Experts at Doctor Web have discovered a Linux variant of the well-known TgRat Trojan, which is employed in focused computer attacks. This Trojan’s ability to be managed by a Telegram bot is one of its noteworthy characteristics.
Positive Technologies Expert Security Centre (PT ESC) found a hacking toolkit that utilised the Telegram chat service to control backdoors during an examination. Attackers employed network traffic tunnelling tools in addition to well-known malware like Impacket and Mimikatz to enter the network and move laterally inside it.
2022 saw the discovery of the TgRat Trojan, which was first built for Windows. It was a little malicious programme made to extract data from a particular hacked system. Not so long ago, its Linux-compatible twin was found by malware specialists at Doctor Web.This virus is classified as a remote access trojan (RAT).

Dr. Web lab got a request for an inquiry into an information security issue from a hosting firm. On one of the clients’ servers, a suspicious file was found by Dr. Web antivirus. It was discovered to be a Trojan dropper—a software intended to infect the targeted machine with malware. The Linux.BackDoor was unloaded by this dropper.TgRat.2 Trojan entering the network.
Mechanism the spyware follows
This Trojan was likewise designed to target certain machines; upon startup, it compares the machine name’s hash with a string that is encoded within the Trojan’s body. The TgRat procedure ends if the values are not the same. If the Trojan is launched successfully, it establishes a network connection and employs a peculiar method of communication with its control server, a Telegram bot.
TgRat github repository

https://github.com/infermiere/tg-rat.git Has the necessary assets that will help you use the bot. Following are the features it offer

TgRat Dropper Operations
The dropper’s initial step involves verifying the inputs (parameters) provided in its launch, which has an effect on the intermediate persistence stage. Add_payload (named after the method that does it) is the first stage if there are input parameters. Initialization and persistence happen if there are not any. So the dropper.
- uses the “-install=false” option to install itself at startup (Figure 1).
- creates the file name containing the payload by parsing the path and the name of the running process, changing the path, and then adding the payload name contained inside the code.
- uses the AES algorithm in CTR mode to decrypt the binary data present in the programme body (the initialization vector is incorporated in the programme body).
- gives the payload control and writes the decrypted data to the file.

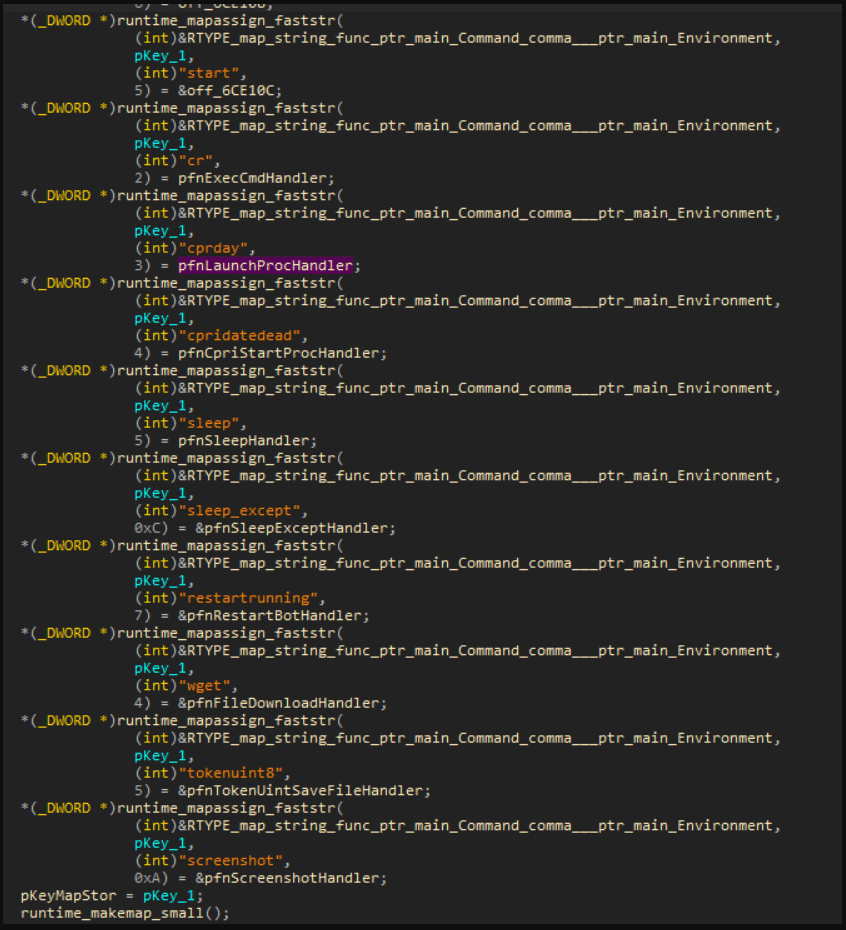
It was much simpler to determine the kinds of instructions that the virus performed after analysing the initialization code of the structure that included the addresses of functions and their names. These commands included:
- Getting the details of the compromised computer
- Binding to a certain Telegram conversation; connection failure message
- Self-destruction (eliminate )
- Destroy yourself (get rid of )
- Auto-updating Shell debut
- running the script in the shell and storing the outcome in a file
- Commencing a procedure
- Rest at a specific time of day.
- Bot restart
- Downloading the file
- capturing a picture of

Utilising The tool
The Telegram bot is linked to a closed group on the messenger that controls the Trojan. Through the messenger, attackers may instruct the Trojan to accomplish tasks including downloading data from a compromised machine, taking screenshots, executing instructions remotely, or downloading files through attachments.
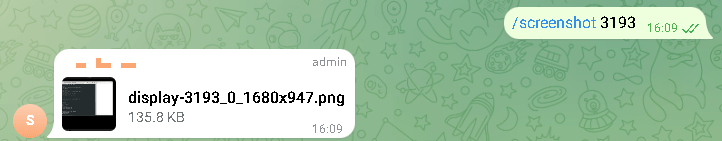
In contrast to its Windows equivalent, this Trojan’s code was encrypted using the RSA cypher and instructions were carried out using the bash interpreter, enabling the execution of whole scripts inside a single message. Because the Trojan had unique identifiers for each instance, attackers could connect all of the bots to a single chat and provide commands to each one.
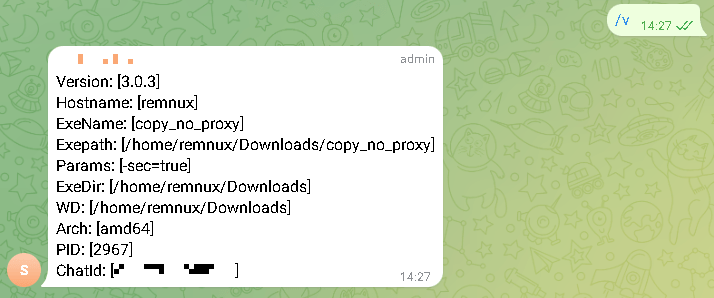
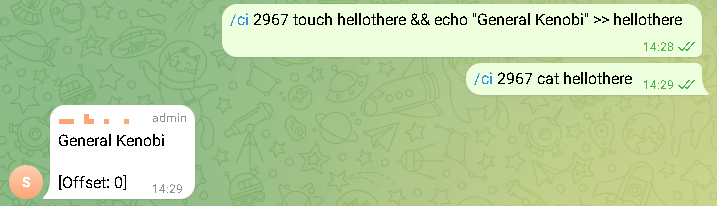
Even though the Trojan and control server’s chosen method of connection is unique, this attack may be identified by closely examining network traffic. Data interchange with Telegram servers is common for user PCs, but not for a server connected to a local network.


