“We confirm that Ultralytics Yolo versions 8.3.41 and 8.3.42 were compromised by a malicious code injection targeting cryptocurrency mining. Both versions have been immediately removed from PyPI,”
“We have released 8.3.43 which addresses this security issue. Our team is conducting a full security audit and implementing additional safeguards to prevent similar incidents.”
Glenn Jocher, the founder and CEO of Ultralytics, acknowledged the attack and stated that it had been resolved

What is Ultralytics YOLO11 ?
Ultralytics YOLO11 is an artificial intelligence model for object detection and computer vision. YOLO11 (short for You Only Look Once) was created for real-time computer vision applications like object identification, image analysis, and pose detection. With over 30,000 stars, over 6,000 GitHub forks, and hundreds of thousands of downloads per day, the service is hugely popular.
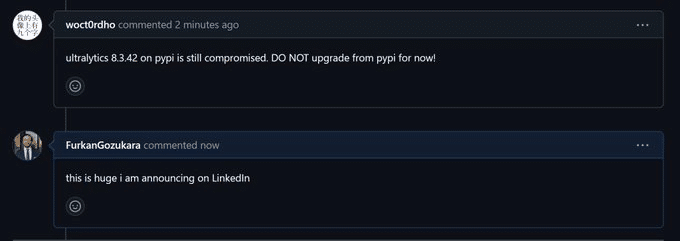
A suspected supply chain attack manipulated the AI model, which was then exploited to infect target devices with malware. The owner of the company verified the attack and stated that the malicious version was removed, but it appears that fresh malicious versions were discovered.
About The Exploitation
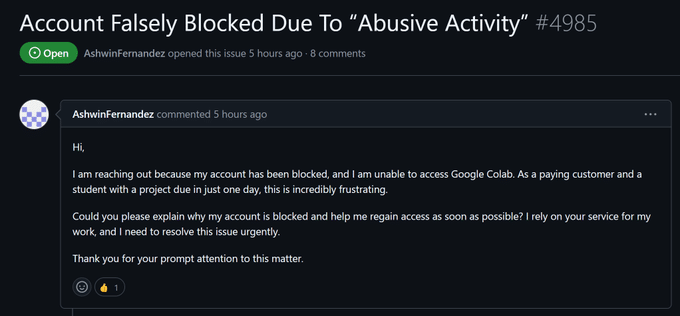
Users who installed the compromised versions of Ultralytics 8.3.41 and 8.3.42 directly or as a dependency found that a cryptominer had been installed. These versions were posted to PyPi yesterday. Owners of Google Colab accounts were reported and banned for engaging in abusive activities.
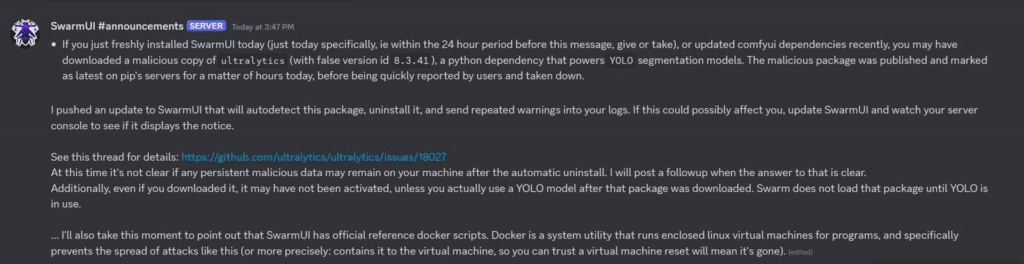
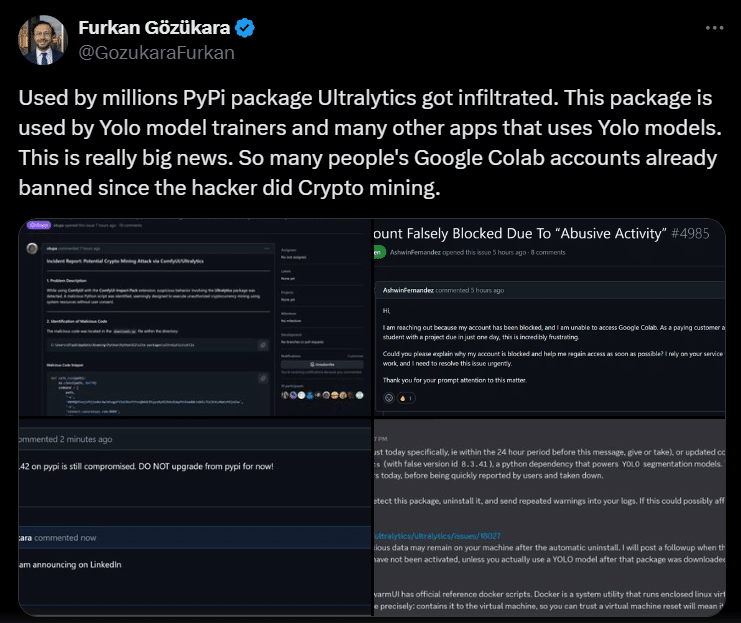
Both SwarmUI and ComfyUI confirmed that installing Ultralytics would have resulted in the miner being installed after new installs of their libraries.
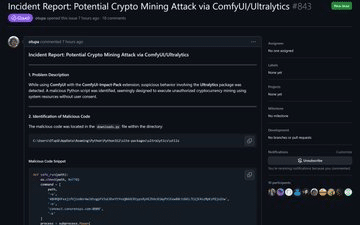
The compromised library connects to a minin pool at “connect.consrensys[.]com:8080” by installing and starting an XMRig Miner at ‘/tmp/ultralytics_runner’.