Researchers at ESET found a zero-day vulnerability in Telegram for Android that permits the sharing of malicious files that appear to be movies. The EvilVideo exploit made it possible for viruses to spread.
ESET researchers discovered a zero-day vulnerability that affects Telegram for Android. On June 6, 2024, the exploit, known as EvilVideo, was uploaded on a secret forum. Via Telegram channels, groups, and chats, attackers spread infected files by using the vulnerability to pass them off as multimedia files.
After obtaining an example of the exploit, the experts were able to analyse it and notify Telegram of the issue on June 26. Telegram versions 10.14.5 and higher were updated on July 11, 2024, to address the issue.
Thanks to this issue, malware files appearing as films might be sent by attackers to users of unprotected Telegram for Android (10.14.4 and above). The seller of the exploit provided a public Telegram channel example, which led to the discovery of the vulnerability on a hidden forum. This made it possible for researchers to download and evaluate the malicious file.
Analysis Of the Telegram Exploit by ESET
The exploit is compatible with Telegram versions 10.14.4 and below, according to our research of it. Since the Telegram API enables developers to programmatically upload specially built multimedia files to Telegram chats or channels, they conclude that the particular payload was most likely created using the Telegram API.
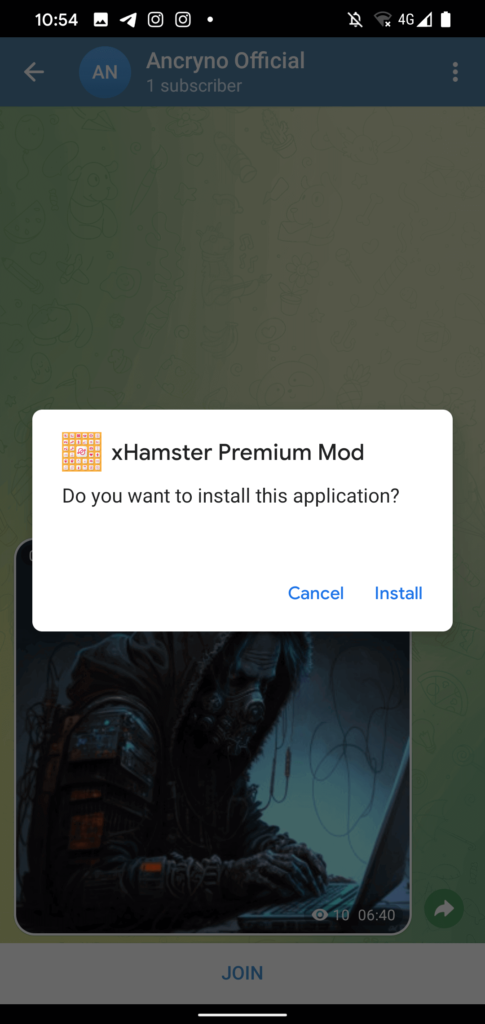
The ability of the threat actor to produce a payload that shows an Android app as a multimedia preview rather than as a binary attachment appears to be necessary for the vulnerability. The malicious payload manifests as a 30-second video once it is shared via chat.
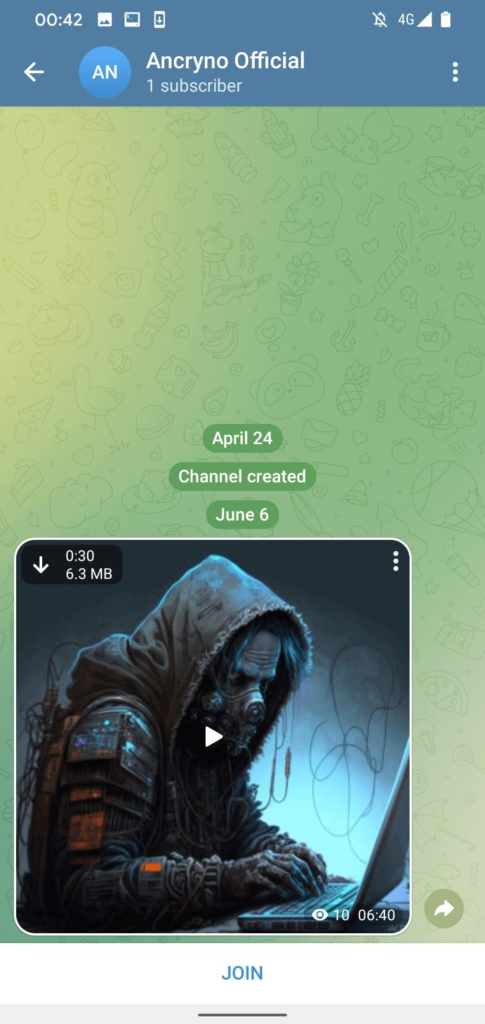
Media files received through Telegram are immediately scheduled to download by default. This means that when a user opens the discussion where the malicious payload was posted, those who have activated the option will instantly download it. The payload can still be downloaded by hitting the download button in the upper left corner of the uploaded, appearing video if the option is manually deactivated.
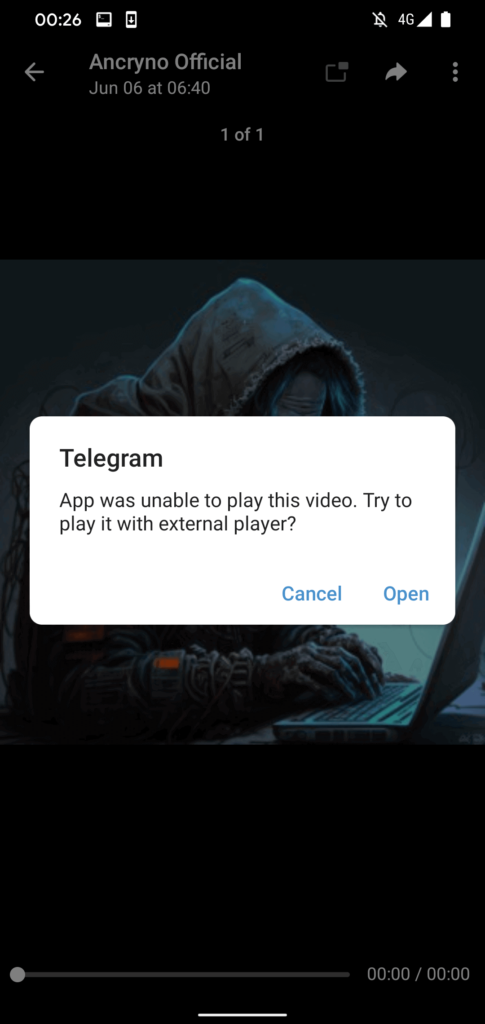
Telegram notifies the user that it cannot play the “video” and recommends using an external player if the user tries to play it.This original Telegram warning was discovered in the genuine Telegram for Android app’s source code; it was not created and distributed by the malicious payload.
Telegram will ask the user to allow the installation of unknown apps if they click the Open button in the displayed message, which will prompt them to install a malicious app that is posing as the previously mentioned external player.
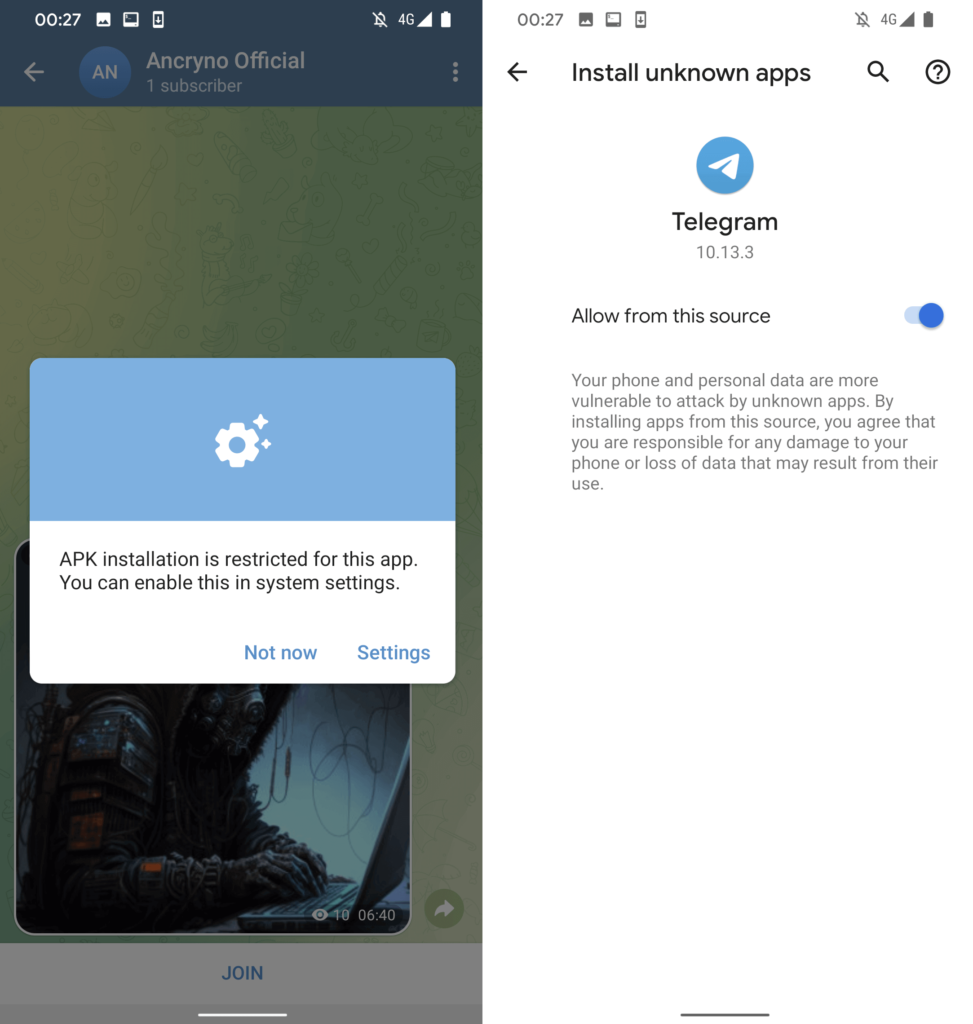
By now, the malicious programme in issue has apparently already been downloaded as a video file with the extension.apk. Curiously, the shared file seems to be a video due to the vulnerability’s nature—the malicious software itself was not changed to appear to be a multimedia file, indicating that the upload process was most likely attacked.
Threat Actor Detection By ESET
The vendor provided in their forum post regarding their Telegram handle. Apart from the exploit, from January 11th, 2024, they have been promoting an Android cryptor-as-a-service on the same underground forum, claiming it to be entirely undetectable (FUD).
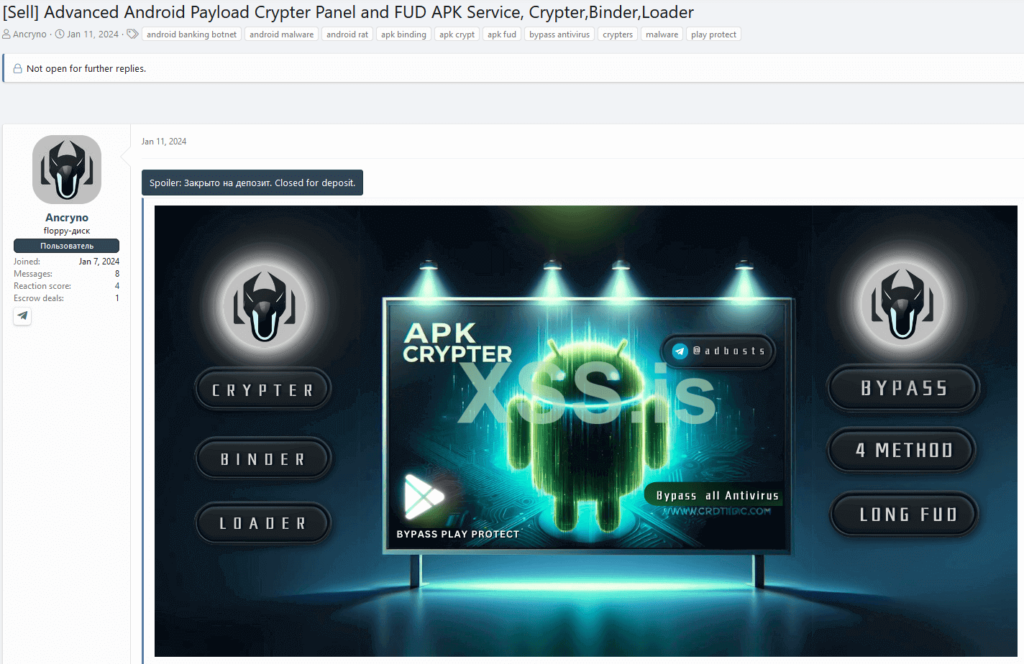
It takes use of a vulnerability to distribute malicious payloads through Telegram conversation that appear to be multimedia files. A request to install an external app will appear if a user attempts to play the supposedly video; this downloads the malicious payload. Luckily, as of July 11th, 2024, the vulnerability has been resolved.


