Alert: Customers were alerted by Acronis to patch a serious Cyber Infrastructure security a defect that allows attackers to use default credentials to bypass authentication on affected servers.
Acronis Cyber Infrastructure (ACI) is a single, multi-tenant platform for virtualisation, backup, and remote endpoint management for cyber security. Furthermore, enterprise backup data is safely stored and disaster recovery activities can be executed on it.

A strict deadline has been set for US federal agencies to address the issue.
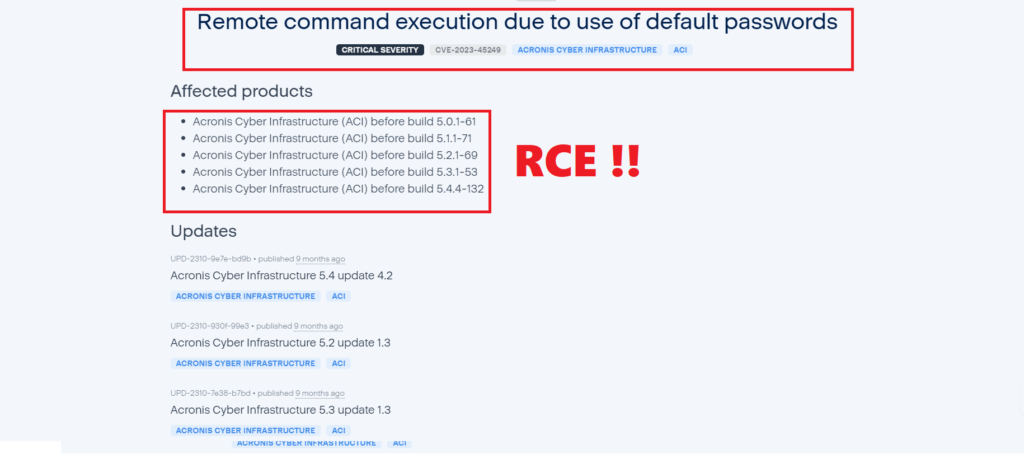
The vulnerability, which is linked to the usage of common passwords and is known as CVE-2023-45249, has been rated 9.8 on the CVSS scale. It permits remote code execution.

The following versions of ACI are impacted by the issue:
- versions up to 5.0.1-61;
- versions up to 5.1.1-71;
- versions up to 5.2.1-69;
- versions up to 5.3.1-53;
- versions up to 5.4.4-132.

Description
This update contains fixes for 1 ctitical severity security vulnerability and should be installed immediately by all users.
This vulnerability is known to be exploited in the wild.

“All users should apply this update immediately as it fixes a security issue with a critical severity.” reads the company-published advice. “There is evidence that this vulnerability is exploited in the wild.”
The vulnerability (recorded as CVE-2023-45249) can be used by unauthenticated attackers in low-complexity attacks to obtain remote code execution on unpatched ACI servers without requiring user input.
You can find the build number of Acronis Cyber Infrastructure by opening the Help -> About dialogue box from the program’s main window and using it to determine whether your servers are vulnerable.
To update ACI to the latest available build, you have to:
- Log in to your account (you can create one and register your licenses using these instructions).
- Download the latest ACI build in the “Products” section and install it on vulnerable servers.
“CVE-2023-45249 pertains to remote command execution vulnerability due to the use of default passwords. The Acronis security team has conducted a thorough analysis and assessed the critical risk level.
We have already implemented a patch to address this issue; the patch has been released and deployed. We have advised customers to upgrade to the latest version of Acronis Cyber Infrastructure (ACI) in order to fix the vulnerability.
The patch and fix were made available 9 months ago when the vulnerability was first detected. Customers should follow patch protocols posted here: https://security-advisory.acronis.com/advisories/SEC-6452.”
Said Acronis


