Greetings, my dear hacker family. As you are aware, hackers like us are constantly improving their methods of evading security measures. We have developed a new method to take advantage of systems. This method was recently used to hack a Windows system, and the worst part is that it is simple to set up but invisible to the naked eye. It is also very easy to understand and avoid these loophole traps, so let others know about it.
Since the technique uses a lot of compression and zip-making tools, let us first take a look at how zip files are structured, how they handle data, and how hackers use this technology to compromise systems.
What is Zip ? Understanding Zip File Structuring
To be absolutely precise and concise on this simple subject, I would explain that zip is a format that is frequently used to compress and bundle several files into one. It is crucial for lowering file sizes and simplifying transfers. Its structural flexibility also makes it an ideal delivery method for evasive viruses.
Zip File Structures
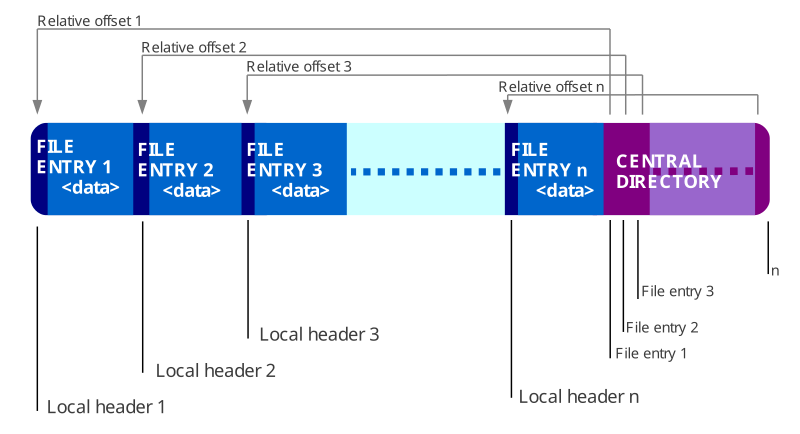
- File Entries
- Central Directory
- EOCD (End of Central Directory):
The actual files or folders that are compressed inside the ZIP file are called file entries. Metadata like the file name, size, and modification date are included in every entry.
At the conclusion of the ZIP file is the Central Directory, which serves as an index for the entire archive. ZIP readers can easily find and extract files without having to sequentially scan the entire ZIP by using this list, which contains all of the file entries and their offsets inside the archive.
End of Central Directory, or EOCD, is a record that indicates the end of the central directory and includes important metadata including the total number of file entries and the directory’s beginning position.
Now that we know the fundamentals of the zip structure, let us learn about some of the most widely used zip archive readers. It will be crucial in the future, but keep in mind that each of these handles concatenation differently. Oh, you have no idea what that is. Continue reading.
Popular Zip Archive Readers : Winrar, 7zip, Windows File Explorer

Open-source 7zip has a wide range of file formats, effective compression, and comprehensive command-line options that developers, cybersecurity experts, and vendors employ.

Winrar is dependable, compatible with a variety of file types, has sophisticated error-recovery capabilities, and is intended for both home and business customers that require extensive archiving capabilities.

Windows File Explorer is a feature that comes with Windows OS that allows for easy ZIP handling and does not require any additional applications.
Let us move on to the good work and discuss how zip concatenation is done and how you may perform it in your own system.
Zip concatenation : The Final Boss
Before we discuss anything more, let us examine the inputs and outputs of a few Linux commands before drawing any conclusions.
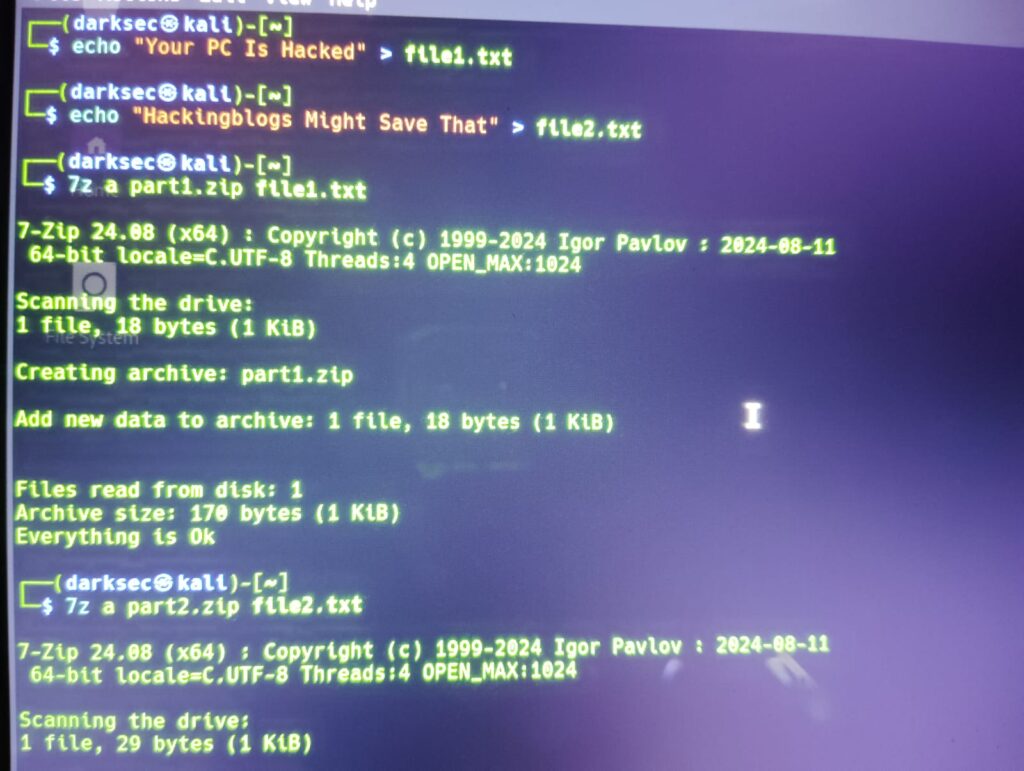

Commands Used
┌──(darksec㉿kali)-[~]
└─$ echo "Your PC Is Hacked" > file1.txt
┌──(darksec㉿kali)-[~]
└─$ echo "Hackingblogs Might Save That" > file2.txt
┌──(darksec㉿kali)-[~]
└─$ 7z a part1.zip file1.txt
7-Zip 24.08 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-08-11
64-bit locale=C.UTF-8 Threads:4 OPEN_MAX:1024
Scanning the drive:
1 file, 18 bytes (1 KiB)
Creating archive: part1.zip
Add new data to archive: 1 file, 18 bytes (1 KiB)
Files read from disk: 1
Archive size: 170 bytes (1 KiB)
Everything is Ok
┌──(darksec㉿kali)-[~]
└─$ 7z a part2.zip file2.txt
7-Zip 24.08 (x64) : Copyright (c) 1999-2024 Igor Pavlov : 2024-08-11
64-bit locale=C.UTF-8 Threads:4 OPEN_MAX:1024
Scanning the drive:
1 file, 29 bytes (1 KiB)
Creating archive: part2.zip
Add new data to archive: 1 file, 29 bytes (1 KiB)
Files read from disk: 1
Archive size: 181 bytes (1 KiB)
Everything is Ok
┌──(darksec㉿kali)-[~]
└─$ cat part1.zip part2.zip > combined_Part3.zipWhat I Did ?
To explain what I did, I first created two distinct text files and gave them names. Next, I used 7zip on my Linux computer to produce two more Zip files. Finally, I cat the contents of these two files and assigned these outputs to a new combined.zip file. It seems simple. The good part will arrive soon.
Analysing the Output file
Let us start by assuming that, logically, if two files are being combined into one zip file, the resultant zip file should contain both files, correct? That is incorrect because 7zip only displays one file and hides the others. However, did you know that this file will also be extracted during the extraction process? That is the risky part, and you will not be able to identify it. Check it out here.

It is easy to ignore a warning that says, “There are some data following the conclusion of the archive.”This strategy takes use of the various behaviours of ZIP readers, including those frequently employed by human malware researchers and well-known cybersecurity technologies. To analyse ZIP files for additional analysis, several security firms use well-known ZIP handlers like 7zip or OS-native tools.
Threat actors are aware that these tools frequently fail to identify or ignore harmful content concealed in concatenated archives, which enables them to target users who use a particular programme to work with archives and deliver their payload unnoticed.


