Hackingblogs: A security researcher discovered DOS(Denial Of Service ) bug in the widely used Facebook Messenger for iOS version 477.0.0. He used emojis to identify his bugs, which is fascinating as I discuss it. Let us go into the article and I will attempt to make it clear to you how he discovered this flaw.

About Facebook Messenger For those who have never heard about it

Facebook created the well-known chat program Facebook Messenger. Users can share images and videos with people or groups, send text messages, and make voice and video conversations. Users may send messages to friends and family straight from the Facebook app thanks to Messenger’s integration with Facebook.
Facebook Messenger is one of the most popular messaging programs in the world, with over a billion users, offering a practical and effective means of communication.
Ever Though, How are these emojis being transferred ?
The researcher first asks the most fundamental yet crucial query: how are the emojis being sent from the sender to the recipient? He then uses JADX to reverse engineer the messenger apk and uses Frida to do a dynamic investigation, which gives the following important findings.
Classes Used
com.facebook.rsys.reactions.gen.SendEmojiInputModel
com.facebook.rsys.reactions.gen.ReactionsApi$CProxyTo extract the emoji values, he writes a custom python script that intercepts code calls to the specified functions. His official article contains the custom script.
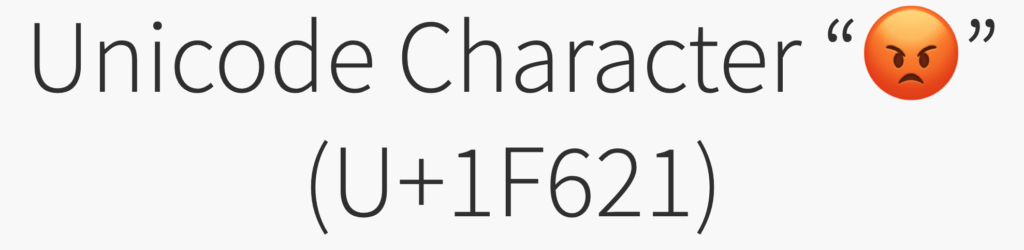
When he executes his programmes on the execution of this poc, he finds that the data being transmitted to the receiver is a string that contains an emoji in hexadecimal.
(env) dev@Mac-mini emoji % python3 emoji_poc.py
[+] Found SendEmojiInputModel Class - continue to send Emoji reaction.
[+] Sending emoji reaction with value: '1f621'
What If A String Is Sent which has no emojis assigned with it
His second most crucial query is: What would happen if we sent a string without a string attached to it? He accomplishes this by altering the Frida script to transform the string to a value that does not match any recognised emoji, like de25 (F_fe0fACE_WITH_COLON_THREE).
Then, in the previously displayed script, he adds the following lines above the this “sendEmoji” function, which substitutes an invalid input for the emoji.
var payload = 'de25';
emoji.emojiId.value = payload;
The video demonstrates how delivering an invalid string that does not look like an emoji causes the iOS participant’s Messenger app to crash.
Log File
*** Terminating app due to uncaught exception 'NSInvalidArgumentException', reason: '-[__NSCFString appendString:]: nil argument'
*** First throw call stack:
(0x180d07d0c 0x1984f8ee4 0x180e026a8 0x180da4374 0x180c90eb8 0x11cfcd628 0x103cd8c34 0x11d03de54 0x11c191b08 0x11b91b428 0x11b935708 0x11b93e6a4 0x11b93e5e4 0x180cb2988 0x180ce61a8 0x11b93dd6c 0x11b91c4b0 0x11b920e18 0x11b920de8 0x1026f2910 0x1026f28c4 0x1823f5cc8 0x180cb382c 0x180c84a64 0x180c7fec4 0x180c93240 0x1a1763988 0x18349341c 0x18322cb88 0x102248590 0x1024743d0)
He included a thorough fundamental analysis of the issue that arose, which I will include here if you wish to go deeper. These kinds of bugs demonstrate the importance of asking sensitive, yet logical, questions to test an application since the tester has an unique perspective, which is necessary for a knowledgeable hacker. I will see you in the next article. That concludes today’s article.


