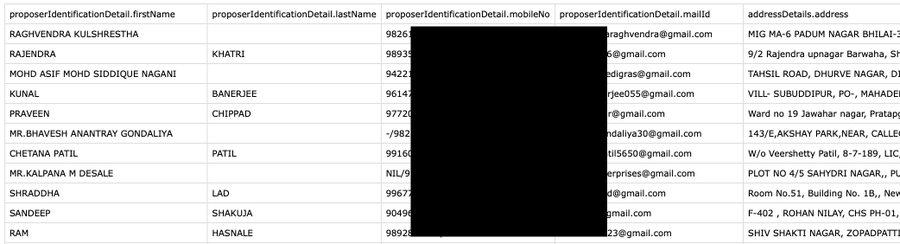
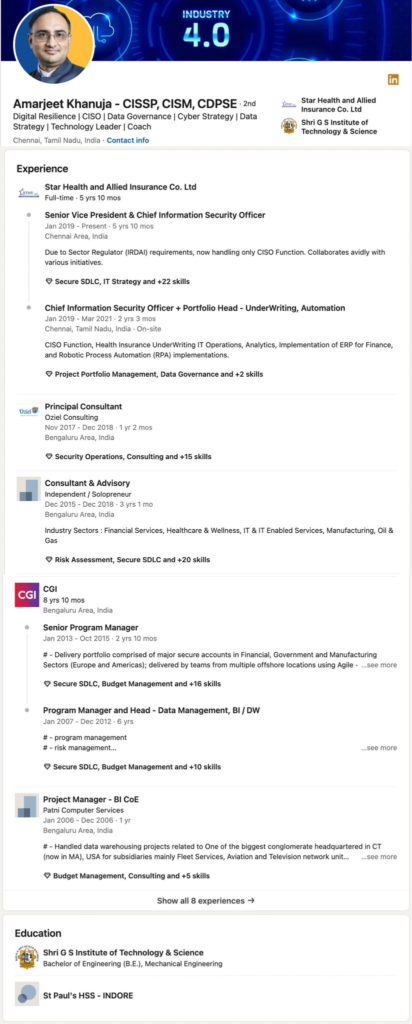
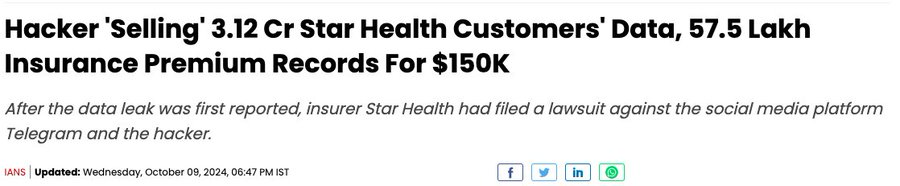
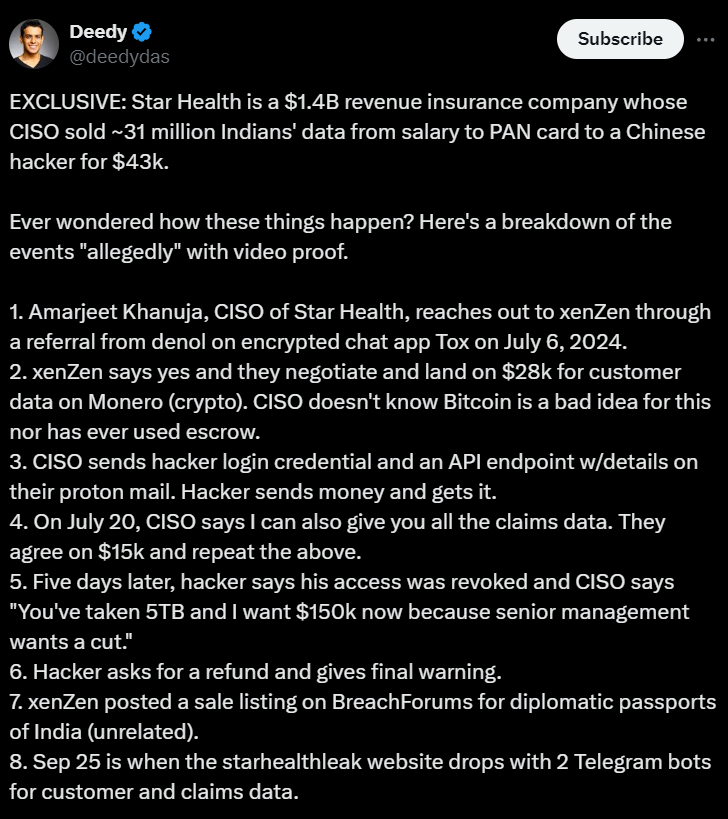
Breaking: Currently taking place in India is one of the biggest hacks ever! For $150k, 31 million row of Star Health Insurance data, including name, DOB, address, phone number, PAN card, and salary for Indians, are being sold. According to hackers He purchased the data from CISO Amarjeet Khanuja. In India, nothing is private.
About the Plot
31 million Star Health customers in India are reportedly affected. Hacker Uses Telegram Chatbots to Leak Dataz`

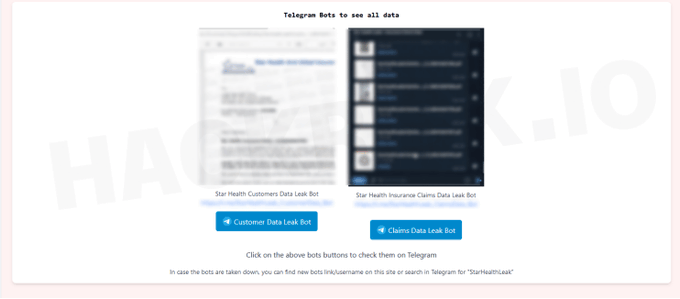
The largest health insurance in India, Star Health, is said to have had 7.24 TB of data compromised by a hacker going by the name xenZen, affecting over 31 million clients.
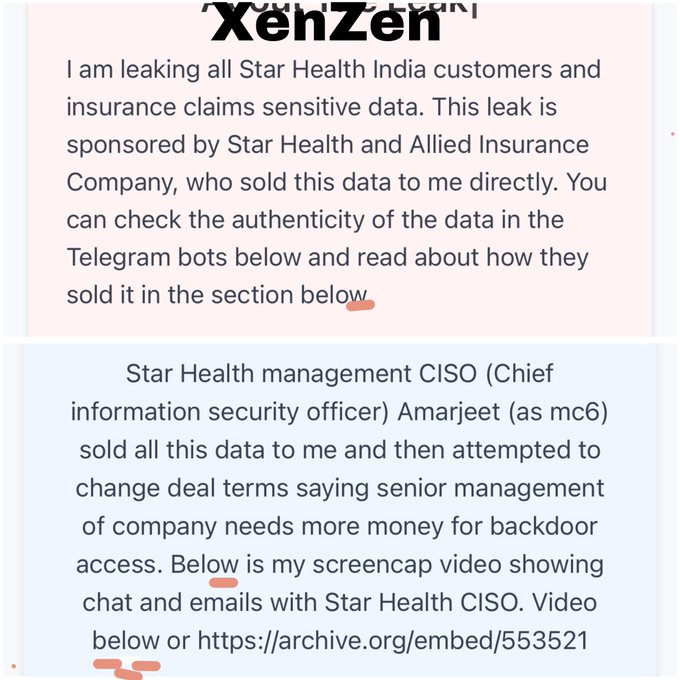
On Telegram chatbots, this data—which includes sensitive personal information, insurance details, and medical records—is offered for free or can be purchased in bulk.
Here is where you may purchase and view a sample of the data: https://starhealthleak.st
Implication Of Leak
The result of such a data breach is:
Financial fraud, identity theft, and targeted scams
— Phishing attempts, account takeovers, extortion, and account hacking
After a brief look, even the free data includes information about the offspring of prominent military figures and Lok Sabha lawmakers who have life-threatening illnesses. This information could be used to blackmail them against India’s interests.
Everything is public, including medical records, prescription drugs, attendees, identification, and personal and private information.
Reporting The Whole Incident
Star Health Insurance Breach: The misguided attempts of a cyber security company to protect its client following a disastrous breakdown in first defence.
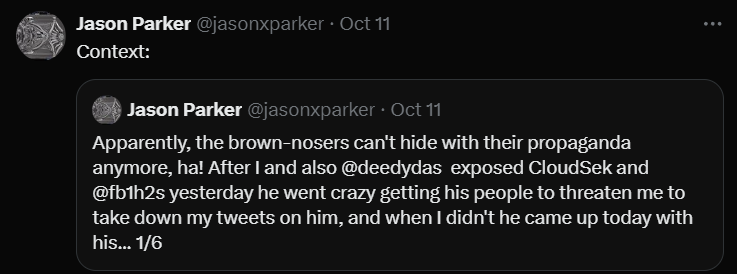
The company, CloudSek of @fb1h2s, released a marketing and cover-up blog post shortly after my tip caused Reuters to report on this breach, which was over a month before the story broke on September 20. After the @Reuters article was published, the threat actor posted the listing on BreachForums.
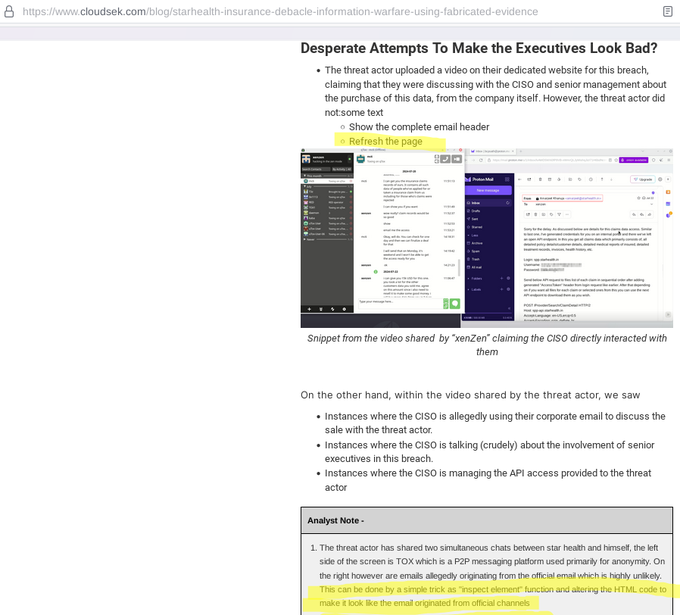
The blog proceeds to ‘analyse,’ if it is even appropriate given what happened in the screen recording video of the threat actor having a conversation with the CISO of Star Health.
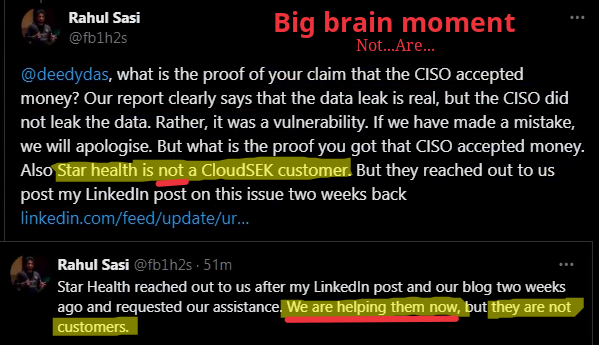
The owner of this claimed cybersecurity organisation, @fb1h2s, then continues to make contradicting claims after learning that Star Health was a client and that this deceptive propaganda is the reason behind their actions.
Cloudsek Founder initiates bounty

We have a 3,13337 INR bounty running for anyone who could give us the identity of xenZen hacker. And here is a new clue – XenZen hacker’s fake twitter handle is @jasonxparker
. The same guy who is pretending to be a UK based researcher and who went to media.
Rahul Sasi declares For us, XenZen, real name Jason Parker, is posing as a British researcher. He is not from the UK, nor is he a native English speaker. Observe also how “below” is used incorrectly repeatedly in both of their phrases. We refer to these as “stylistic habits.”
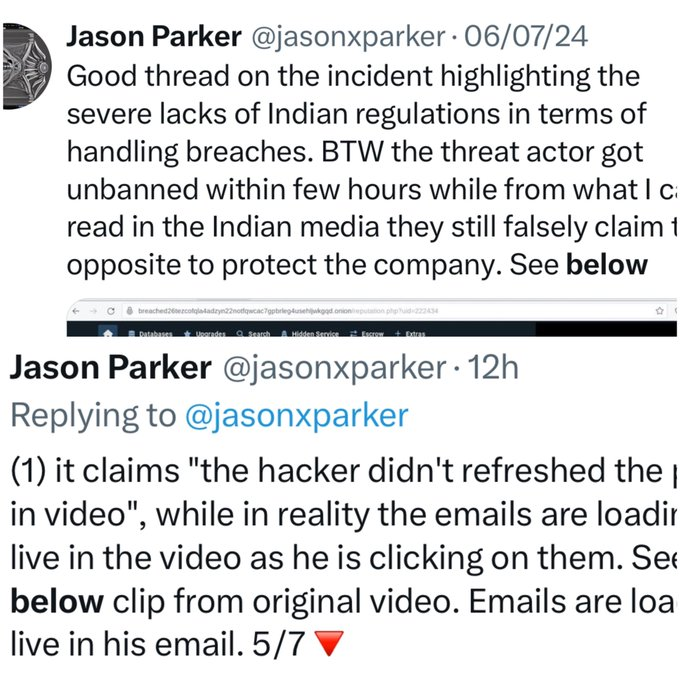
Jason Parker describes himself as a London-based security researcher. He said that he was the one who contacted the media initially after learning about the leak.
Critics point out that Cloudsek is wrong to conclude that Jason Parker is Xenzen.