Introduction
Recently, 0patch researchers discovered a serious zero-day vulnerability that impacts every version of Windows, from Windows 7 to the most recent version, Windows 11 (v24H2). This vulnerability might lead to users being tricked into viewing a malicious file, which could reveal their NTLM credentials. All the information you want on the vulnerability and its impact on your Windows PC could be found here.
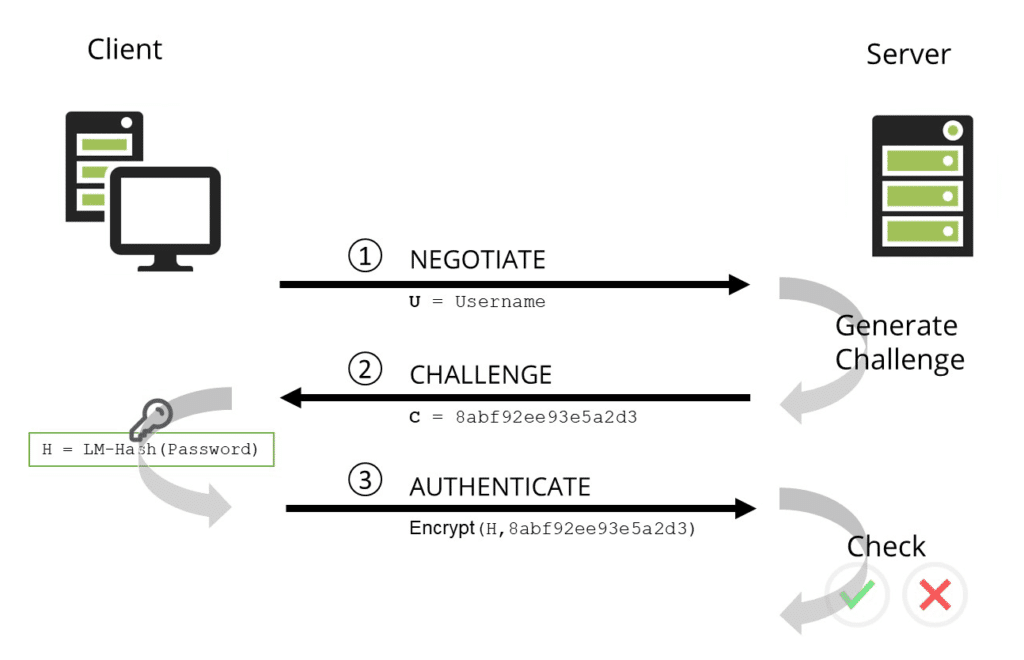
“The vulnerability allows an attacker to obtain a user’s NTLM credentials by simply having the user view a malicious file in Windows Explorer – e.g., by opening a shared folder or USB disk with such file, or viewing the Downloads folder where such file was previously automatically downloaded from attacker’s web page,”
0patch researcher Mitja Kolsek
Key Details of the Vulnerability
Vulnerability Overview: NTLM (New Technology LAN Manager) credentials, which are frequently used for authentication in Windows networks, are the subject of the recently identified zero-day vulnerability. When a user opens a malicious file that has been specially constructed in Windows Explorer, this vulnerability enables attackers to obtain NTLM credentials.
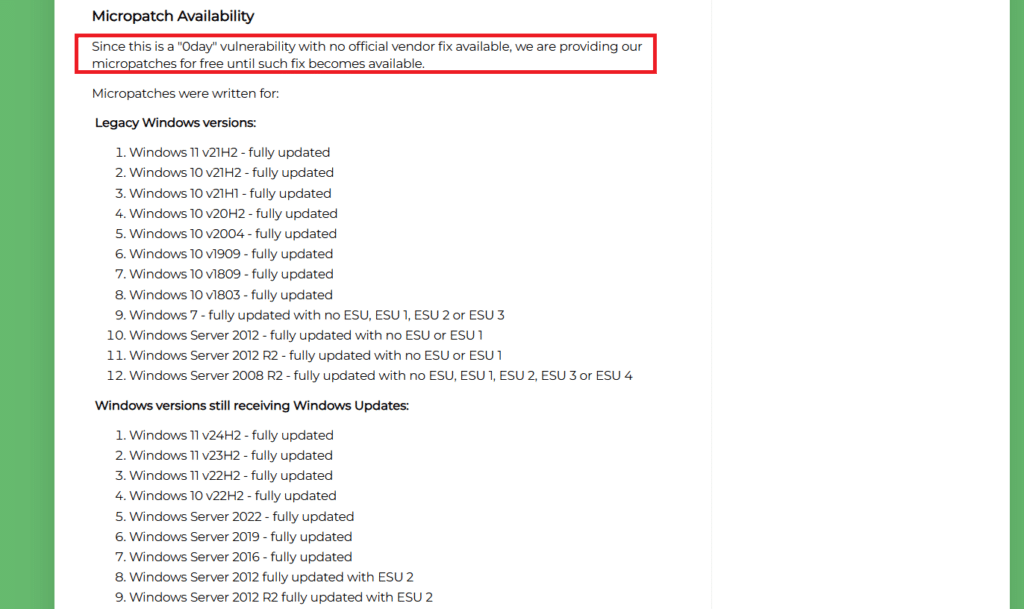
The vulnerability affects a number of Windows versions, ranging from more recent ones like Windows 11 (v24H2) and Server 2022 to older ones like Windows 7 and Server 2008 R2.
How Does the Attack Work?
- Attackers create a malicious file and put it on USB sticks, shared files, or even the Downloads folder so the victim can download it automatically.
- When the file is opened in Windows Explorer, the attacker can access sensitive systems and data without authorisation because their NTLM credentials are made public.
| Windows Version Affected | Impact |
|---|---|
| Windows 7, 8, 10, 11 | Vulnerable to NTLM credential theft |
| Windows Server 2008 R2, 2012, 2022 | Affected by NTLM vulnerability |
This Attack has a wide variety of threat with it lets discuss some of them
Why Is This Vulnerability So Dangerous?
- NTLM Credential Exposure: It is simple for attackers to obtain NTLM credentials, which they might then use to gain access to private information or breach corporate networks.
- Exploitation is simple; all you have to do is open a folder that contains the infected file to reveal your credentials.
- Absence of Official Patch: Users are at risk since Microsoft has not yet released an official fix. 0patch has stepped up with an unofficial micropatch until Microsoft publishes a patch.
Now lets have a look as to how you can protect your systems from this threat in the next section.
What Are the Mitigation Steps?
- Use 0patch’s Micropatch: 0patch is providing a free micropatch to safeguard users while they wait for an official Microsoft repair. All registered 0patch users have access to this micropatch, which may be installed without restarting your computer.
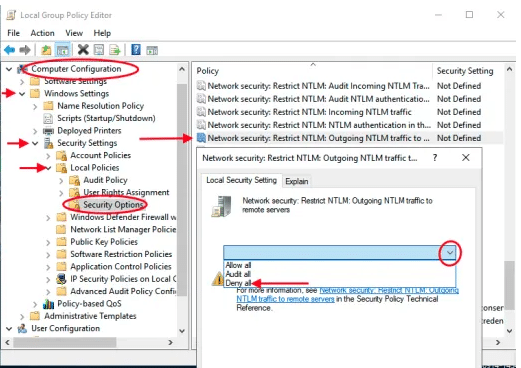
- Disable NTLM Authentication: Group Policy or registry changes can be used to disable NTLM authentication if you are worried about NTLM vulnerabilities. Here’s how to accomplish it:
Navigate to Security Options under Security Settings > Local Policies.
Restrict NTLM authentication in the context of network security. Limit NTLM. - Maintain Windows Updates: Make sure you have the most recent Microsoft patches installed on your Windows OS. Keeping up with updates is essential for security, even though Microsoft has not released an official remedy yet.