Please be advised, VMware users who follow hackingblogs, that serious vulnerabilities have been found in both VMware vCenter Server and VMware Cloud Foundation. We will talk about these two vulnerabilities in a moment. They are the VMware vCenter Server heap-overflow vulnerability and the VMware vCenter privilege escalation issue.
The severity score for this serious vulnerabilities is 9.8 out of 10, while the other has This vulnerability has a high level of severity (7.5 out of 10).
These vulnerabilities are being used by hackers to remotely code and totally compromise the systems. Additionally, hackers can use a specially constructed network packet to elevate privileges to root.
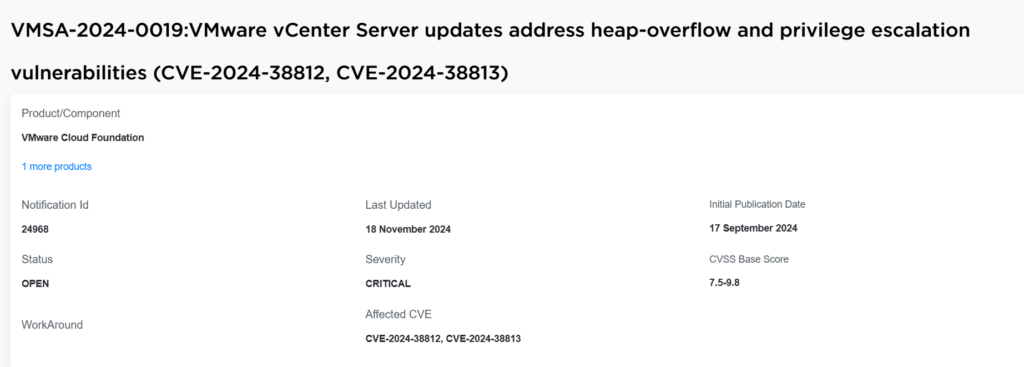
VMware by Broadcom has determined that the vCenter patches released on September 17, 2024 did not fully address CVE-2024-38812. All customers are strongly encouraged to apply the patches currently listed in the Response Matrix. Additionally, patches for 8.0 U2 line are also available.
Broadcom Said In An Article
The compromised assets in this bug are VMware Cloud Foundation and VMware vCenter Server.
What Is Vcenter Server ?
Making folks comfortable with the program we will be working with is important before they understand what its flaws are. To put it simply, vCenter is a platform for central management of VMware virtual environments. Administrators may manage and keep an eye on numerous VMware vSphere hosts, clusters, and virtual machines from a single interface with the help of this control panel-like tool.
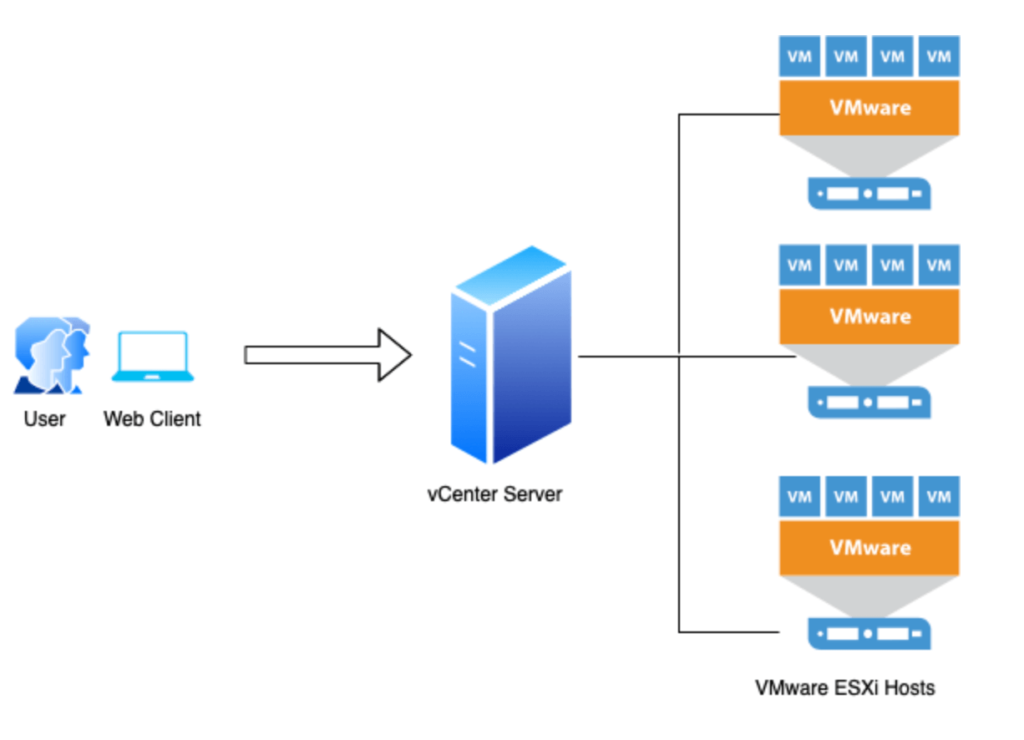
Deploying, managing, and troubleshooting virtual machines and data centres is made simpler by vCenter’s features, which include resource allocation, performance monitoring, and security management. Consider it your “brain” for managing and improving your virtual infrastructure.
VMware vCenter Server heap-overflow vulnerability (CVE-2024-38812)
Alright, let us discuss this issue, which primarily affects vCenter Server. Here, the DCERPC protocol implementation on the server has a heap-overflow vulnerability.

An application may crash, become unstable, or run malicious code as a result of an attacker executing a heap overflow attack to write data past the end of a heap buffer. Because heap overflows can result in data corruption and uncontrolled code execution, they pose a major security risk.
Networked computers can communicate with one another using the Distributed Computing Environment/Remote Procedure Call (DCE/RPC) protocol. It enables processes to invoke functions or processes on distant systems just like they would on their own. Database access, file sharing, and authentication are just a few of the uses for DCE/RPC.
To fix CVE-2024-38812 and fix the bug in your software, apply the updates indicated in the ‘Fixed Version’ column of the ‘Response Matrix’ below to the deployments that are impacted.
VMware vCenter privilege escalation vulnerability (CVE-2024-38813)
The second weakness found was the VMware vCenter privilege escalation vulnerability, which allows a hacker to get access to vCenter Server and use it to deliver a specially constructed network packet that elevates rights to root. By taking advantage of security flaws, a threat actor in this type of attack obtains elevated access and administrative rights to a system.
| VMware Product | Version | Running On | CVE | CVSSv3 | Severity | Fixed Version | Workarounds | Additional Documentation |
| VMware vCenter Server | 8.0 | Any | CVE-2024-38812, CVE-2024-38813 | 9.8, 7.5 | Critical | 8.0 U3d [1] | None | FAQ |
| VMware vCenter Server | 8.0 | Any | CVE-2024-38812, CVE-2024-38813 | 9.8, 7.5 | Critical | 8.0 U2e | None | FAQ |
| VMware vCenter Server | 7.0 | Any | CVE-2024-38812, CVE-2024-38813 | 9.8, 7.5 | Critical | 7.0 U3t [1] | None | FAQ |
| VMware Cloud Foundation | 5.x | Any | CVE-2024-38812, CVE-2024-38813 | 9.8, 7.5 | Critical | Async patch to 8.0 U3d [1] | None | Async Patching Guide: KB88287 |
| VMware Cloud Foundation | 5.1.x | Any | CVE-2024-38812, CVE-2024-38813 | 9.8, 7.5 | Critical | Async patch to 8.0 U2e | None | Async Patching Guide: KB88287 |
| VMware Cloud Foundation | 4.x | Any | CVE-2024-38812, CVE-2024-38813 | 9.8, 7.5 | Critical | Async patch to 7.0 U3t [1] | None | Async Patching Guide: KB88287 |



