
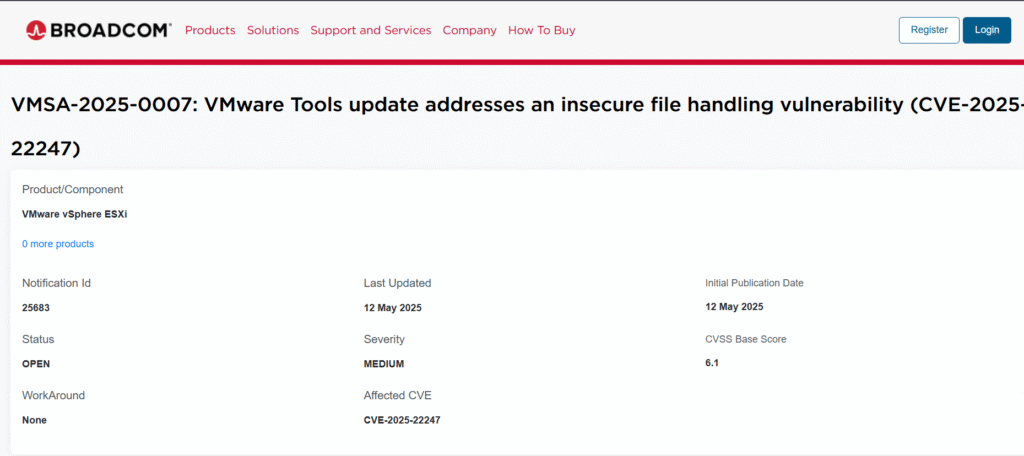
Hello There Hackingblogs readers. In a recent security alert, Broadcom-owned VMware disclosed a moderate-severity vulnerability in its VMware Tools software, which is crucial for optimizing and maintaining virtual machines (VMs) on platforms such as ESXi. The vulnerability, identified as VMware Tools CVE-2025-22247 Vulnerability, allows hackers with limited access privileges to tamper with files inside guest VMs, resulting in insecure file operations.
This newly reported vulnerability primarily targets Windows and Linux virtual machines, leaving macOS computers unharmed.
VMware Tools CVE-2025-22247 Vulnerability: What’s the Issue?

Broadcom said that the weakness is in the way VMware Tools processes local files within guest virtual machines. If an attacker acquires non-administrative access to a VM, they can modify local files and perform insecure file operations. This vulnerability, however moderate on the CVSS scale (6.1), can have a major impact in multi-user situations and cloud infrastructure configurations.
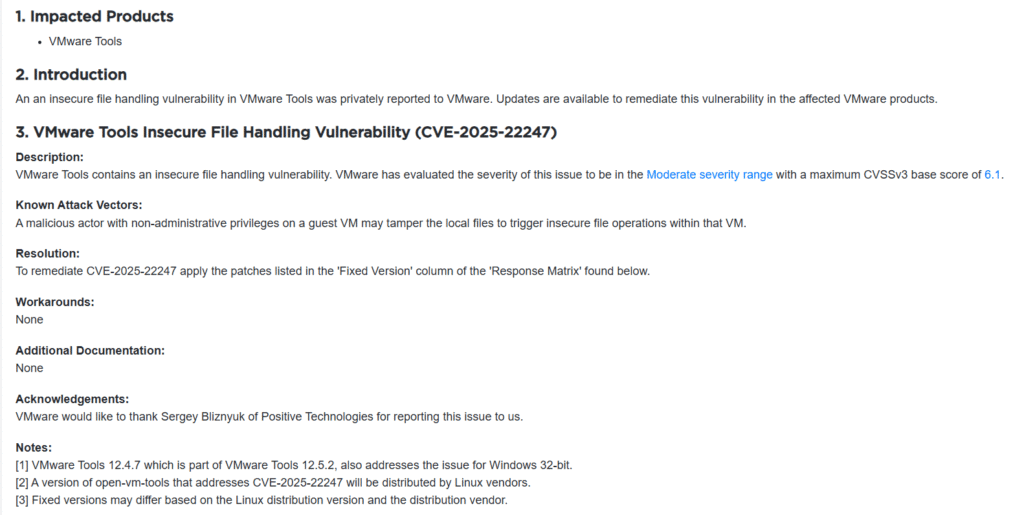
“A malicious actor with non-administrative privileges on a guest VM may tamper the local files to trigger insecure file operations within that VM.” – Broadcom Security Advisory
Sergey Bliznyuk, a security researcher from Positive Technologies, responsibly revealed the vulnerability to VMware, ensuring that a patch was in place before public exposure.
Key Highlights
- Vulnerability ID: CVE-2025-22247
- Severity Level: Moderate
- CVSSv3 Score: 6.1
- Attack Vector: Local access to guest VM
- Impact: High integrity impact, low confidentiality impact
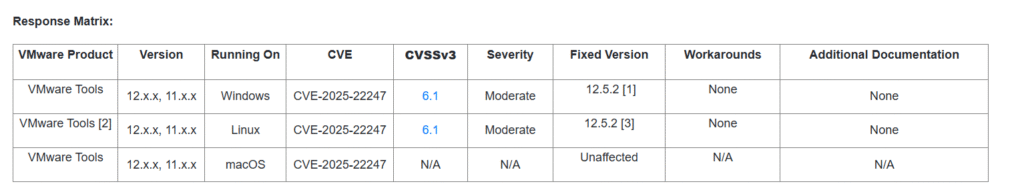
- Affected OS: Windows and Linux (VMware Tools 11.x.x and 12.x.x)
- macOS: Unaffected
- Patch Available: Yes (VMware Tools version 12.5.2)
Who Is at Risk?
The primary targets are organizations that use VMware-based servers, especially those in business and cloud environments. This includes:
- Data centers featuring multi-tenant virtual environments
- DevOps or IT teams use Windows/Linux-based guest VMs.
- Businesses rely on automated CI/CD handles within virtual environments.
Even while the issue does not allow attackers to escape the VM or compromise the hypervisor, it might be utilized as part of a bigger attack chain, potentially resulting in privilege escalation or internal VM tampering.
Patch Details: How to Stay Safe
VMware has released VMware Tools version 12.5.2 to remedy the problem. The patch is especially available for Windows 32-bit users in version 12.4.7 (part of 12.5.2).
For Linux systems:
The affected versions are open-vm-tools 11.x.x and 12.x.x.
Patches will be issued via various Linux suppliers (such as Ubuntu and Red Hat).
Specific patch files:
CVE-2025-22247-1230-1250-VGAuth-updates.patch (versions 12.5.0–12.3.0)CVE-2025-22247-1100-1225-VGAuth-updates.patch (versions 12.2.5–11.0.0)
How to manually apply patches in Linux environments:
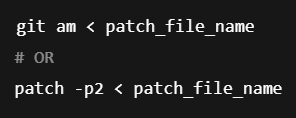
The CVE-2025-22247 vulnerability is simply another warning that non-hypervisor tools, such as VMware Tools, can become attack vectors. Although the issue requires local access, it allows for potentially harmful intrusion in shared virtual machine setups.


