OpenVPN installation up to date to protect your system against vulnerabilities and take advantage of the newest features and security improvements.
Microsoft recommends that companies who use OpenVPN check their versions and install any updates right away. Further reducing possible dangers can be achieved by restricting access to VPN services and maintaining strict credential management.


