Summary
- A wealth of employee data was accidentally exposed and made public by the UK-based temporary employment company GigtoGig.
- 217,000 sensitive files were in the database, which was accessible to anybody without requiring a username or password because it was made public.
- Criminals can easily create false identities using leaked or stolen passport copies, which they can then use to apply for loans and carry out other fraudulent operations.
As Per the Research By Cybernews they said Tens of thousands of gig workers are at risk of identity theft and other scams due to the passports of these individuals being compromised by the UK hiring business Gigtogig. GigtoGig states that it collaborates with well-known companies like G4S, Hilton, Sainsbury’s, and Marriott.
Businesses can find workers for short-term projects through GigtoGig and similar sites, which also offer workers a variety of job options, payroll services, and insurance.
Gigtogig Misconfigured Amazon Bucket
On August 5th, during a routine investigation, there research team discovered a misconfigured Amazon AWS S3 bucket, which they managed to attribute to GigtoGig. Unfortunately, the database, which contained 217,000 sensitive files, was exposed to the public, meaning that anyone could access it without having to enter a username and password.

Risk Of Data Exposure
Criminals can easily create false identities using leaked or stolen passport copies, which they can then use to apply for loans and carry out other illegal operations.
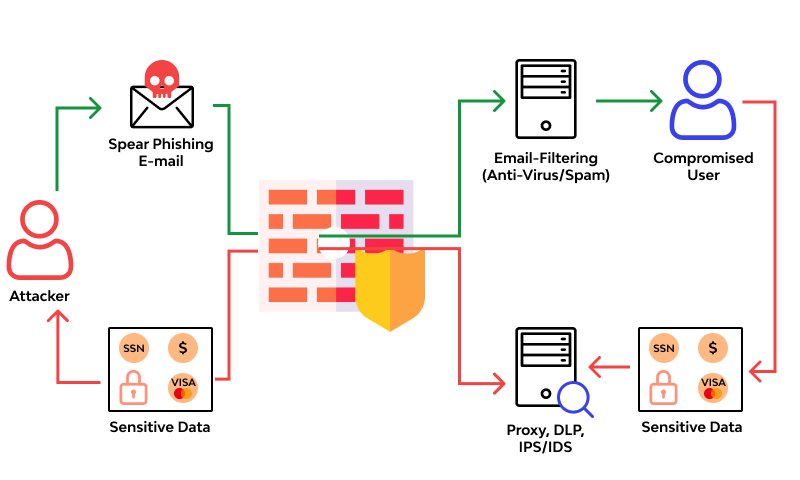
Gig workers may also be vulnerable to highly targeted phishing attacks, in which hackers pretend to be government authorities or employers in order to trick their victims.
For attackers, exposed CVs are also a very useful tool because they can be used to create phishing emails that look real.
“Scammers might impersonate trusted entities to extract more sensitive information or money from the applicants,”
Cybernews researchers said
Asking for addtional information (private) making false assumption like the following : Attackers who obtain phone numbers and other personally identifiable information (PII) may act as recruiters or employers and state that the application was not processed correctly or that further information is required. They could request more private information or money in exchange for background check services.
Mitigation Of Such Data Exposure
As Per Cybernews the following mitigation plan has been released
Reduction for businesses’ image
To secure the bucket and limit public access, modify the access settings.
- Modify permissions to guarantee that only services or users with permission have the required access
- Examine access logs in the past to see if unauthorised actors have accessed the bucket.
- Turn on server-side encryption to safeguard data when it is not in use. 3. Image 4.
- To securely maintain encryption keys, use AWS Key Management Service (KMS).
- Enable secure communication for data in transit by implementing SSL/TLS.
- Think about putting security best practices into effect, such as personnel training, automated security checks, and frequent audits.


