🚨 Alert for HackingBlogs Readers! 🚨
Hello there to people who landed here. Today we’ll covering specific detail about SuperCardX a latest Malware-as-a-Service (MaaS) for NFC relay fraud that runs on Android. This software, which Cleafy Labs discovered, allows hackers to do contactless payments without physically touching the victim’s card. This is an essential read for anyone interested in financial fraud operations, NFC attacks, or mobile malware. Let us analyse it.
Overview
What’s NFC-Relay Fraud: What’s New ?
The SuperCard X malware is a new type of Android malware that uses a Malware-as-a-Service (MaaS) business model to allow fraud cash-outs via NFC relay attacks. uses a multi-phase strategy that combines NFC data interception, malicious application installation, and social engineering. Because of its targeted functionality, SuperCard X currently has a low detection rate among antivirus programs.
NFC-Relay Fraud
A modern kind of cybercrime known as NFC-Relay Fraud uses Near Field Communication (NFC) technology to get and abuse credit card numbers. Devices like smartphones and contactless cards may communicate data across small distances (typically a few centimeters) thanks to NFC, a wireless communication technology.
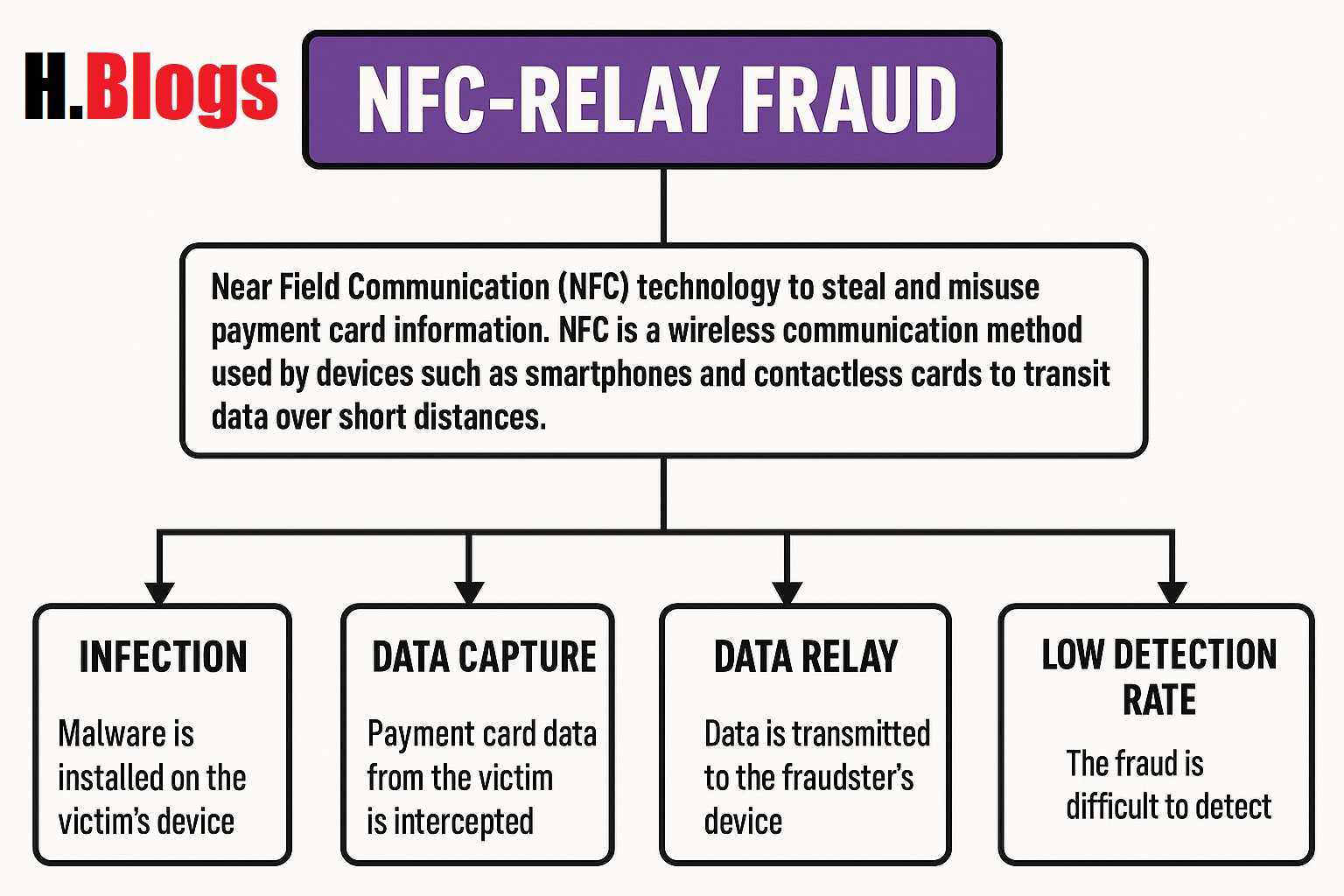
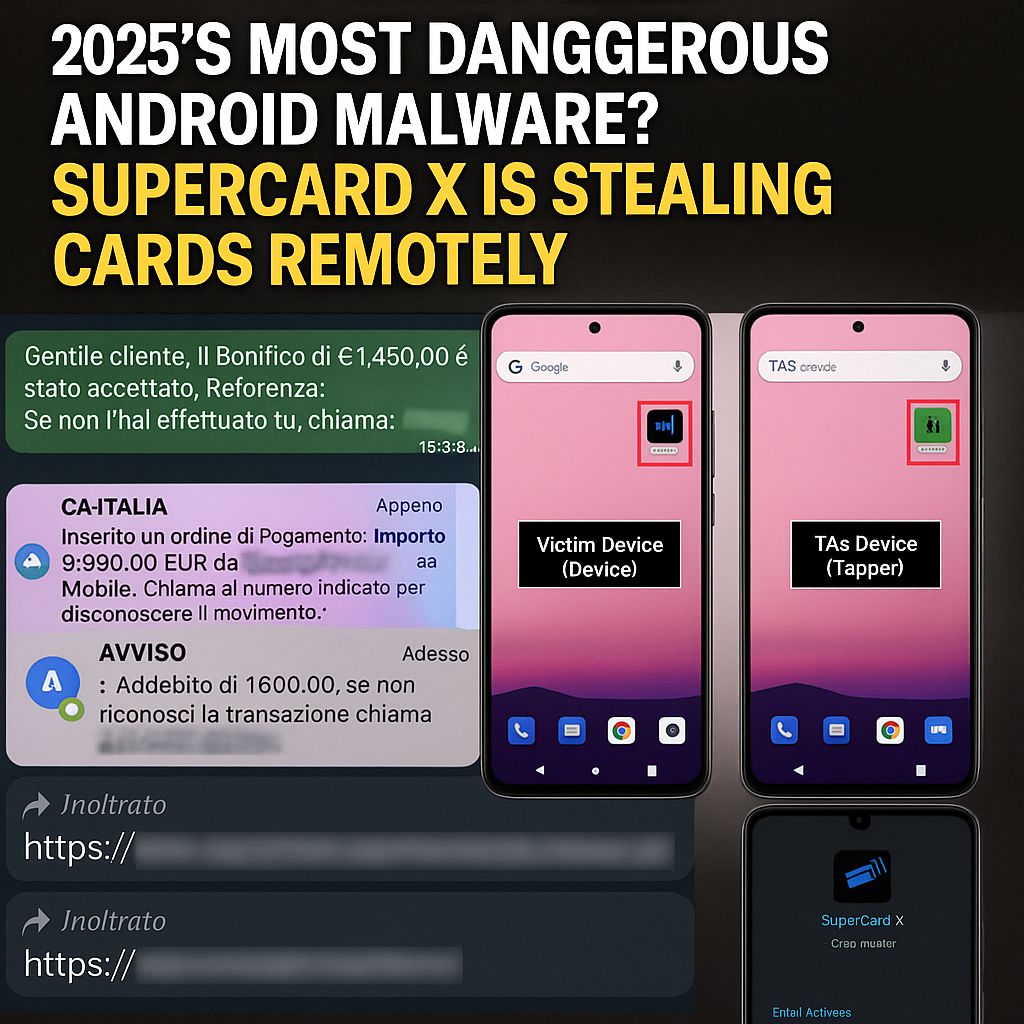
In NFC-relay fraud, attackers, frequently without the victim’s awareness, use malware or specialized tools to intercept and relay NFC signals from a victim’s payment card (such as a credit or debit card) to another device.
The attack makes advantage of a new technique known as NFC-relay fraud, which enables attackers to take out ATM withdrawals and make illegal payments. They accomplish this by eavesdropping on NFC signals from devices that have been compromised. The scam is made possible by the attackers’ manipulation of victims into installing malicious apps on their phones, after which they instruct them to “tap” their credit cards on the compromised device.
Preliminary analysis suggests that TAs are leveraging a Chinese-speaking Malware-as-a-Service (MaaS) platform promoted as SuperCard X. This malware exhibits significant code overlap with the previously documented NGate malware discovered by ESET in 2024.
Said Researchers at cleafy
Steps Used In Persuading The Users And Installing The Softwares On Device: SuperCard X
A carefully planned social engineering attack is the first step in the fraud campaign. The urgent SMS or WhatsApp messages that victims receive frequently pose as bank alerts regarding suspicious transactions. The message asks them to cancel the transaction by calling a certain number. This initiates a Telephone-Oriented Attack Delivery (TOAD) scenario, in which the attacker uses phone calls to manipulate the victim.


Attackers use manipulation during the call to obtain the victim’s credit card information in a number of ways:
- PIN Request: By taking advantage of the victim’s anxiety over fraud, the attackers persuade them to “reset” or “verify” their card information. To locate the PIN, they walk them through their banking app.
- Removing Card restrictions: The attackers tell the victim to remove any spending restrictions on their card to facilitate money withdrawals after they have earned their trust and perhaps access to their banking app.
- Installing Malicious software: To enable NFC-relay fraud, the attackers mislead the victim into installing fake security or verification software that secretly hosts the SuperCard X malware.
In the last phase, the attackers tell the victim to place their credit or debit card near the compromised phone. Through NFC, the SuperCard X malware secretly obtains the card information and transmits it to a second device under the attackers’ control.
The attackers use the second device to carry out illegal operations, including contactless retail payments or, worse, cash withdrawals from ATMs, using the stolen card information.

It is important to emphasize the impact of this threat, as it no longer fits within the traditional fraud paradigm where the targets were customers of a specific bank. On the contrary, the operational context of this attack is mainly agnostic of the financial institution involved since the ultimate target of the fraudsters is the customers’ debit or credit cards, regardless of the issuing bank.
Said Cleafy
SuperCardX Architecture
The latest malware, SuperCard X, is made to carry out NFC relay fraud and functions similarly to NGate and NFCGate. NFC technology, which is used for contactless card payments, is exploited by these kinds of malware. Two applications are used by the malware: “Reader” and “Tapper.”
- The “Reader” app: This program, which is installed on the victim’s phone, uses NFC to get information from the victim’s credit card.
- Installed on the attacker’s device, the “Tapper” software uses the card information that has been taken to conduct fraud purchases.
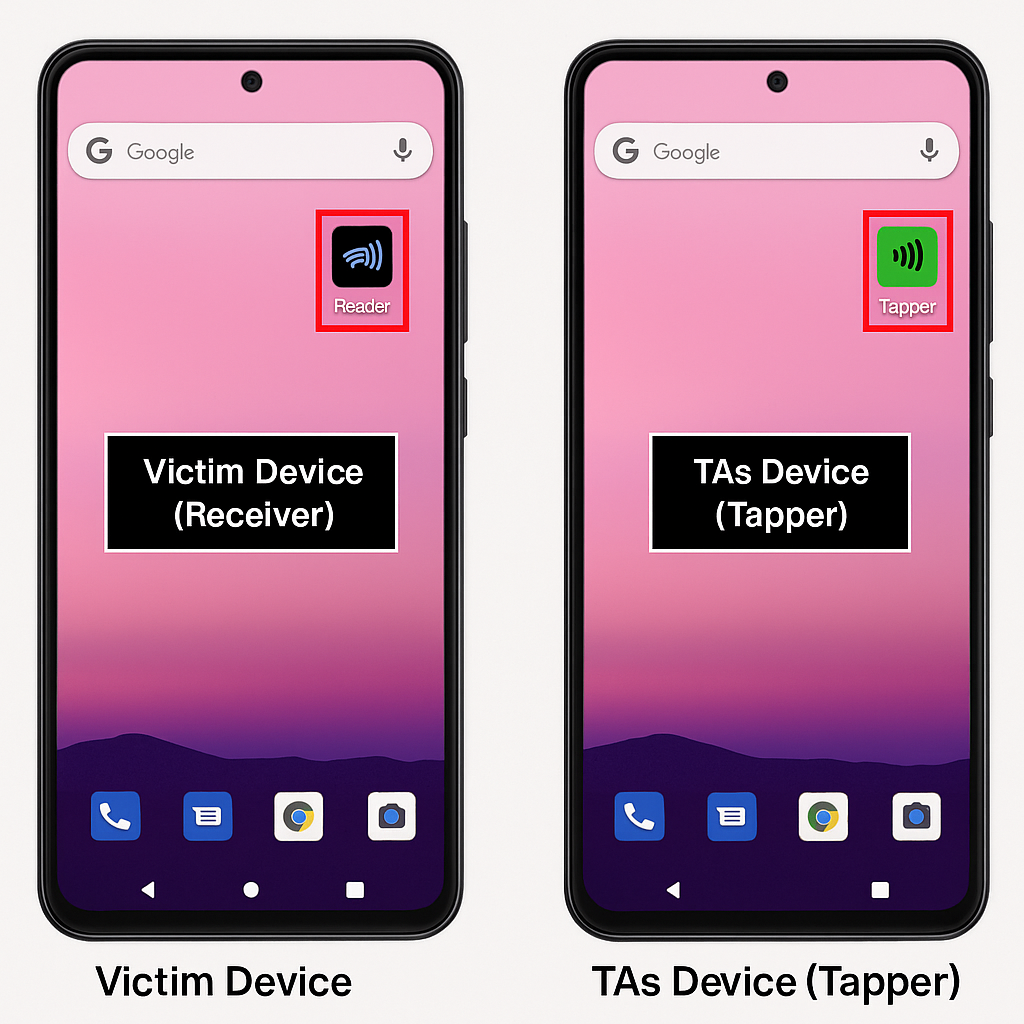
By connecting to a central server (Command and Control, or C2) under the attackers’ control, the apps exchange information with one another over the internet. Real-time relaying of the stolen NFC data is aided by this server.
The attackers instruct the victim to log into the “Reader” app in order for this to function. Following the gathering of card data, the app simulates the genuine card and makes it look authentic to point-of-sale systems or automated teller machines (ATMs) by using a unique message format known as ATR (Answer To Reset).

The important thing is that this technique enables the attacker to do illicit activities remotely by avoiding the requirement that they be physically close to the card. To make the relay attack smooth and invisible to the victim, the “Reader” software saves these ATR messages.
Low Detection Rate
The simplicity with which SuperCard X evades detection by antivirus (AV) software is among its most dangerous characteristics. According to a number from the research, the majority of security tools were unable to identify it when tested.
This occurs because, unlike other financial viruses, SuperCard X is highly focused and does not request a lot of rights. SuperCard X keeps things simple, unlike most Android banking trojans that request a lot of dangerous permissions, such as reading your texts, taking over your phone, or displaying fake screens.
It just requests a few standard permissions that do not raise any red lights, such as access to NFC, which is necessary to read contactless cards. Its small setup allows it to remain undetected while still carrying out its primary function, which is card data theft via NFC.
Malware samples:
| Hash | App name |
|---|---|
| 2c6b914f9e27482152f704d3baea6c8030da859c9f5807be4e615680f93563a0 | Verifica Carta |
| 3f39044c146a9068d1a125e1fe7ffc3f2e029593b75610ef24611aadc0dec2de | SuperCard X |
| 3fb91010b9b7bfc84cd0c1421df0c8c3017b5ecf26f2e7dadfe611f2a834330c | KingCard NFC |
C2 servers:
| Domains |
|---|
| api.kingcardnfc[.]com |
| api.kingnfc[.]com |
| api.payforce-x[.]com |


